Improve Government Efficiency & Bolster Security
Protect sensitive information with powerful monitoring while improving operational efficiency, streamlining workflows, and maximizing resource utilization—all within a platform designed to meet federal security and compliance requirements.
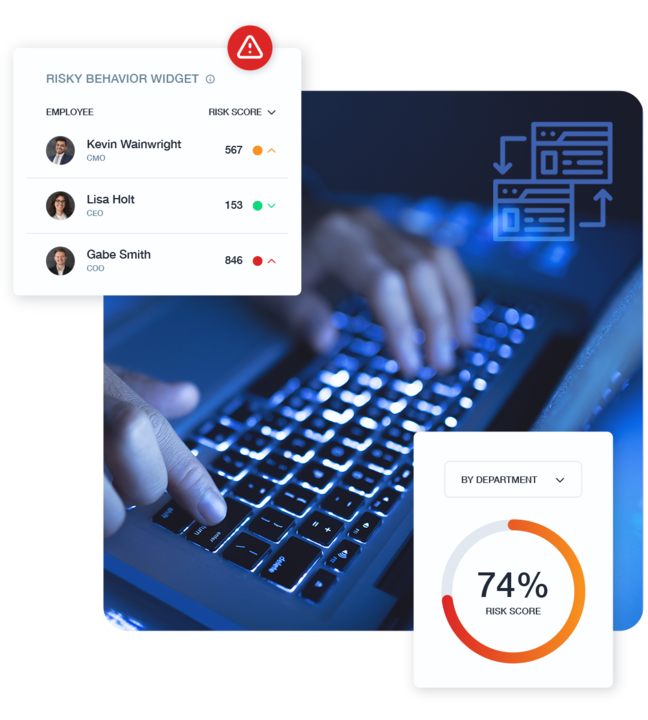

Why Government Agencies Choose Teramind
- Workforce Analytics: Uncover the hidden patterns in productivity trends that lead to actionable improvements.
- Resource Optimization: Ensure that every team and technology resource is utilized to its fullest potential.
- Process Improvement: Streamline workflows and create smoother processes that empower your teams to deliver their best work.
- Performance Management: Move beyond subjective evaluations and embrace an evidence-based approach. Recognize high achievers and provide valuable coaching to all employees.
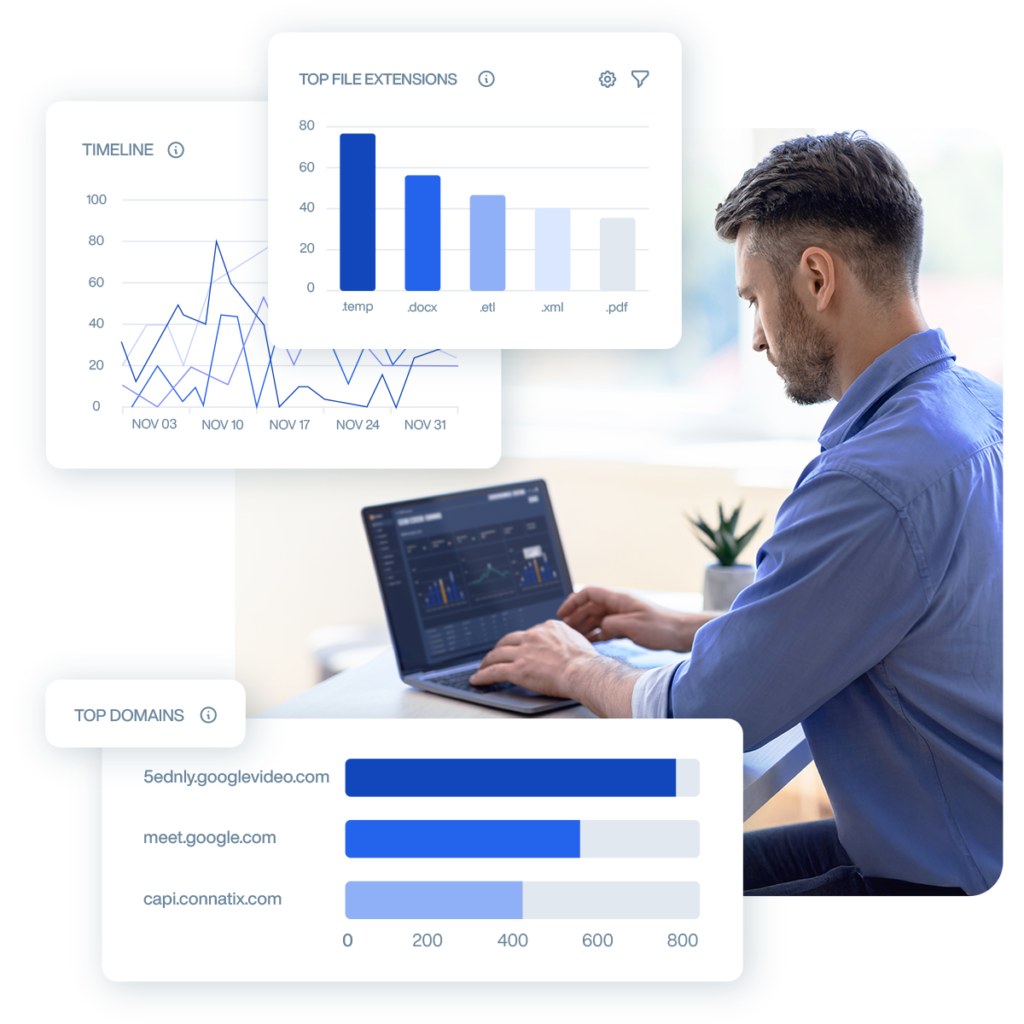
- Proven Compliance: Meeting strict federal requirements, including FISMA, NIST, ISO 27001, EO 14028, FAR 52, and CNSSD 504
- Complete User Activity Monitoring: Track activity across 15+ threat vectors with real-time monitoring of all user interactions
- Proactive Threat Prevention: Stop data breaches and insider threats before they happen with behavioral analytics and automated risk assessment
- Forensic Investigations & Audits: Collect video/audio recordings, alert reports, case management, and immutable audit logs
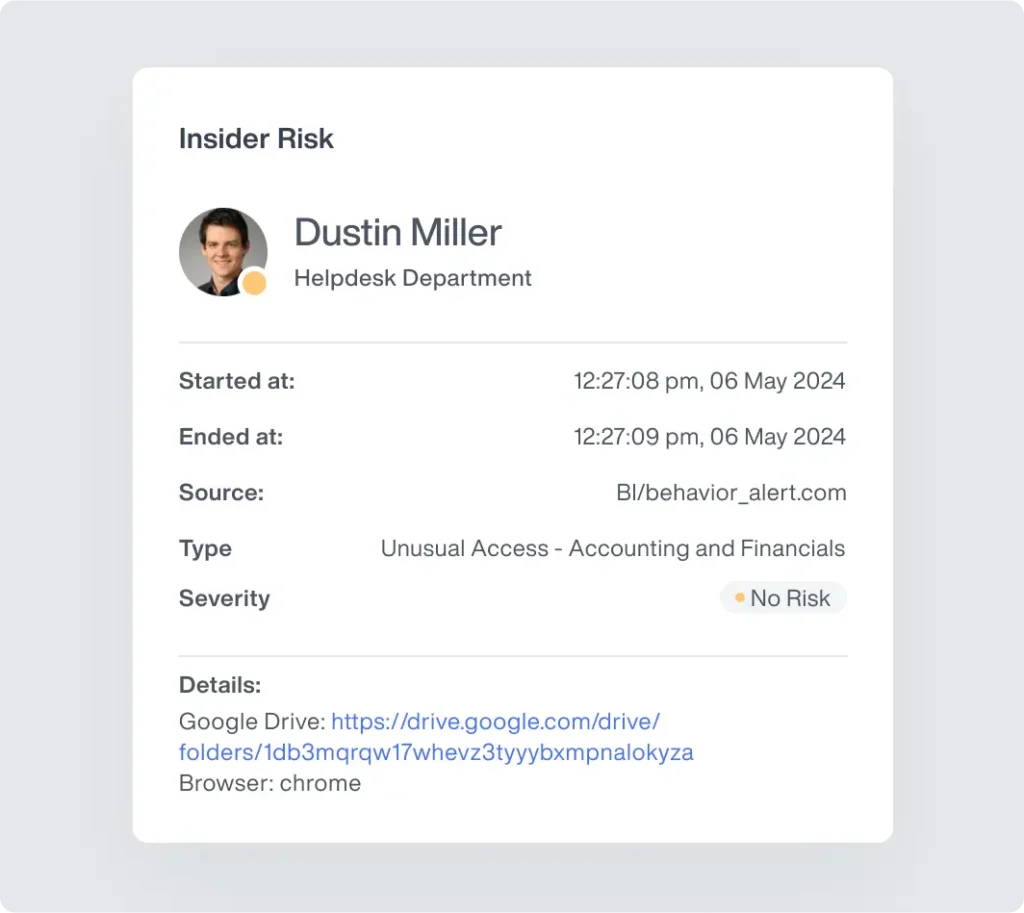
How Government Agencies Use Teramind
Intelligence Agencies
Protect classified information with multi-layer security controls and advanced user activity monitoring
Administrative Departments
Optimize workforce productivity and improve resource allocation with detailed activity analytics
Defense & Military
Track privileged user activity across secure networks while measuring operational efficiency metrics
Real-Time Monitoring
Track employee activity and computer usage across Windows and Mac devices with minimal performance impact.
Productivity Optimization
Improve agency efficiency with employee productivity tracking that identifies bottlenecks and streamlines workflows.
Risk Mitigation
Protect your agency from insider threats and data breaches with behavior analytics..
Comprehensive User Activity Monitoring & Insider Threat Protection
Teramind delivers a fully automated TDIR (Threat Detection, Investigation, and Response) program with user activity monitoring, behavior analytics, risk scoring, and enterprise-grade data loss prevention—all designed specifically for government security requirements.
Zero-Trust Security Framework
Implement a true zero-trust architecture with user activity monitoring that protects your agency’s most sensitive data from insider threats.
- Satisfy Executive Order 14028 with NIST-compliant RBAC and identity management
- Enforce the principle of least privilege with granular access controls for all users
- Implement separation of duties to prevent privilege abuse and unauthorized actions

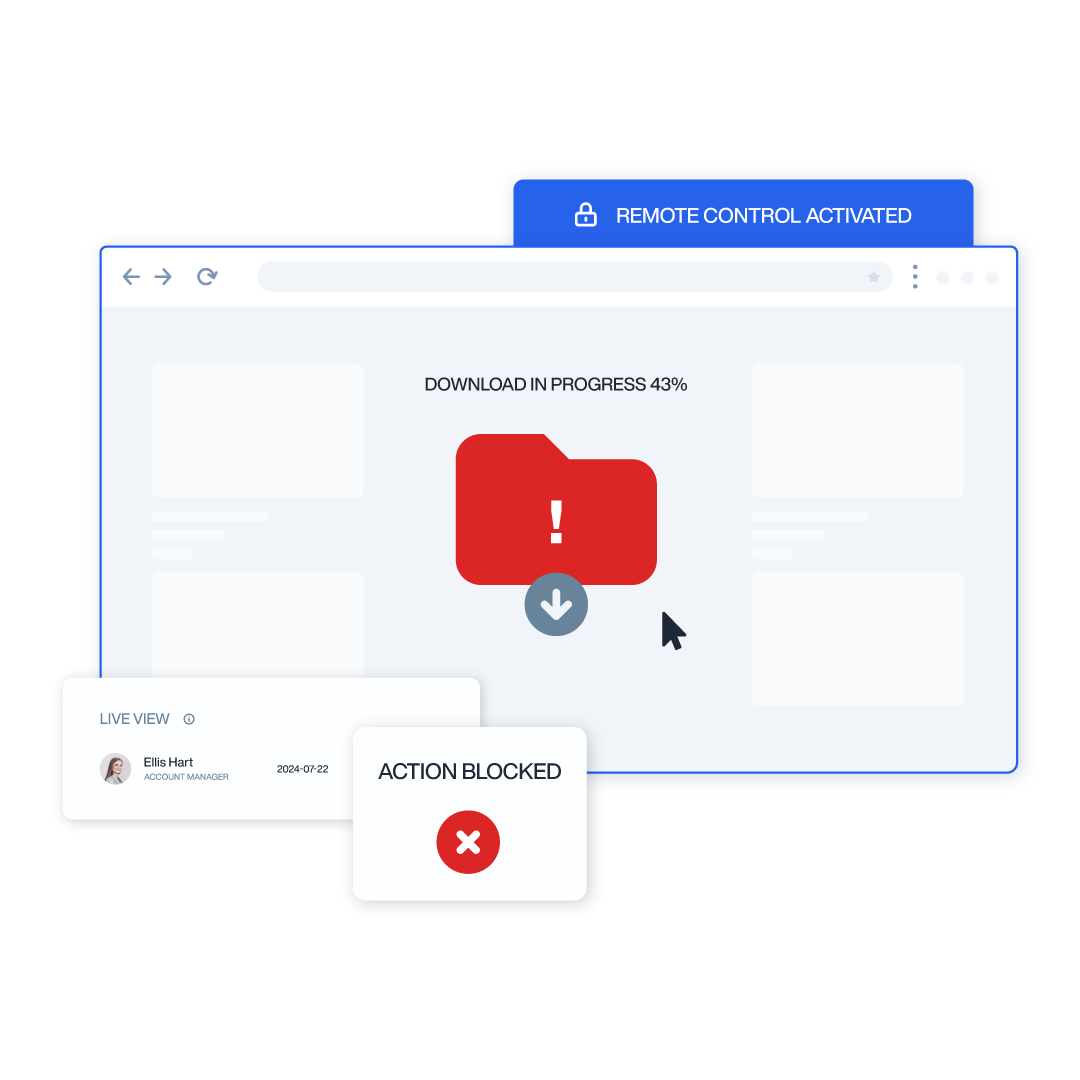
Advanced User Activity Monitoring & Threat Prevention
Identify suspicious behavior patterns before they escalate into security incidents with continuous monitoring of all user activities.
- Monitor 15+ threat vectors, including web, apps, email, file transfers, and keystrokes
- Deploy Machine Learning (ML) powered behavioral analytics to detect anomalies in real-time
- Create risk profiles with built-in scoring for all users and privileged accounts
- Receive immediate alerts when high-risk activities are detected
- Automatically block high-risk activities based on behavioral rules
Government-Compliant Deployment Options
Choose the deployment model that best fits your agency’s security requirements.
- Deploy on GSA-certified Cloud, On-Premises, AWS GovCloud, or Azure Government
- Integrate with existing SIEM and SOAR systems
- Maintain complete data sovereignty with air-gapped options for classified environments
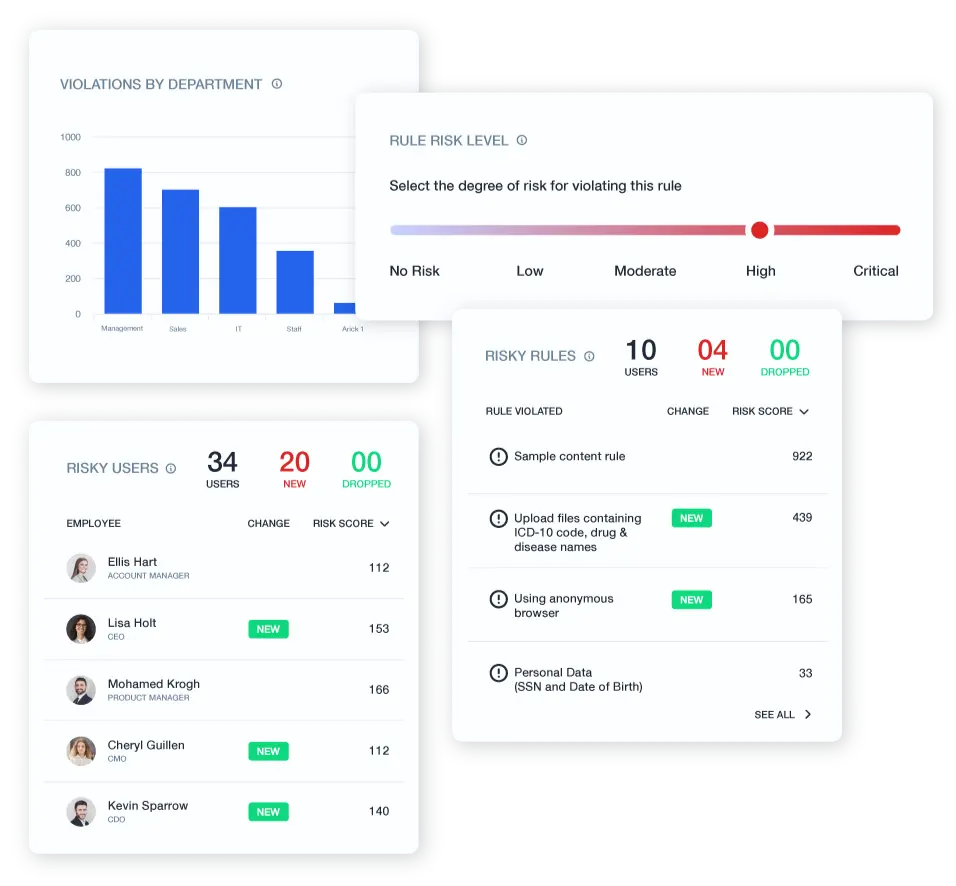
Comprehensive Audit & Investigation Capabilities
Conduct thorough investigations with irrefutable forensic evidence.
- Capture detailed audit trails, including screen recordings and keystroke logs
- Maintain immutable logs for compliance and investigation purposes
- Export detailed reports for incident response and regulatory requirements
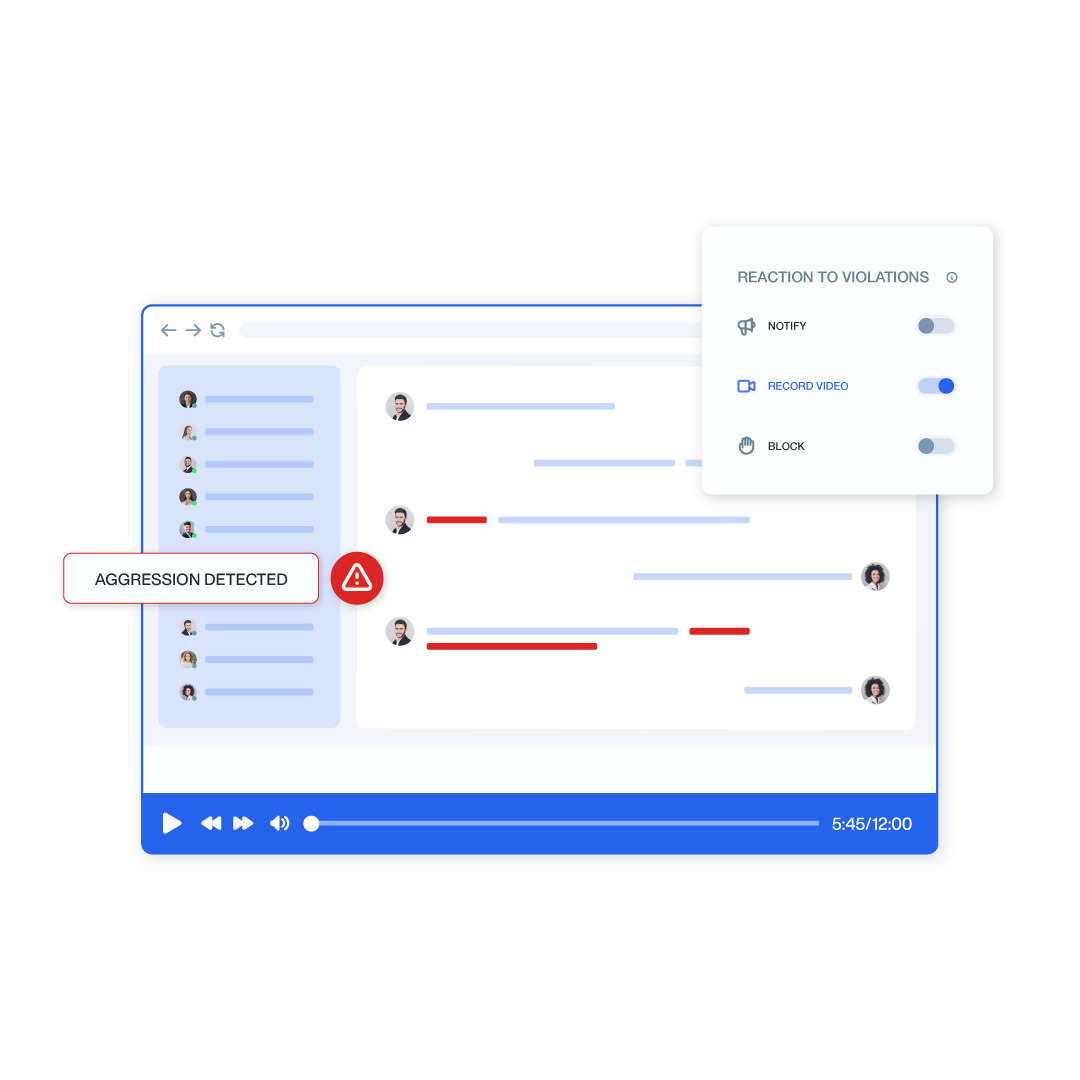
Remote Workforce Security
Extend your security perimeter to include work-from-home employees and contractors.
- Monitor remote user activity with the same level of detail as on-site personnel
- Apply consistent security policies across all endpoints regardless of location
- Detect and prevent data exfiltration via personal devices or cloud services
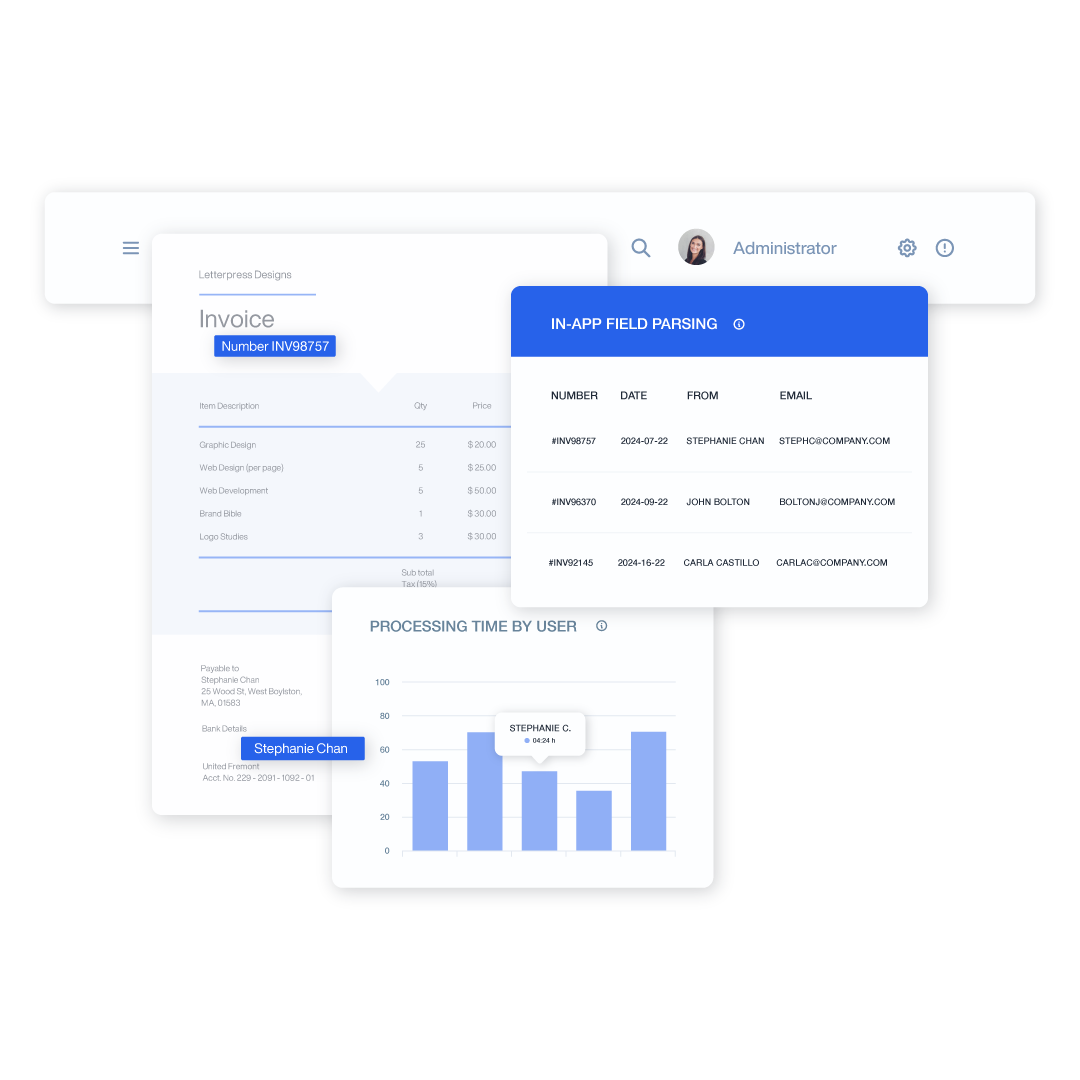
Automated Compliance Enforcement
Ensure adherence to government regulations with automatic policy enforcement.
- Implement controls for FISMA, NIST, ISO 27001, DoDI and more
- Automate data discovery, classification, and protection with behavioral DLP rules
- Generate compliance reports that satisfy strict government audit requirements
Teramind's Monitoring & Security Features
Leverage Teramind’s unparalleled power to solve your workforce challenges.
Screen & Audio Recording
Monitor employee screens in real-time or record them for irrefutable evidence. Optionally, record audio input and output too for additional evidence.
Optical Character Recognition
Teramind’s OCR functionality allows you to extract text from images and screenshots, enhancing your monitoring and analysis capabilities.
Website
Monitoring
Track employee time spent on websites, identify unproductive web browsing, and enforce company policies with comprehensive website monitoring.
Application
Monitoring
Monitor application usage, track time spent on specific apps, and identify potential security risks with detailed application monitoring on your endpoints.
Email
Monitoring
Monitor employee emails to prevent data leaks, ensure compliance with company policies, and protect sensitive information.
Instant Message Monitoring
Track instant messages and conversations to gain insights into team communication and collaboration, and ensure compliance.
Social Media Monitoring
Monitor social media activity to protect your brand reputation, prevent data leaks, and ensure employees adhere to company policies.
Network
Monitoring
Gain visibility into network activity, identify potential security threats, and optimize network performance with network monitoring.
Citrix/Session Hosts Monitoring
Monitor employee activity within Citrix, terminal servers, RDP or virtual environments. Track application usage and ensure data security with specialized monitoring.
Remote Desktop Control
Take control of remote employee computers in real-time to provide support, troubleshoot issues, or prevent data breaches and insider threats.
RDP Session Recording
Record RDP sessions to gain a comprehensive understanding of user activity, troubleshoot technical problems, and ensure compliance.
Productivity
Analysis
Analyze employee productivity with detailed metrics, identify areas for improvement, and boost productivity across your team members.
Active Vs. Idle
Time Logs
Track active and idle time to understand how employees spend their work hours and optimize time management and productivity.
Unproductive Work
Time Analysis
Identify unproductive work time, analyze patterns, and implement strategies to improve efficiency and time management.
Try Platform
With a Live Demo
to see how it works.

What our Customers Say
“Easy Implementation, Great UI, and amazing product. We leverage Teramind to manage high-risk situations to get in-depth visibility and alerting. It has far surpassed our expectations and has saved us significant data loss.”
IT Security & Risk Manager
$7B Manufacturing Enterprise
“Cost effective and feature reach DLP and User Behaviour Monitoring Tool. Easy to set up even on-premises. No end-user impact. Cost-effective. Both DLP and User behavior Monitoring.”
IT Manager
$3B Managed Services Provider
“It’s been an amazing experience and a wonderful software that does exactly what you want! Security, control, peace of mind, the ability to know all that is going on in the organization. Very easy to use. It gives you real data! It has given us the protection that we need!”
Renee H
Head of IT Security
FAQs
How does Teramind help government agencies meet FISMA and NIST compliance requirements?
Teramind provides built-in controls and reporting capabilities specifically designed to address federal compliance frameworks. Our solution includes automated policy enforcement for FISMA, NIST 800-53, NIST CSF, and other government standards. Our platform’s comprehensive audit trails, immutable logs, and detailed reporting make it easier to demonstrate compliance during audits. Teramind’s deployment options—including FedRAMP-ready cloud environments — ensure your agency can maintain compliance while implementing robust insider threat protection.
Can Teramind be deployed in classified or air-gapped environments?
Yes, Teramind offers flexible deployment options that include on-premises installation for classified and air-gapped environments. Our solution can be implemented without external connectivity requirements, making it suitable for SCIFs and other high-security facilities. Teramind’s on-premises deployment maintains all the functionality of our cloud solutions while ensuring data never leaves your secure environment. We also support deployment on AWS GovCloud and Azure Government for agencies requiring cloud solutions that meet government security standards.
How does user activity monitoring work without impacting employee productivity?
Teramind’s user activity monitoring is designed to operate with minimal system impact. The lightweight agent uses less than 1% CPU utilization during normal operations (and can be hidden or revealed to users). Agencies can configure the monitoring scope to focus only on the activities that matter for security and compliance, reducing any potential performance impact while maintaining comprehensive visibility into risky behaviors.
What types of insider threats can Teramind detect that traditional security tools miss?
Unlike traditional security tools focusing on network perimeters or system vulnerabilities, Teramind monitors user behavior to identify threats that other solutions miss. This includes detecting unusual file access patterns, suspicious after-hours activity, unauthorized data transfers, policy violations, and signs of account compromise. Our behavioral analytics can identify subtle changes in user activity that may indicate an insider threat developing over time. Teramind can also detect threats from privileged users who have legitimate access to sensitive systems but are misusing their permissions.
How quickly can Teramind be implemented across a government agency?
Most government agencies can deploy Teramind enterprise-wide within 1-2 weeks. Our implementation team includes specialists with experience in government security requirements who can assist with configuration, policy development, and integration with your existing security infrastructure. Implementation can typically be completed in just a few days for smaller agencies or departments. Teramind also offers expedited deployment options for agencies responding to active security incidents or urgent compliance deadlines.
Does Teramind integrate with our existing security tools and SIEM systems?
Teramind integrates with leading SIEM platforms, including Splunk, IBM QRadar, LogRhythm, and others used by government agencies. The platform provides pre-built connectors for security orchestration tools and can share alerts, logs, and activity data with your existing security ecosystem. This integration capability allows agencies to maintain their current security investments while enhancing them with Teramind’s user activity monitoring and insider threat detection. Our open API supports custom integrations for specialized government systems and security tools.

