Slack DLP
Protect Your Most Sensitive Communications in Slack
Detect and prevent insider threats and maintain compliance across all Slack workspaces with Teramind’s employee monitoring and DLP controls.
The Future of Slack Security in Modern Businesses
While Slack revolutionizes workplace collaboration, it also creates new vectors for data exfiltration and insider threats. Teramind’s behavioral analytics and machine learning provide comprehensive protection without impeding operational efficiency.
Real-Time Message Monitoring
Leverage advanced natural language processing and behavioral analytics to identify and prevent data exfiltration through Slack messages
- Smart message scanning: Deploy contextual DLP that uses machine learning to analyze message content, attachments, and sharing patterns to prevent sensitive data exfiltration while minimizing false positives and business disruption
- Learning from patterns: Establish baseline communication patterns through behavioral analytics and machine learning to detect anomalies that could indicate insider threats or compromised credentials
- Automated incident response: Implement granular response policies that can automatically quarantine messages, revoke access, or trigger security workflows based on risk severity and behavioral context
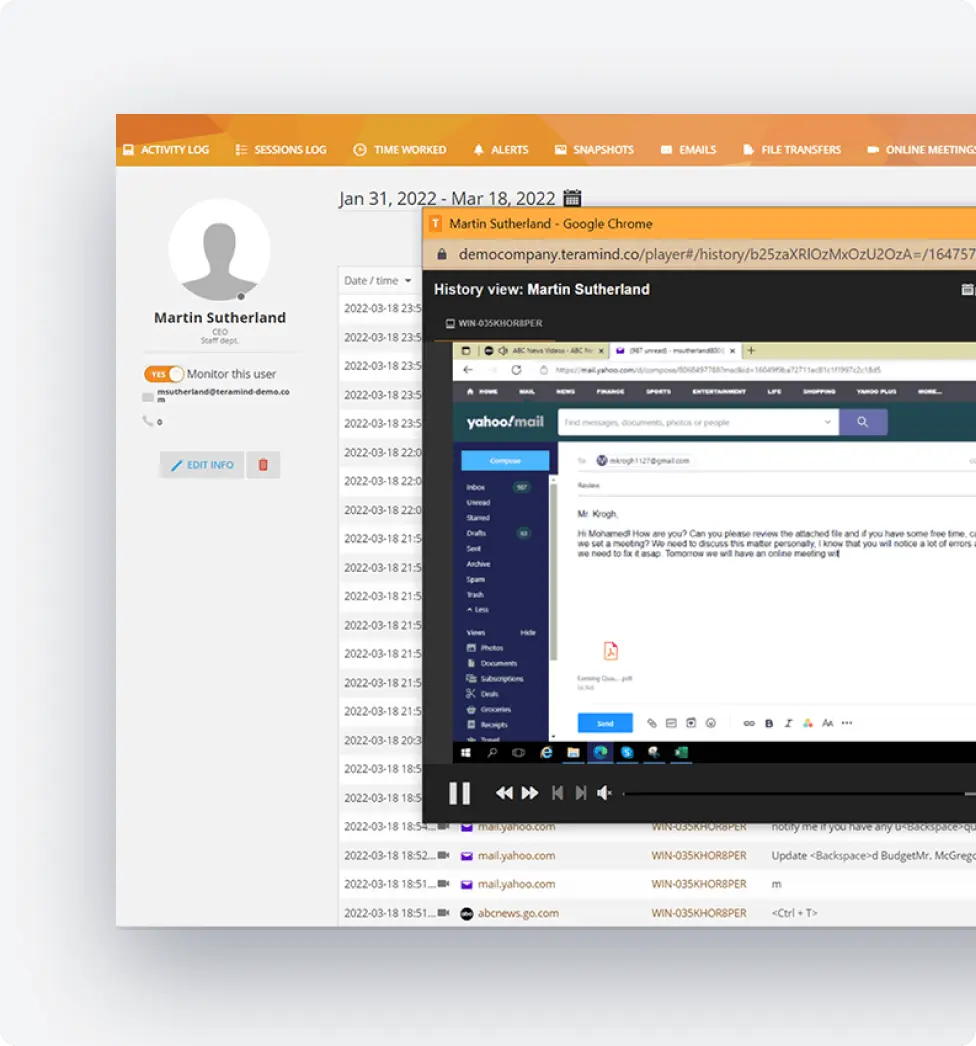
File Transfer Security Controls
Implement context-aware file monitoring and automated data loss prevention across all Slack file-sharing activities
- Advanced file analysis: Combine deep content inspection, behavioral analytics, and machine learning to identify sensitive data patterns and prevent unauthorized exfiltration through file uploads
- Dynamic access control: Deploy adaptive file sharing policies that automatically adjust based on user behavior patterns, data sensitivity, and risk scoring algorithms
- Exfiltration pattern detection: Monitor file sharing velocity, timing, and recipient patterns to identify potential data staging or unauthorized bulk transfers before sensitive information leaves your environment
Channel Access Governance
Maintain granular control over information flows and enforce least-privilege access across all Slack workspace communications
- Behavioral channel monitoring: Apply machine learning to analyze channel creation, membership, and activity patterns to prevent unauthorized lateral movement and data access
- Zero-trust access enforcement: Implement continuous authentication and dynamic authorization based on behavioral risk scoring and real-time activity analysis
- Cross-channel threat detection: Monitor inter-channel communication patterns to identify potential data spillage, privilege escalation, or insider collusion attempts
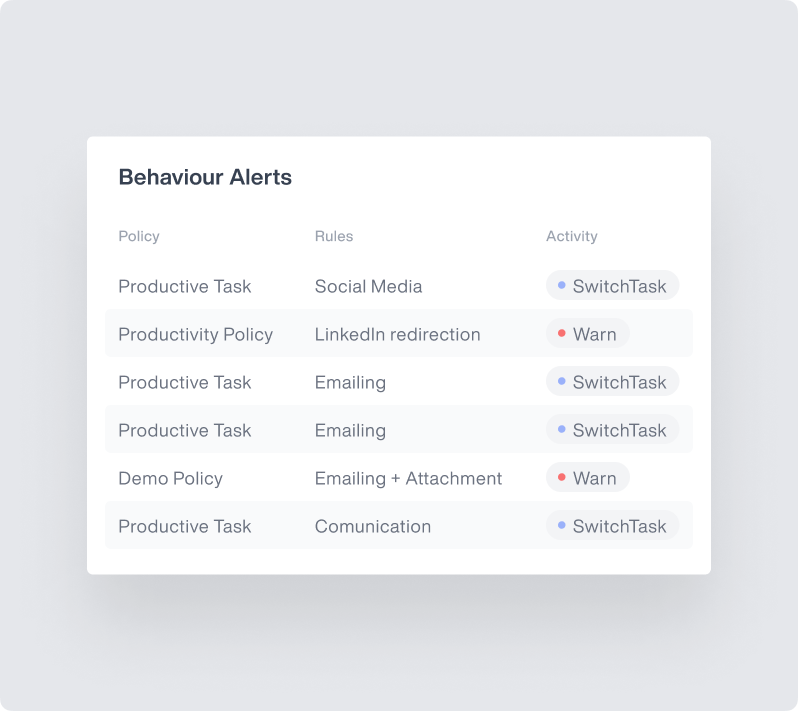
Advanced Behavioral Analytics
Leverage sophisticated machine learning and user behavior analytics (UBA) to identify abnormal activities and potential insider threats
- ML-powered baseline modeling: Build comprehensive behavioral baselines across users, channels, and workspaces to enable accurate anomaly detection with minimal false positives
- Advanced anomaly detection: Apply multiple machine learning algorithms to identify subtle behavioral changes that could indicate account compromise or insider threats
- Risk-based threat scoring: Combine behavioral indicators, historical patterns, and security context to generate accurate risk scores for real-time response automation
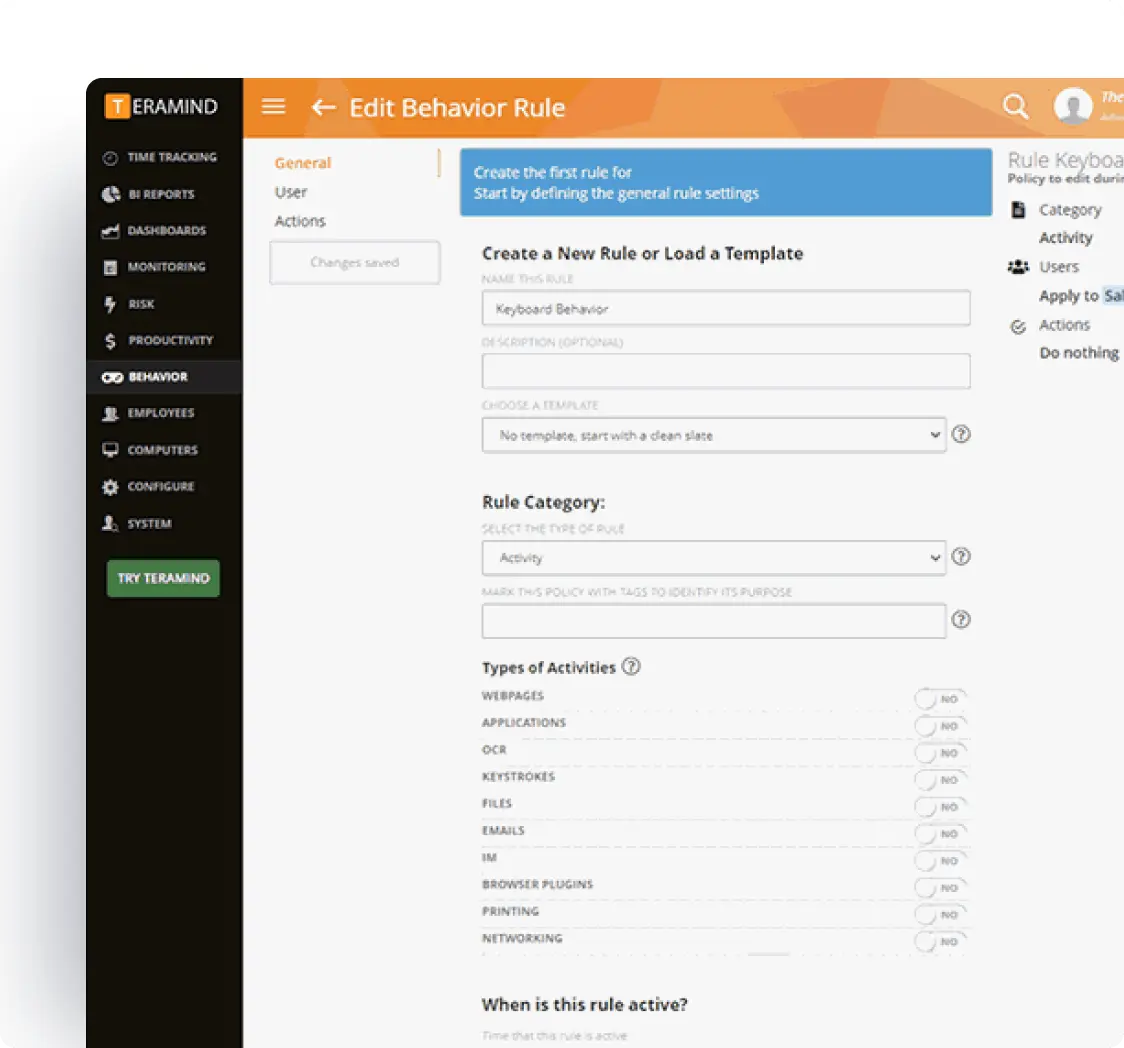
Compliance and Audit Controls
Maintain comprehensive compliance with regulatory requirements while enabling seamless investigation and reporting capabilities
- Immutable audit logging: Maintain tamper-proof records of all Slack activities with full metadata preservation for forensic investigation and compliance reporting
- Policy automation framework: Deploy intelligent compliance rules that adapt to changing business needs while maintaining consistent policy enforcement
- Advanced compliance reporting: Generate detailed compliance reports with full activity timelines, risk assessments, and response documentation
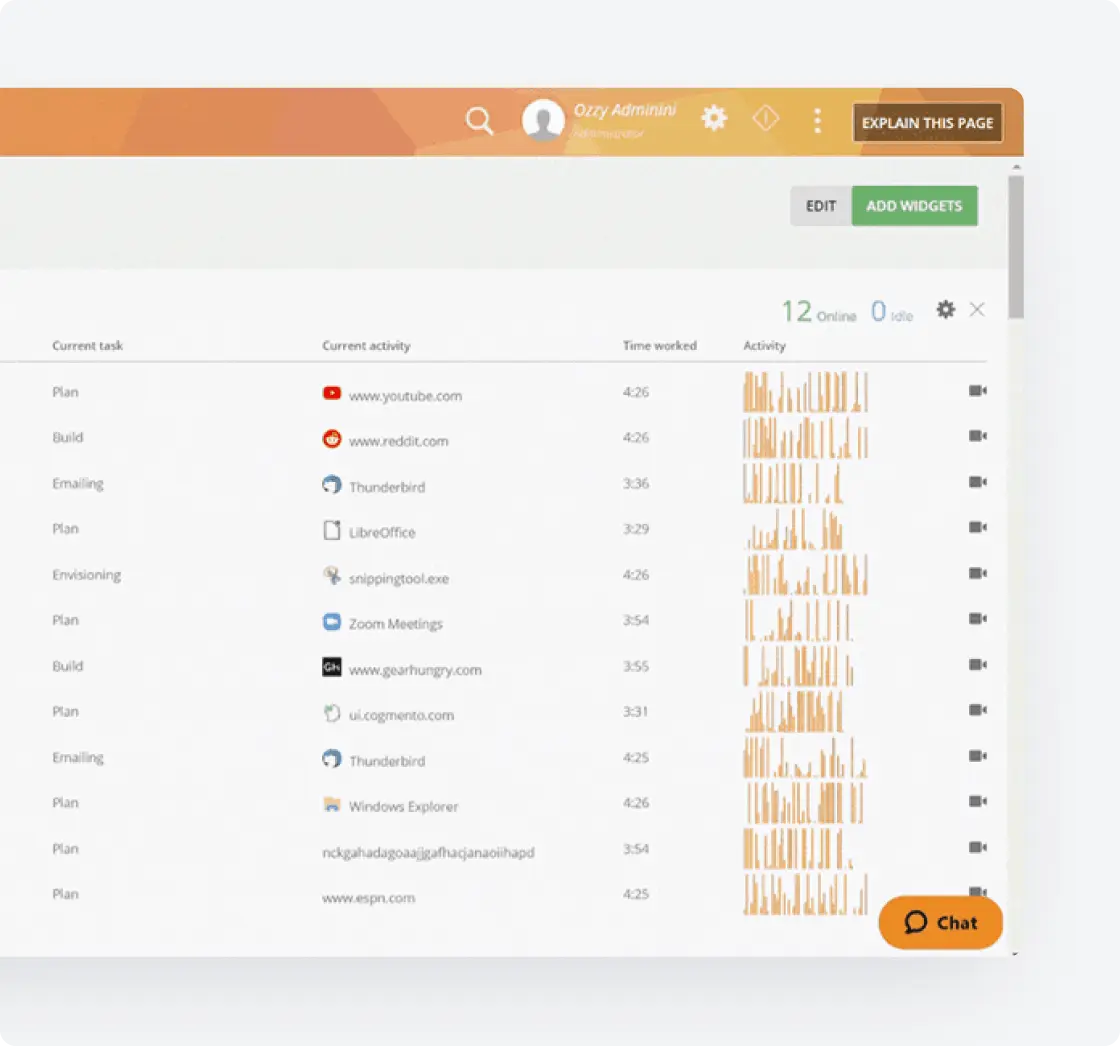
Security Integration and Orchestration
Enhance your security infrastructure with seamless integration of Slack monitoring and automated incident response
- Enterprise security integration: Integrate Teramind’s Slack monitoring capabilities with your existing SIEM, SOAR, and security tools through robust APIs and pre-built connectors
- Unified security analytics: Consolidate Slack security metrics with other data sources to enable comprehensive threat detection and incident investigation
- Automated incident orchestration: Trigger automated response workflows across your security stack based on behavioral risk scores and threat detection

Core Teramind Features
Leverage Teramind’s unparalleled power to solve your workforce challenges.
Live View & Historical Playback
Monitor employee screens in real-time or review past activity with historical playback to gain complete visibility into user activity and computer activity.
Optical Character Recognition
Teramind’s OCR functionality allows you to extract text from images and screenshots, enhancing your monitoring and analysis capabilities.
Website
Monitoring
Track employee time spent on websites, identify unproductive web browsing, and enforce company policies with comprehensive website monitoring.
Application
Monitoring
Monitor application usage, track time spent on specific apps, and identify potential security risks with detailed application monitoring on your endpoints.
Email
Monitoring
Monitor employee emails to prevent data leaks, ensure compliance with company policies, and protect sensitive information.
Instant Message Monitoring
Track instant messages and conversations to gain insights into team communication and collaboration, and ensure compliance.
Social Media Monitoring
Monitor social media activity to protect your brand reputation, prevent data leaks, and ensure employees adhere to company policies.
Network
Monitoring
Gain visibility into network activity, identify potential security threats, and optimize network performance with network monitoring.
Citrix
Monitoring
Monitor employee activity within Citrix environments, track application usage, and ensure data security with specialized Citrix monitoring on your devices.
Remote Desktop Control
Take control of remote employee computers in real-time to provide support, troubleshoot issues, or prevent data breaches and insider threats.
RDP Session Recording
Record RDP sessions to gain a comprehensive understanding of user activity, troubleshoot technical problems, and ensure compliance.
Productivity
Analysis
Analyze employee productivity with detailed metrics, identify areas for improvement, and boost productivity across your team members.
Active Vs. Idle
Time Logs
Track active and idle time to understand how employees spend their work hours and optimize time management and productivity.
Unproductive Work
Time Analysis
Identify unproductive work time, analyze patterns, and implement strategies to improve efficiency and time management.
Try Platform
With a Live Demo
to see how it works.

What our Customers Say
“The interface and reporting capabilities of Teramind remain unmatched compared to other products we have tried. Overall, Teramind is far more advanced than other competitors. They are definitely raising the bar and I’ll back them up any day.”
Ricky H.
Government Administration
“It’s been an amazing experience and a wonderful software that does exactly what you want! Security, control, peace of mind, the ability to know all that is going on in the organization. Very easy to use. It gives you real data! It has given us the protection that we need!”
Rene H.
Head IT Security
“This software has allowed us to save from a potential data breach and being able to catch people leaving who tried to take our IP. Very good software. A bit on the expensive side but worth every penny. Functionality is easy to get around. Has a great GUI.”
Milena L.
IT Manager

A Practical Approach to Data Loss Prevention in Slack
All businesses handle sensitive information regularly, but what happens if that data is compromised? Data loss can have severe consequences, ranging from regulatory compliance violations to financial loss and reputational damage. Hence, why implementing robust security measures is crucial to safeguarding classified information.
Slack, a popular cloud-based messaging app, helps streamline communication in the workplace. This collaboration tool allows for real-time sharing of data, documents, project updates, and more – which is especially beneficial for remote teams. However, any time you’re sharing proprietary information, protecting your data is crucial.
What is Data Loss Prevention (DLP) for Slack?
Generally speaking, data loss prevention solutions monitor traffic across all communication platforms to detect any potential security threats. DLP systems prevent the transfer of inappropriate messages and data—ensuring that only authorized individuals can access and distribute confidential information.
Data loss prevention (DLP) for Slack refers to the tools and strategies that prevent the unauthorized sharing, transfer, or loss of sensitive data. Slack DLP monitors data and scans messages and text-based files sent by members of your organization for any content that violates rules you create.
Since Slack is widely used for workplace communication, implementing data loss prevention measures is critical to ensuring compliance, protecting data, and mitigating the risk of insider threats. While Slack does offer its own built-in DLP, the functionality is somewhat limited.
Limitations of Slack’s Built-in DLP
Mastering Slack data loss prevention requires the integration of external tools, security policies, and user training. Slack’s built-in DLP has constraints, including reliance on standard expression formats and basic matching criteria. These limitations may prove insufficient in today’s complex data security environment.
Slack’s method for detecting protected health information (PHI) is based on simple pattern matching techniques, versus utilizing more sophisticated reasoning. This approach may yield the following constraints:
- Pattern-Oriented Matching: Slack identifies sensitive information by searching for established patterns, such as Social Security numbers, credit card numbers, or medical records formats. This method may result in false positives and false negatives—failing to detect disclosures of protected health information.
- Misinterpretation of Context: Context may not be interpreted correctly because Slack’s built-in security features don’t analyze surrounding text to determine if the detected pattern is actually PHI.
- Lack of Complex Combination Logic: More advanced DLP solutions utilize multiple data points to confirm a PHI violation, while Slack lacks this capability—resulting in less effective PHI protection.
- Limited Integrated DLP Controls: Slack does not offer data loss prevention tools for its Enterprise Grid customers, thus businesses must rely on third-party integrations such as Nightfall AI for more robust PHI detection and prevention.
Key Strategies for Effective Slack DLP
The objective is to develop a robust data loss prevention strategy that will mitigate the risks of data leaks, compliance breaches, and unauthorized access within Slack. Key strategies to enhance Slack DLP include a combination of third-party integrations, security policies, employee training, and proactive monitoring.
Build Your Human Firewall
Employees often act as the first line of defense against cyber threats. By providing proper training and awareness, businesses can build what’s known as a human firewall to prevent cyberattacks, data breaches, and phishing attempts. Employing these best practices will help strengthen your firewall:
- Educate employees on methods to prevent malicious access and provide guidelines on the appropriate information to share.
- Encourage employees to create strong passwords and enable multi-factor authentication (MFA) for their Slack accounts.
- Establish clear policies for external sharing of sensitive data, such as intellectual property.
Establish Data Classification Policies
Data classification policies assist businesses in organizing, safeguarding, and overseeing data—based on sensitivity and importance. Developing defined policies for organizing data will help signify different levels of confidential information, while proper categorization will signify how strong access controls need to be for specific files. Using Teramind’s data loss prevention tools will promote compliance, enhance security, and minimize the risk of data breaches.
Encrypt Your Sensitive Data
Encrypting your data within Slack, both when stored and during transmission, will ensure that your sensitive information remains unaccessible to anyone who might intercept it. Be sure to verify whether or not your Slack subscription allows for this feature.
Slack does not offer end-to-end encryption; however, enterprise key management (EKM) is available for Slack Connect. Utilizing an EKM system can help secure the encryption of your messages and files.
Monitor Your Slack Environment
Monitoring your Slack environment is essential to securing sensitive information and detecting insider threats. Utilizing such robust collaboration software can put your organization at high risk for a data leak. To effectively monitor activity, you can use Slack’s native audit logs, integrate with an SIEM tool, or implement a DLP tool. Mimecast Aware is one solution that ingests all Slack messages in real time and detects any unauthorized content.
Here are the activities that you should be monitoring in Slack:
- User activity: unusual login locations, frequent password resets, or suspicious message content
- File sharing: sharing of large volumes of data-sensitive documents
- Channel activity: unusual message patterns or discussions about sensitive topics
- External user access: activity from users outside of your organization
- Administrative actions: changes to user permissions or channel modifications
Enable Two-Factor Authentication (2FA)
Enabling two-factor authentication (2FA) in Slack enhances security by adding a second verification step during the login process—minimizing the risk of unauthorized access. It’s highly recommended that all Slack users enable 2FA for another layer of security. Executing strategies that reduce the risk of unauthorized access is critical if an individual’s password is compromised.
Regularly Review Third-Party Integrations
Slack is so popular among enterprises because it can connect with more than 2,600 third-party integrations. Many organizations use well-known apps such as Salesforce, Asana, and Google Drive in conjunction with Slack. These applications may create vulnerabilities and potentially comprise data stored within your Slack workspace. Administrators should thoroughly assess each integration’s security and permissions thoroughly and regularly audit any apps connected with Slack.
Essential Functionalities for a Slack DLP Solution
There are many features of a Slack DLP solution that are vital because they allow organizations to proactively detect and prevent the sharing of sensitive information within the Slack workspace. The following functionalities all aid in safeguarding confidential data, maintaining regulatory compliance, and minimizing the risk of data breaches:
Content Analysis
The DLP solution that you employ should be able to scan messages for sensitive information, files, and any other content shared within Slack channels. This could include personally identifiable information (PII), financial details, intellectual property, and more.
The solution should also allow for flexible rule customization, seamless integration with other tools, and the ability to define custom keywords. Proactive intervention is paramount to preventing data leaks.
Flexibility
Organizations should have the flexibility to establish and tailor DLP rules to meet their specific data security needs. Administrators of the Slack workspace must have the capability to establish guidelines and identify potential scenarios that could result in a breach of policies by using specific patterns or keywords.
Real-time Alerts
Real-time monitoring of Slack communications is critical to identifying potential violations as they occur—allowing for immediate alerts that notify administrators promptly. This way, they can proactively address the situation to minimize data loss or exposure risks.
Actionable Insights
DLP solutions should provide visibility into policy breaches, data leaks, and trends, thus enabling more robust reporting and auditing capabilities. The actionable insights obtained will allow the organization to better evaluate the situation and make informed decisions that will enhance its security posture.
Integration with Other Tools
The Slack DLP solution must also be able to effortlessly integrate with various tools to enhance enterprise data security options. It should guarantee complete protection through the implementation of data loss prevention solutions, security information, event management systems (SIEM), or other relevant safety protocols.
Protecting Slack Data Security
While Slack is an essential tool for collaboration among many teams, it can easily become a vulnerability without proper data security measures. To secure Slack data, it’s important to enforce access controls and monitor user activities to prevent data leaks and cyber threats. Organizations should employ a proactive approach to Slack security to minimize any potential risks.
Identifying and Classifying Sensitive Information
To successfully execute data loss prevention within Slack, enterprises need to identify and categorize all sensitive data that is transmitted via messages, channels, and file-sharing. This could include payment card data, personally identifiable information, or any other confidential information.
Using tools like Teramind can help to detect and classify sensitive data in real time. Teramind’s DLP solution uses advanced technology to monitor, detect, and prevent potential data loss or breaches before they occur.
Implementing Data Security Measures
Effectively implementing data security measures in Slack requires a structured approach and should incorporate encryption, access control, and data governance. The use of tools like Expireon, a DLP solution that enhances Slack’s native capabilities, provides additional layers of security.
Enhancing Slack Data Loss Prevention
A comprehensive approach is needed to strengthen and enhance data loss prevention in Slack. To obtain maximum security, organizations should integrate a multifaceted approach to include advanced detection, access controls, real-time monitoring, and automated security measures.
Tools and Solutions for Slack DLP
To successfully mitigate the risk of data leaks, unauthorized access, and compliance violations in Slack, organizations should deploy data loss prevention tools that actively monitor, identify and protect sensitive information.
Tools like Teramind are designed to enhance Slack’s native DLP and provide additional layers of security. Integrating DLP solutions with other tools will improve your enterprise data security options.
Customization Options for Slack DLP
Organizations can customize their Slack DLP to meet their unique security requirements and operational needs. You should be able to scan files and messages from various file categories. The following are seven key customization options for tailoring your Slack data loss prevention strategy:
- Define custom-sensitive data categories such as health, financial, and legal.
- Block specific keywords like social security numbers and credit card details.
- Limit the external sharing of sensitive files and messages.
- Initiate automated alerts when policy violations occur.
- Delete sensitive messages after a predetermined period i.e. 30 days.
- Create real-time monitoring dashboards.
- Establish unique encryption keys by department or region.
You can also utilize tools like Teramind to incorporate custom detectors, specific rules, keywords, regexes, and pre-configured detectors that encompass a wide range of data types.
Conclusion
If your organization regularly uses Slack for communication and collaboration, you must secure the data included within. It is not uncommon for multiple teams and departments to share financial data and other proprietary information via Slack. While primarily used internally, any tool that allows file sharing is susceptible to hackers, especially if there is sensitive information inside.
To protect your enterprise and customer data, and to remain compliant with regulations, it is recommended that you implement a data loss prevention solution within your Slack workspace.
Effectively mastering Slack DLP means adopting a comprehensive and proactive approach that integrates advanced security tools, a solid compliance framework, and user training. When deployed correctly, organizations can prevent and mitigate data leaks and breaches – and that’s something you can’t put a price on.

