
What Is An Insider Threat: The Definitive Guide to Insider Threats, The Risks They Pose & How to Address Them
Today’s businesses operate in a complicated cybersecurity and data privacy environment. Whether they are guarding against expensive ransomware attacks or reputation-damaging data breaches, today’s landscape has one thing in common: people are often the problem.
According to Verizon’s 2022 Data Breach Investigations Report, 82 percent of data breaches involved the human element, including insider threats.
In other words, insider threats pose a significant risk to a company’s cybersecurity, operational, and regulatory efforts. Keep reading to learn about insider threats, the risks they pose, and the steps companies can take to protect their data and IT infrastructure.
What is an Insider?
Insiders include leaders, employees, contractors, and trusted third parties with access to company data and IT infrastructure. Examples of insiders include:
- High-privileged users, such as network administrators, executives, partners, and other users, with permissions across sensitive data.
- Developers with access to data using a development or staging environment.
- Resigned or terminated employees with enabled profiles and credentials.
- Acquisition managers and employees.
- Vendors with internal access.
- Contractors with internal access.
- Partners with internal access.
Trusted by companies and equipped with login credentials and access to sensitive information, insiders can intentionally or unintentionally take action that puts the organization at risk.
What is a Malicious Insider?
Malicious insiders intentionally misuse data or network access to harm an organization. These threat actors have an advantage because they are difficult to detect as they operate with the company’s implicit trust, and they often know how to avoid raising suspicion or detection.
While any employee or contractor can be an insider threat, high-privileged users are most likely to cause a cybersecurity or data privacy incident because of their access to sensitive information.
How to Detect Malicious Insiders
Since insiders have access to network credentials and customer information, detecting malicious insiders is uniquely challenging. Detecting malicious insiders requires a combination of awareness and response efforts. In today’s digital-first operational environment, this often means deploying behavior analytics software to detect and prevent malicious insiders.
What is an Insider Threat?
An insider threat is a person with legitimate access to a company’s IT infrastructure and data who uses this access to unintentionally or intentionally undermine security.
Types of Insider Threats
- Unintentional. These insiders fall for a social attack, like a phishing scam, accidently share sensitive information, or mistakenly misuse company data. They didn’t mean to cause a problem, but their negligence or mischance can still cause significant damage to a company’s bottom line and brand reputation.
- Intentional. These insiders compromise network integrity or data privacy on purpose. Their motivations are multifaceted. Some are looking to profit from their privileged access, while others may be disgruntled employees or people looking to benefit from a company’s digital resources.
- Other. These insider threats are often collusive, recruited or enticed by cybercriminals or threat actors to provide login credentials or compromise network integrity from the inside.

Types of Insider Threat Attacks
Oblivious Insider. Insiders with important access to company information that have been compromised from the outside. Because the system is monitored from the outside, these employees are usually oblivious to the act.
According to one study, 83 percent of organizations experienced a successful phishing attack in 2021, often sharing account login information with threat actors. In total, one-third of employees are likely to fall for a phishing scam or social engineering attack. These oblivious insiders don’t compromise IT networks or company data on purpose, but the consequences are still devastating.
Negligent Insider. Insiders that are usually uneducated on potential security threats, or they simply bypass protocol to meet workplace efficiency goals. These employees are most vulnerable to social engineering attacks.
Especially in today’s hybrid work environment, employees are using personal devices to access company data with frightening regularity. One analysis found that 64 percent of employees use a personal device for work while only 43 percent are security enabled. This is just one example of negligent insiders putting cybersecurity and data privacy on the line.
Similarly, more than one-third of employees fail to regularly update their passwords, making it more likely that threat actors can leverage employee negligence to gain front-door access to company accounts of network infrastructure. For instance, when hackers infiltrated Colonial Pipeline, disrupting a major US natural gas pipeline with an expensive ransomware attack, the incident was traced back to an employee account with an outdated account password that was easily accessible on the Dark Web.
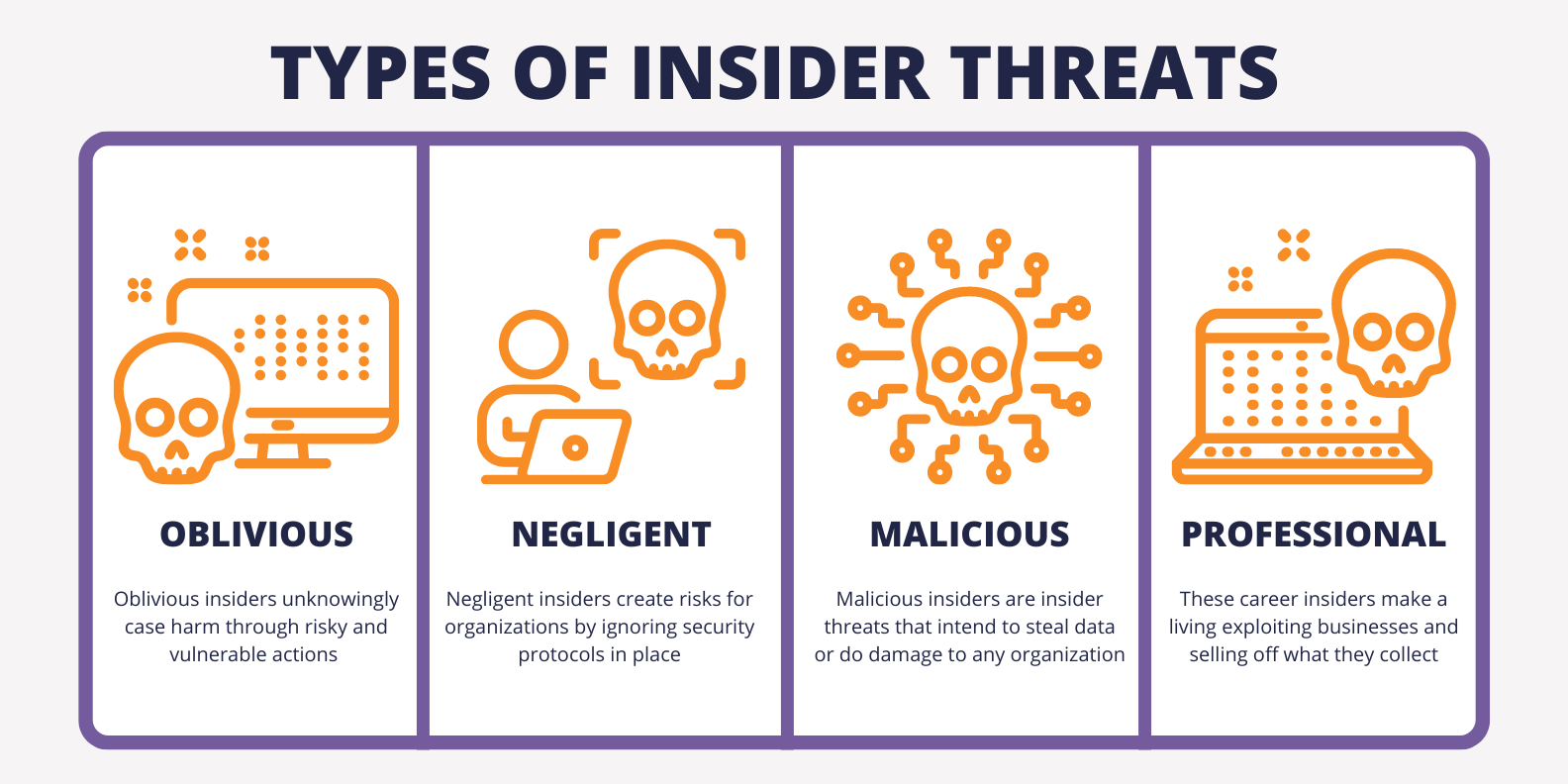
Malicious Insider. Insiders that steal data intentionally or destroy company networks, such as an employee that deletes company data on their last day of work.
For example, an employee at a US electric car company was paid $1 million by a Russian national to compromise his company’s network with malware, reflecting the external pressure and financial incentive that entice malicious insiders.
Professional Insider. Insiders making a career off exploiting company network vulnerabilities and sell that information on the Dark Web.
In 2019, a former Amazon Web Services employee used her professional background to exploit a loophole in her new employer’s firewall, allowing her to steal 100 million customer records, an expansive and expensive data breach enabled by a single insider threat.
Regardless of the attack type, insider threats put companies at risk, requiring today’s businesses to take steps to stop and present insider threats.
How to Stop and Prevent Insider Threats
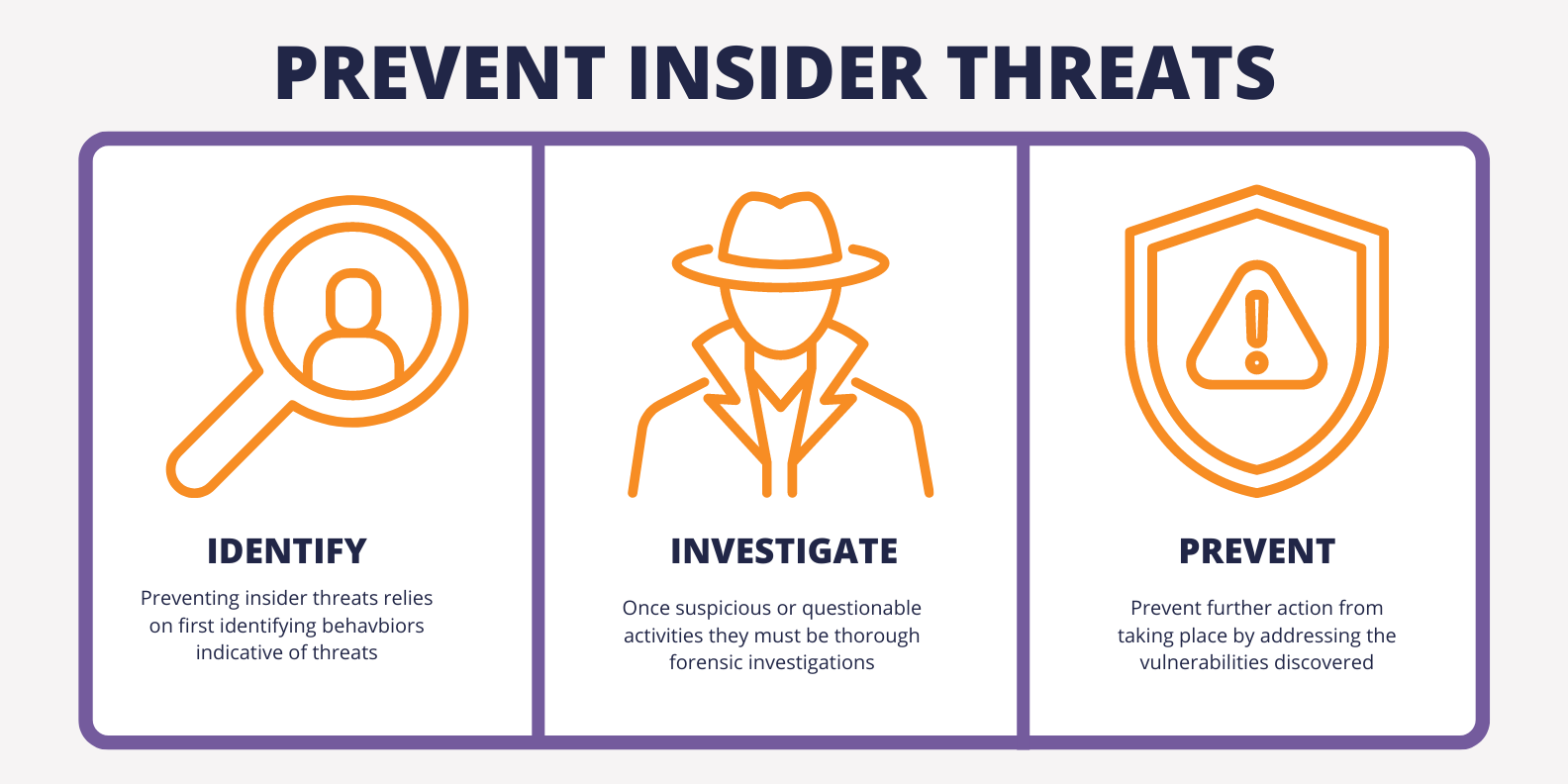
Identify. Effective insider threat prevention efforts begin with detection. Threat detection relies on identifying observable, concerning behaviors and activities that warrant further investigation. Successful programs will combine human intelligence with powerful insider activity monitoring software to detect possible threats.
Investigate. Investigating insider threats requires cybersecurity teams or management personnel to evaluate an attack’s veracity and determine the scope, intensity, and consequences of a potential threat.
Prevent. Prevention is the optimal outcome for insider threat mitigation efforts. By proactively preventing insider threats, companies can avoid costly data breaches and any consequential cybersecurity incidents.
Resources for Identifying and Detecting Insider Threats
Taken together, the stakes of insider threat detection and prevention are incredibly high, making it critical that companies know how to identify an insider threat.
Effective insider threat prevention programs will proactively mitigate vulnerabilities; first, by detecting and identifying observable behaviors that then need to be brought to the attention of company leadership or the cybersecurity team.
This requires both human and software solutions.
In response, companies should develop a “see something say something” policity as friends, family, and coworkers can help identify and report concerning behavior. Behavioral indicators might include:
- Dissatisfied or disgruntled insiders
- Documented attempts to avoid security protocols
- Changing work patterns or regularly working off-hours
- Displaying resentment for coworkers or leadership
- Contemplating resignation or actively looking for new job opportunities.
In today’s digital-first operational environment, software solutions are necessary tools for identifying and preventing insider threats.

What Software Should Companies Use to Detect, Investigate, & Prevent an Insider Threat?
Software that monitors endpoints, anomalous behaviors and user activity is most effective in detecting, investigating, and preventing insider threats.
- Endpoint Monitoring solutions protect sensitive and confidential company data from loss caused by accidental, negligent, or compromised insiders.
- User & Entity Behavior Analytics software exposes irregularities in system and user activities by leveraging advanced analytics to find suspicious behavior at any endpoint.
- User Activity Monitoring platforms allow companies to identify and respond to malicious or risk activities with automated responses and enhanced, actionable insights.
By leveraging this powerful software, cybersecurity and leadership teams can capture and analyze behavior analytics that provide critical data insights and enforcement options for organizations, regardless of size or sector.
How To Stop and Prevent Insider Threats with Teramind
As an endpoint and user activity monitoring solution built with user and entity behavior analytics, Teramind provides the activity and data tracking capabilities companies need to detect, investigate, and prevent insider threats. As a result, companies can:
- Get alerted and automatically respond to anomalous and malicious behaviors
- Control how company data and files are handled
- Gain total visibility into workforce behaviors and data habits
- Keep an eye on those who have the most access to sensitive information
In addition, Teramind Optical Character Recognition (OCR) allows users to perform high speed searches of session recordings to locate sensitive content appearing on users’ screens, in any format, including in images or videos. Such comprehensive search functions enhance forensic investigations, enabling organizations to locate stealthier, malicious activity.
Taken together, Teramind’s endpoint user behavior solution is a uniquely capable insider threat and data loss prevention solution. Providing powerful insights and workforce analytics, it can be applied to all areas of business.
