Check out the highlights from our most recent update, Platform Release 624! Boasting over 200 updates, we delivered 22 new features and 12 improvements that will boost your productivity and increase the security and reliability of your deployment. See the highlights below and for a full rundown, check out the complete Release Notes here.
Activity Monitoring & Tracking Enhancements
We have added additional monitoring channels and given you more control over existing ones.
Track Even More Communications Channels
Platform Availability: Cloud, On-Premise
Where to Find it On the Dashboard: Monitoring > Online Meetings
Teramind already supports the most popular online meeting apps. Now, you can track even more meetings with the support for WebEx Web:
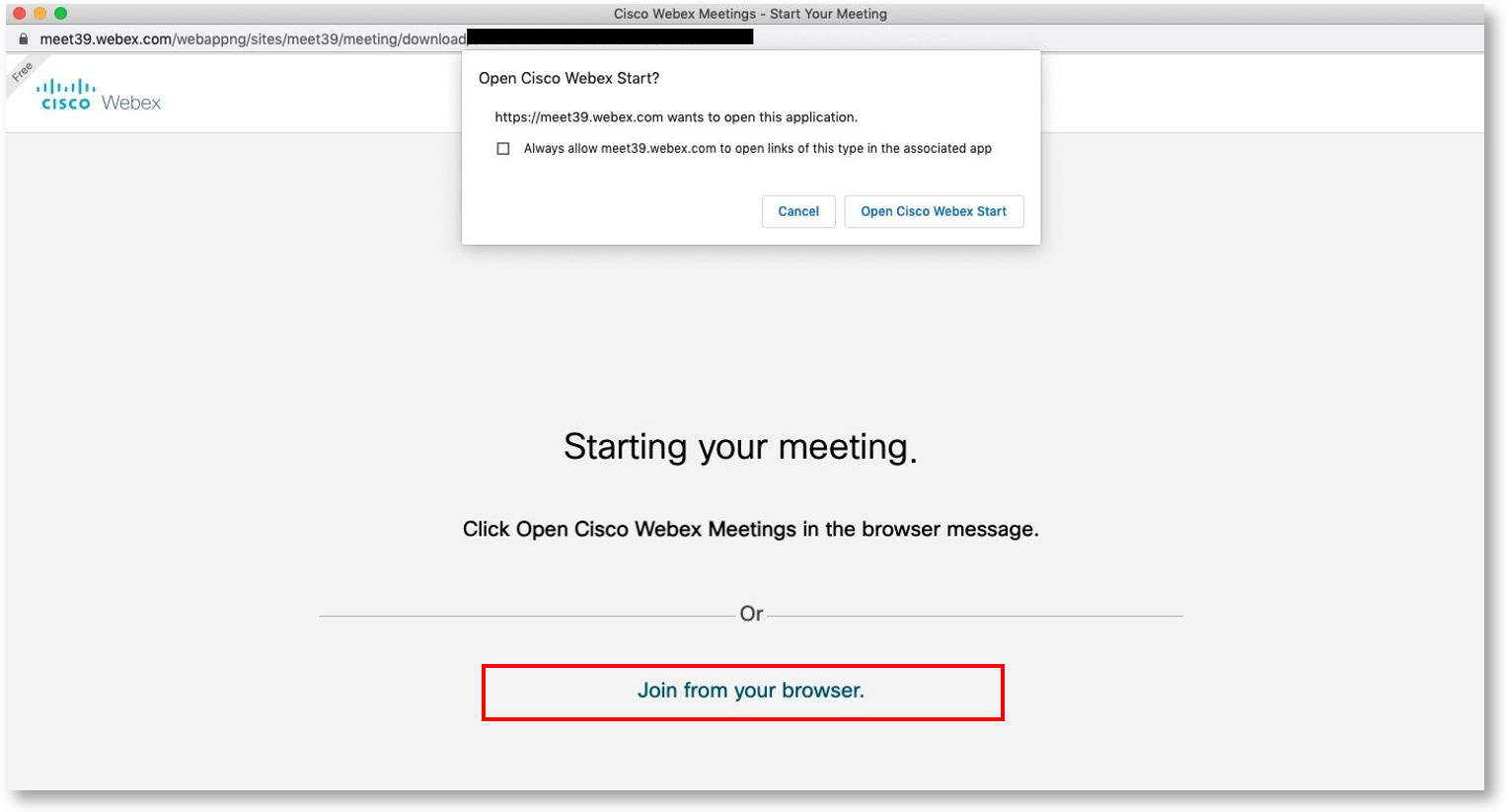
The meetings will show up under the Monitoring > Online Meetings and on the Employee > Activity Log report.
More Powerful Business Intelligence & Analytics
We’ve updated BI Reports to make them powerful and more convenient to use.
Create Rules Quickly from the BI Filters
Platform Availability: Cloud, On-Premise
Where to Find it On the Dashboard: BI Reports > Filter Panel
Now you can create rules directly from a BI Report! We’ve added a new CREATE BEHAVIOR RULE button on the Filter Panel of the BI Reports. Using this feature you can quickly build a rule out of the selected filters:
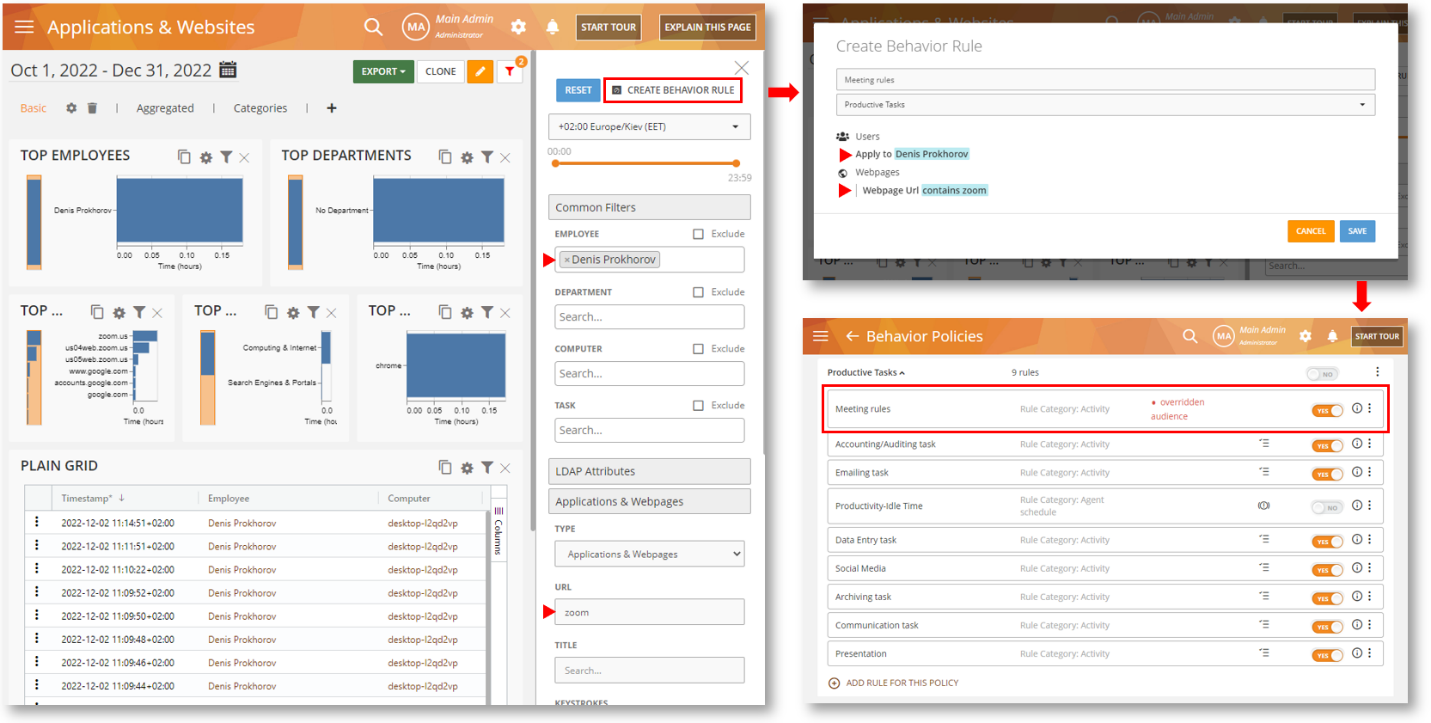
Reduce False Positives and Find Out Exactly What Triggered a Rule
Platform Availability: Cloud, On-Premise
Where to Find it On the Dashboard: BI Reports > Behavior Alerts
The Behavior Alerts BI Report provides even more details now. A new column, Matched triggers was added to the grid widget on the Behavior Alerts report. This column shows what triggered the rule and exactly what rule criteria and conditions were detected when the rule was violated:
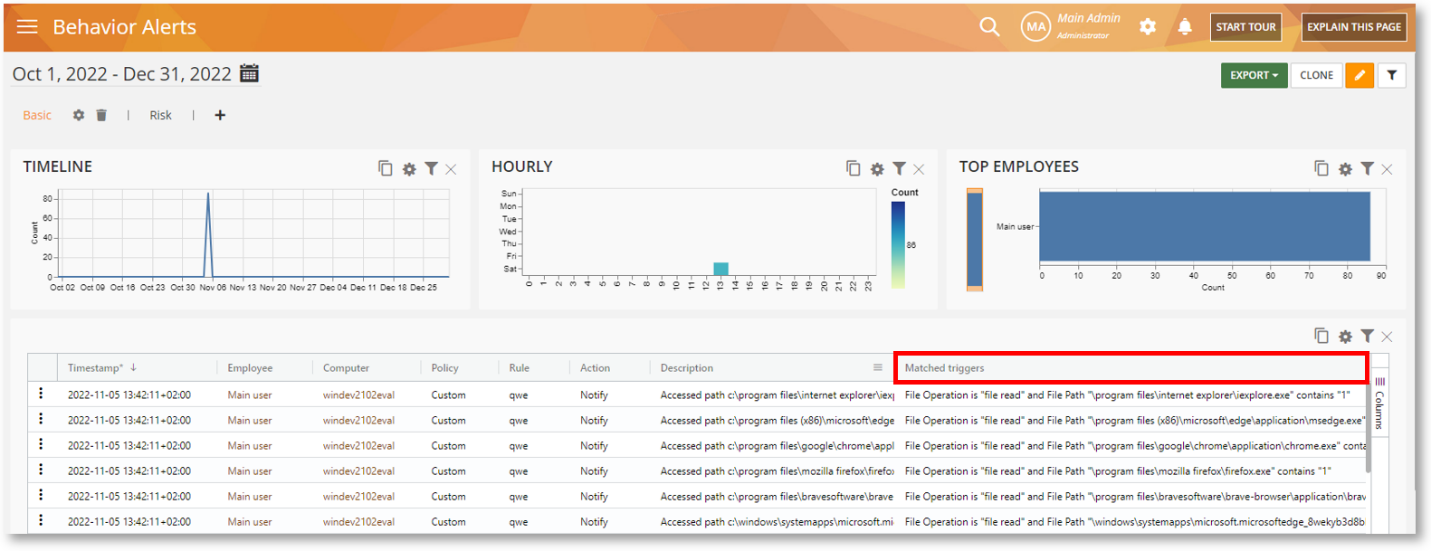
This data point, along with the Description data point will help you better investigate a rule violation incident and gather more contextual insights.
Smarter Behavior Policies & Rules
A new feature was added to the Behavior Policies & Rules for productivity optimization.
Find Out How Engaged Your Employees are with Focused Time Tracking
Platform Availability: Cloud, On-Premise
Where to Find it On the Dashboard: Behavior > Policies > Rules Editor
Frequent task-switching and interruptions can cost employee productivity, increase overall work hours and cause burnout. Our newest monitoring feature, Focused Time tracking provides more context to productivity and better enables you to spot employee burnout and disengagement faster.
To address excessive app and task switching, we’ve introduced two new rule conditions: Focused Time and Total Focused Time to help you find out if employees are maintaining a healthy habit between activity, focus, and breaks.
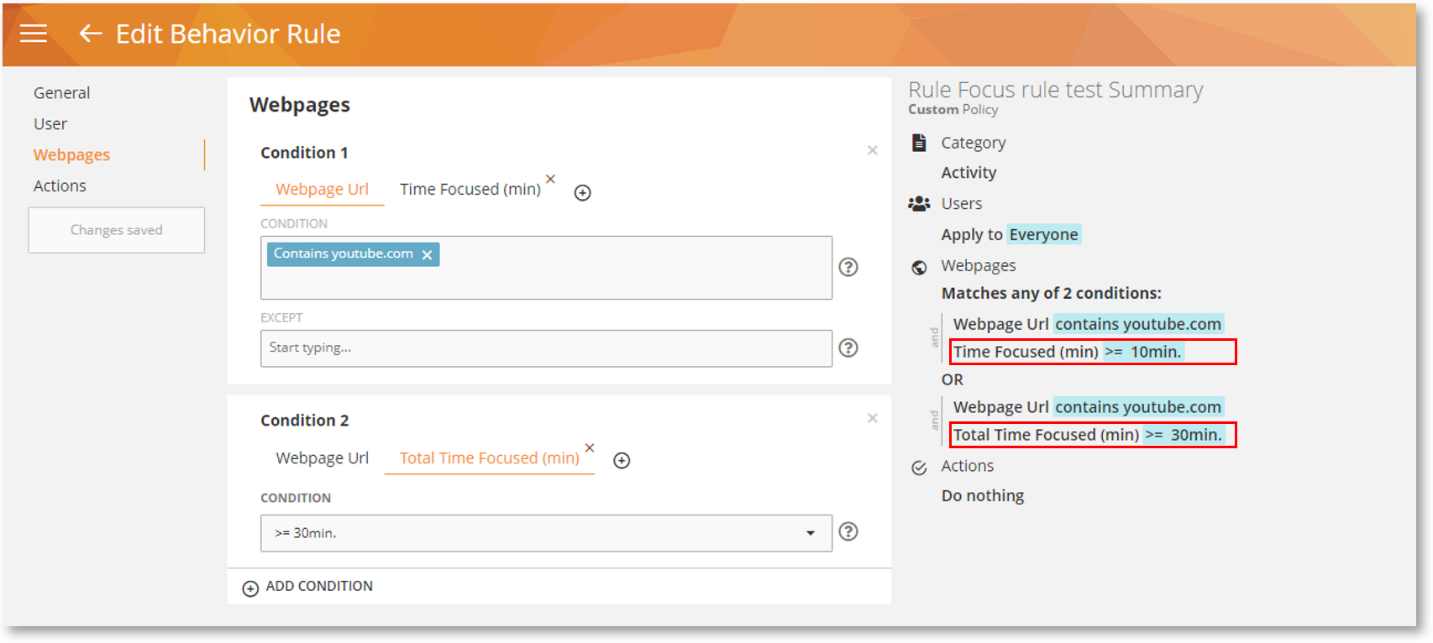
You can use these two conditions with any applications or websites on an Activity-based rule.
Enhanced Security & Compliance
We have added three new security and compliance features and implemented various security improvements and hardening to the overall platform.
Enforce a Strong Password Policy to Secure Your System
Platform Availability: Cloud, On-Premise
Where to Find it On the Dashboard: Settings > Security
We have added a new, Password Policy section on the Security screen:
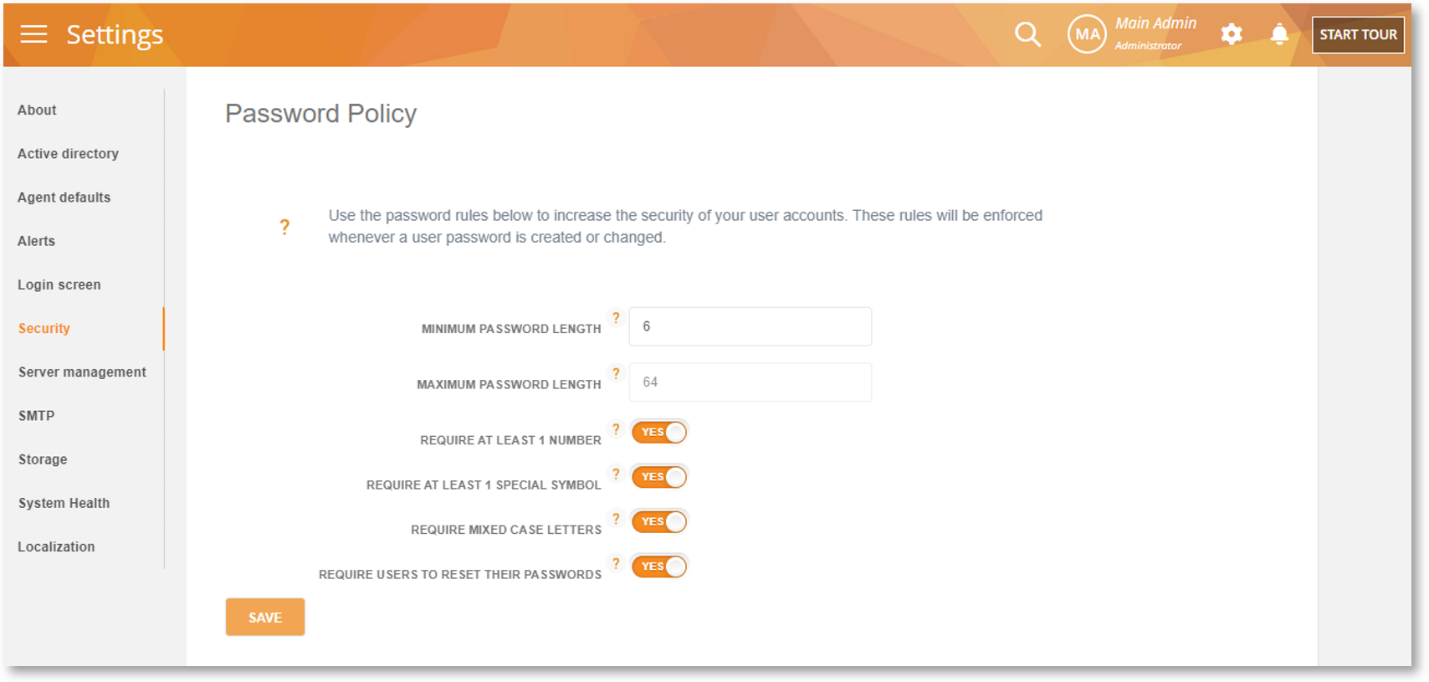
Stronger passwords help prevent your systems from being compromised and your data stolen. A strong password policy is also often compulsory for many compliance and security standards such as ISO 27001, PCI DSS, GDPR, among others.
These new settings will allow you to define a set of rules that will impose strong password creation such as including special characters or a minimum length. The rules created under this policy will be enforced whenever a user password is created or changed.
Disable Password Managers to Minimize Password Leaks and Account Compromises
Platform Availability: Cloud, On-Premise
Where to Find it On the Dashboard: MonitoringSettings > Advanced
Most modern browsers have a password manager that prompts you to save passwords from login forms on websites. While this is convenient, it’s a security risk. The default password management features available in browsers seem secure but a web browser can be broken into, and malware or weak plugins/extensions can expose your saved passwords.
Teramind has introduced an ADVANCED monitoring setting, DISABLE BUILT-IN PASSWORD MANAGER OF KNOWN BROWSERS to disable password managers built into the browsers:
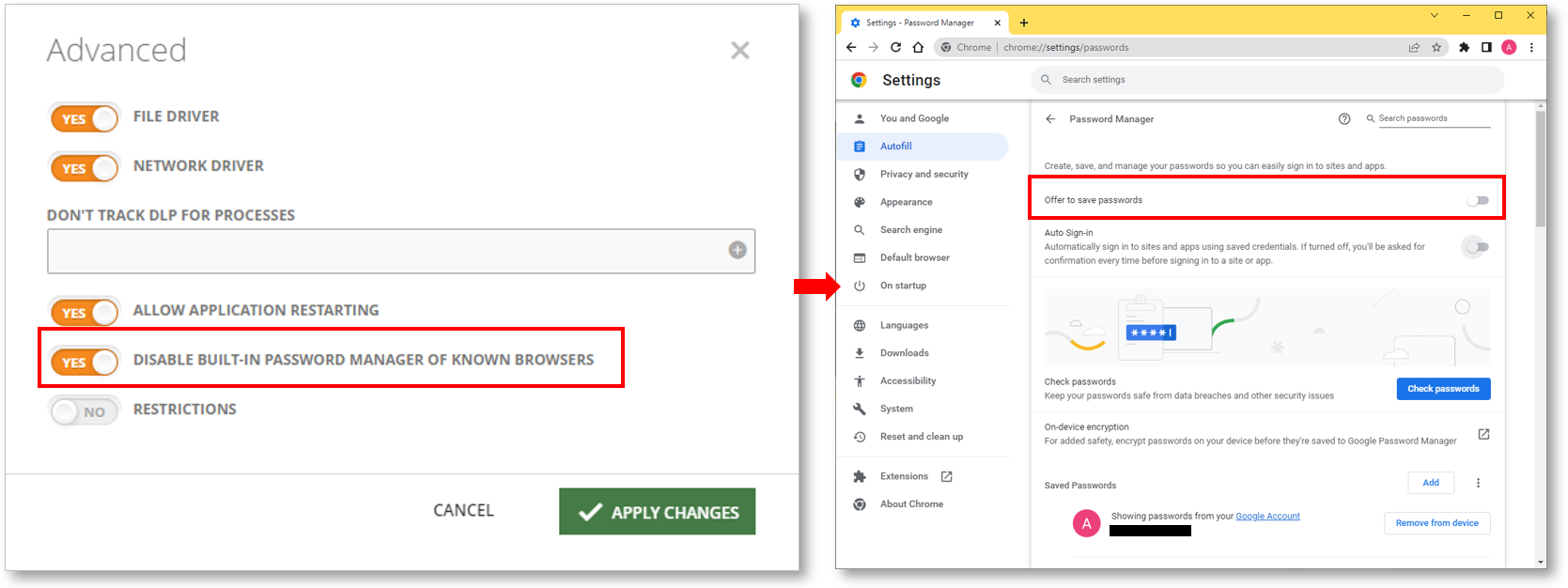
Once enabled, the feature will disable the password-saving option on any supported browsers. The user will not be able to override the option. It’s important to note though, standalone password managers like LastPass will still work.
Enhance the Privacy, Safety, and Security of Your Endpoint with the New Agent Options
Platform Availability: Cloud, On-Premise
Where to Find it On the Dashboard: N/A
We have added several command line options that can be used during the installation of the Agent. These include:
| Ability to Add the Stealth Agent to the Windows ARP list |
By default, Teramind Stealth/Hidden Agent isn’t shown on the Windows list of installed programs (known as the Add or Remove Programs, or ARP list). In this release, a new command line option TMADDENTRYTOARP is added to the installer. If used, it will allow you to add the Stealth/Hidden Agent to the installed programs list on Windows. This is useful if you want the ability to make the Agent visible to a user for transparency purposes and give an admin the ability to remove the Agent using the Windows default uninstaller.
|
| Ability to Change the Agent’s Name |
Currently, the Agent’s default name is dwm.exe. However, Windows also has a service with the same name for its Desktop Windows Manager. We’ve added a new command line parameter, TMAGENTEXE so that you can change the default Agent name to something else in order to make it more clear and avoid confusion with Windows services.
|
| Ability to Anonymize the Usernames |
We have added the ability to obfuscate the usernames with an MD5 hash so that the usernames will be anonymized on the Dashboard. This feature can be enabled with the new command line parameter, TMHASHUSERNAMES.
|
| Ability to Hide the Client IP During an RDP Session |
Usually, when you connect to a computer over an RDP session, the Agent sends the IP address of the client to the server. However, for privacy or security reasons, you might not want to expose the client IP to the server. We have added a command line option, TMHIDERDPCLIENTIP that allows you to hide the client IP address from the server.
|
| Options to Configure the SOCKS Proxy |
We have added several parameters to configure the SOCKS proxy when installing the Agent. They are: TMHTTPPROXY, TMSOCKSHOST, TMSOCKSPORT, TMSOCKSUSER, TMSOCKSPASSWORD, and TMUSESOCKS5.
|
Mac Enhancement Continues
We continue to add features and capabilities to our Mac Agent to bring it closer to the Windows Agent in terms of feature parity.
Monitor Network Activities
Platform Availability: Mac / Cloud, On-Premise
Where to Find it On the Dashboard: Monitoring > Network Monitoring
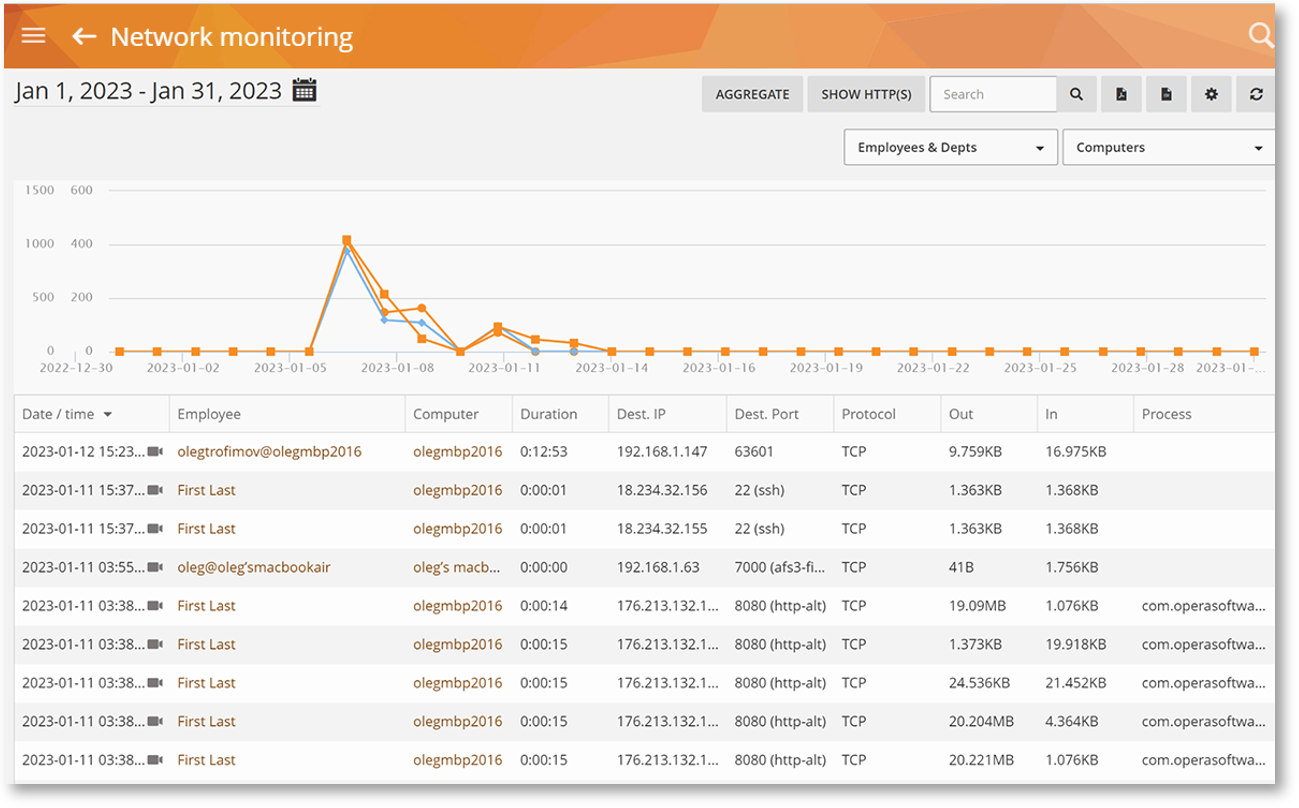
The Mac Agent is now able to monitor TCP/IPv4-based network connections on macOS 11 (Big Sur) and later:
Detect Network Anomalies and Limit Access with Networking Rules
Platform Availability: Mac / Cloud, On-Premise
Where to Find it On the Dashboard: Behavior > Policies > Rules Editor
Networking Activity-based rules detect what data are being sent/received over the network. You can set conditions like Application Name, Remote Host, Remote Port, Bytes Sent, and Bytes Received:
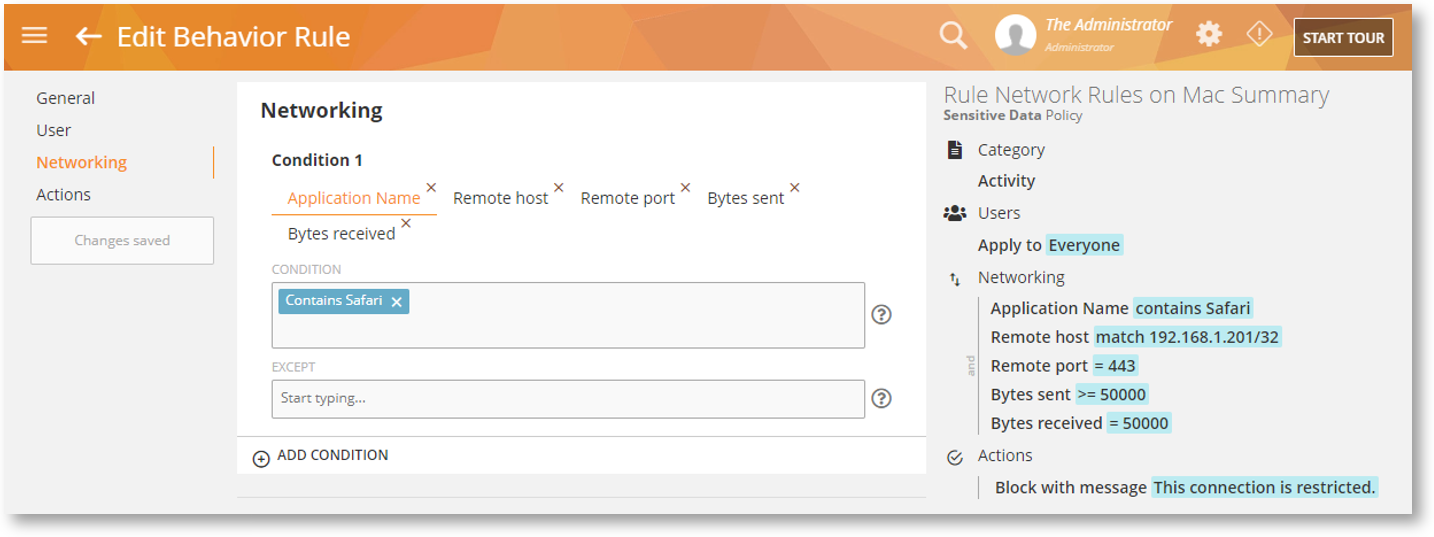
With these conditions, you can implement network security-related rules. For example, you can restrict outgoing internet traffic, limit network access for instance by disabling login via RDP (Remote Desktop Protocol), get notified when abnormal network activity (i.e. sudden spike in network traffic) is detected which might indicate an intrusion, and more.
Stop Drip Incidents with the Lock Out User Rule Action
The Mac Agent now supports the Lock Out User rule action:
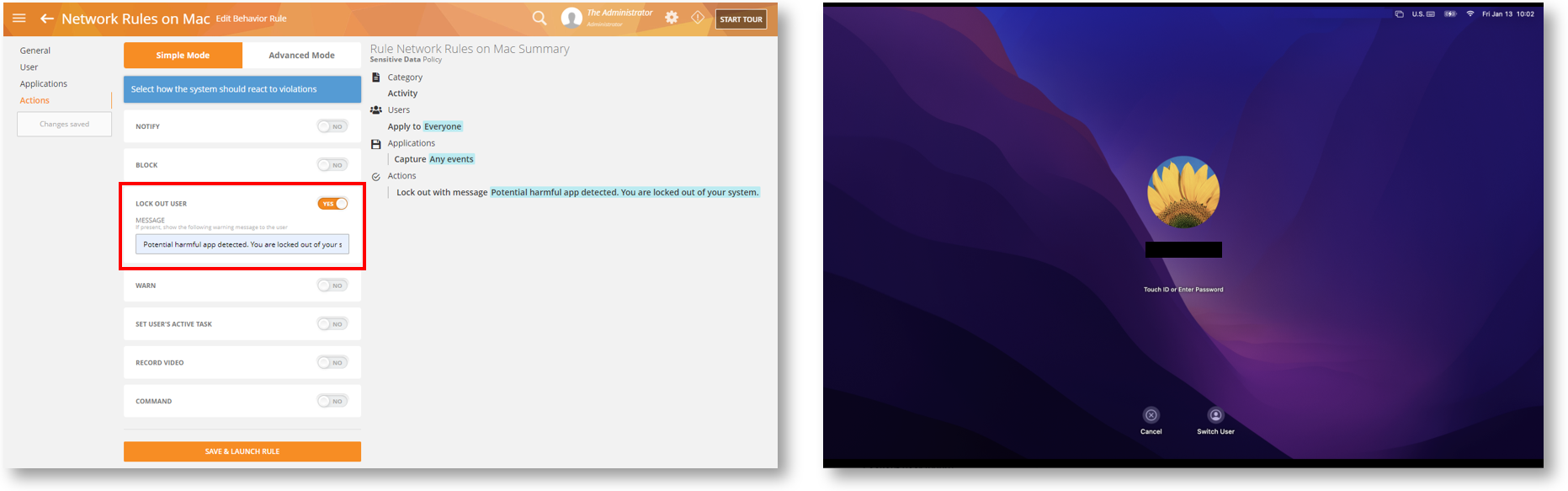
This action is useful when you want to lock out a user from their computer when a dangerous rule violation incident is detected that might lead to other potential incidents (drip incidents) or growing threats). This way, the user cannot cause further harm with subsequent activities. For example, as soon as you detect that a user downloaded a file from a suspicious website, you can lock them out so they cannot open the file which might lead to a potential malware infection.
Better Enterprise Integrations with API Enhancements
We’ve introduced several new API calls and enhanced a few others to improve the API experience for enterprise users and IT developers. For example:
| New OCR Search POST |
A new API POST functionality elastic-search-screen is added to the Teramind API which will allow you to search records directly in the Teramind Elasticsearch database.
|
| New Schema, Validation and TypeScript Types Generation | We have added support for better request schema, user input validation and TypeScript types generation. This will help you use the Teramind API more effectively and troubleshoot issues quicker. |
Other New Features & Improvements
This release also comes with feature enhancements and bug fixes for an easier and more streamlined platform experience and navigation. See the highlights below and check out the full list here.
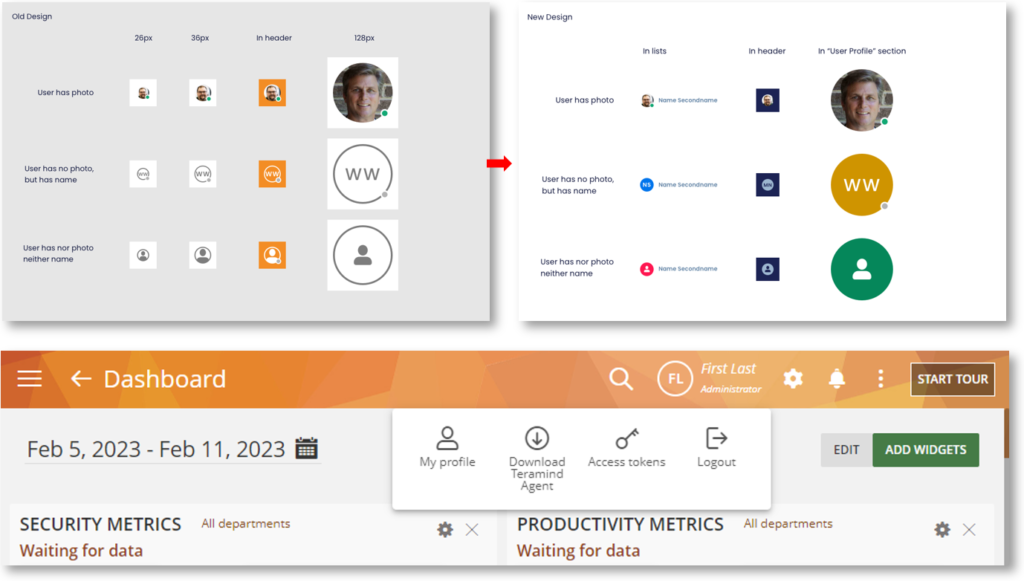
UI Enhancements
We’ve updated the user avatars, some of the menu items, icons, scrollbars, etc. to make them more modern and responsive. We’ve also added the ability to distinguish users with the same name.
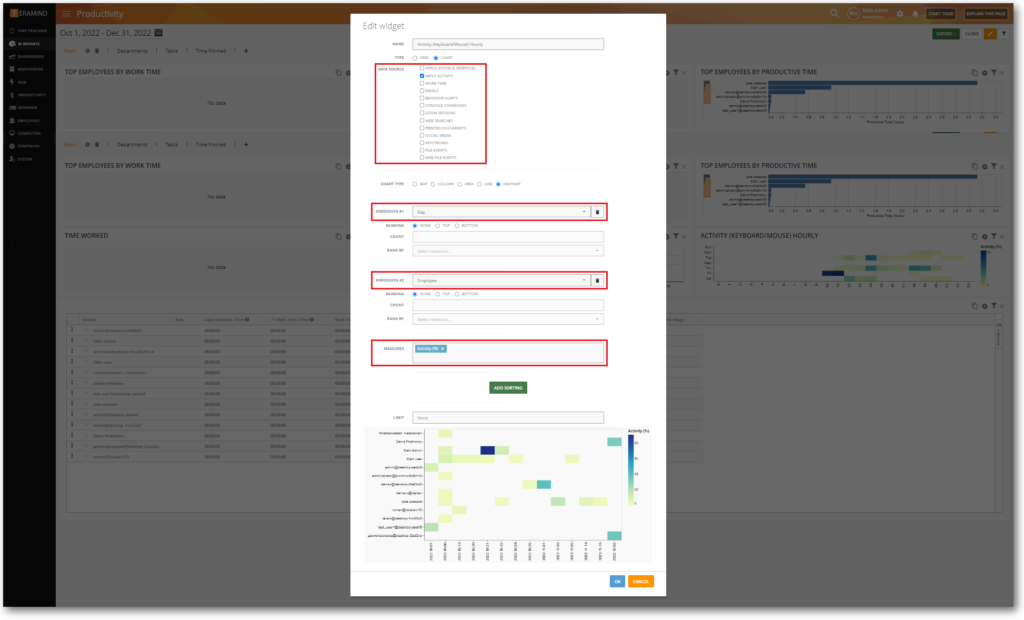
Improved Heatmap Chart Widget
Changes were made to the Heatmap Chart Widget so that it will now enforce proper configuration such as selecting the right data source, dimensions, and measures.
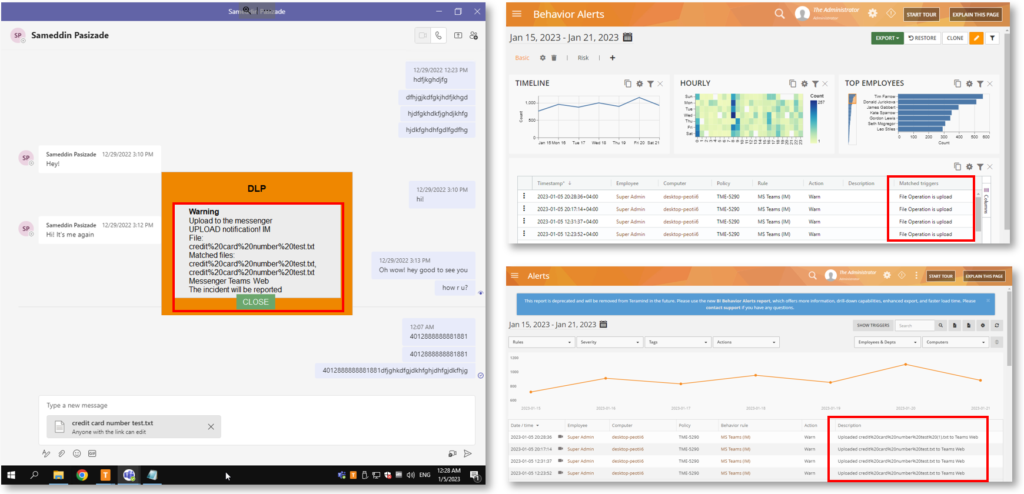
Better Websites and Social Media Tracking
Teramind tracking system will now use the SNI (Server Name Indicator) to handle browsers that use HTTPS proxy servers over TLS protocol. We’ve also updated the Content Sharing rules so that IM activities such as file uploads will show more contextual information on the Behavior Alerts report to reduce false positives.
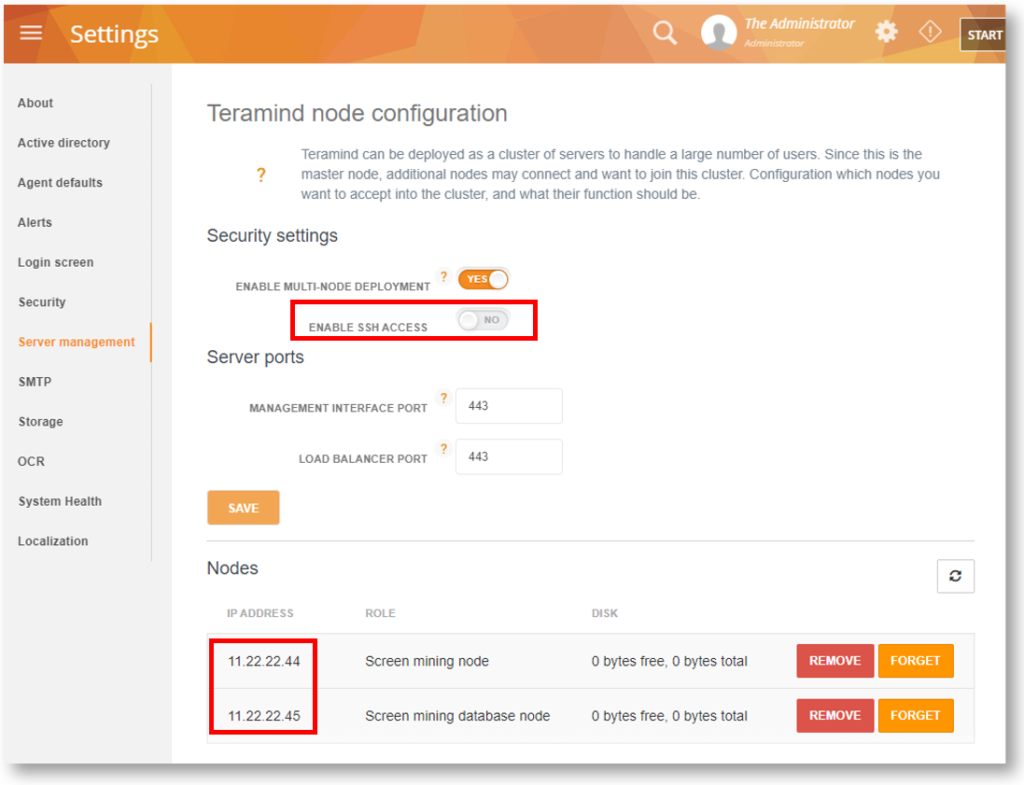
Server Improvements
We’ve improved the SSH access control so that when disabled, it will now block access to all nodes instead of just the app server. Additionally, we have improved the server memory management to handle stability during peak loads. Changes were also made to the OCR mining process to make it more stable and responsive.

Agent Improvements
Changes were made to the Teramind start-up sequence so that the Teramind kernel driver will no longer automatically start when Windows boots up. Instead, the Agent will run the service in a just-in-time manner. The Agent update process is also improved to make it more efficient.
How to Update to Release 624:
Cloud Customers
Cloud customers will be automatically updated to the latest Platform release. If you enabled the Agent Auto-Update feature, the Agent will be automatically updated. Otherwise, you can download it from your dashboard.
On-Premise / Private Cloud Customers
On-Premise, AWS, or Azure customers can download the updated files from our Self Hosted Portal. You can then apply the server update through the dashboard and update to the new Agent remotely.
Discover what Teramind can do for you!




