Check out the highlights from our most recent update, Platform Release 650. This is our biggest release so far with 457 features, improvements, and bug fixes. See the highlights below. For a full rundown, check out the complete Release Notes here.
Business Intelligence
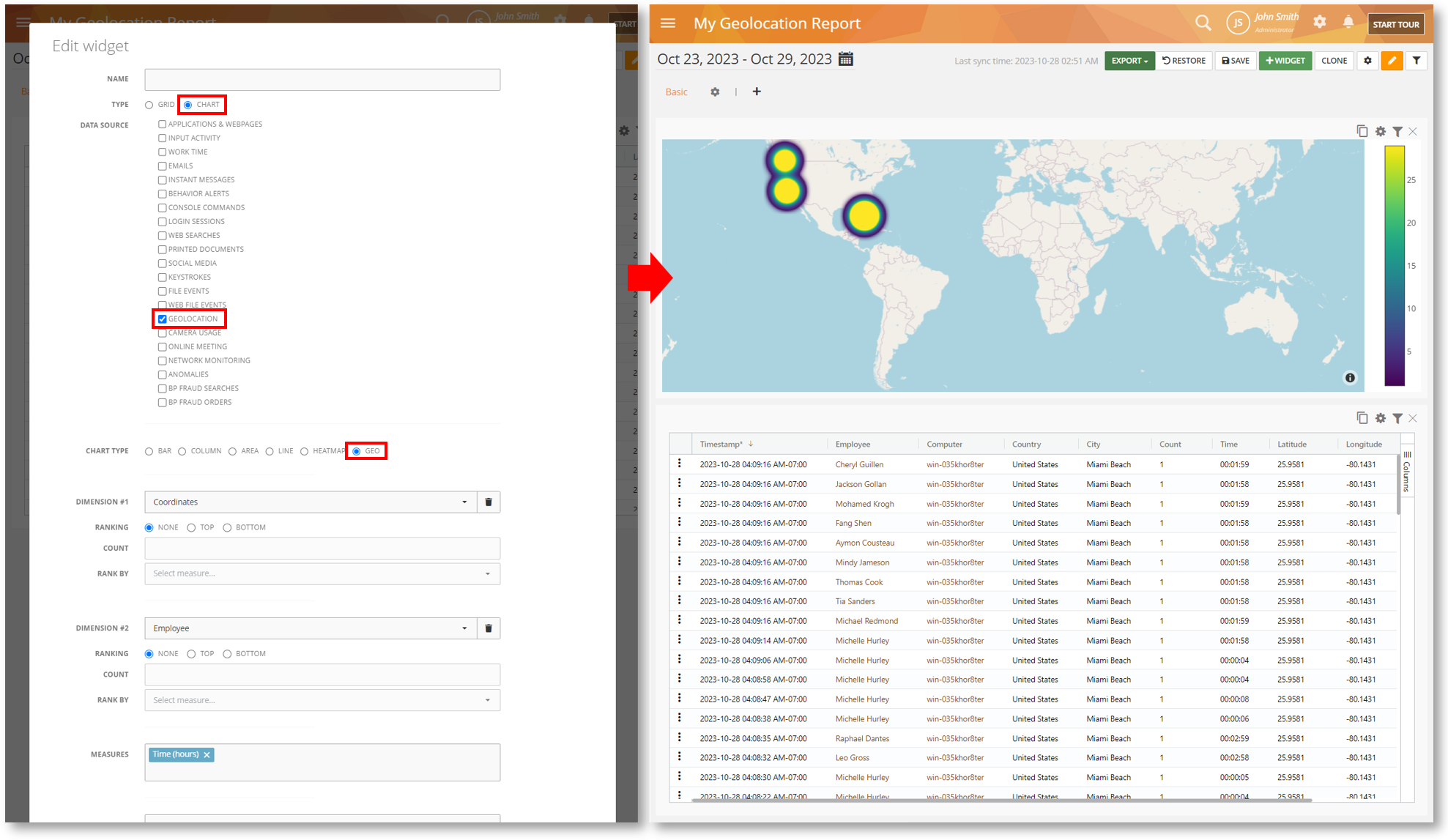
Map Employee Locations with the Geo Chart Widget
We have added a new Geo chart widget that will let you plot geolocation coordinates on a map. This will help you visualize employee whereabouts instead of trying to figure out the location coordinates.
You can add the Geo widget to any custom BI reports including a clone of the existing Geolocation report. You can plot the coordinates with a secondary dimension such as Employee, Computer, etc. and measure it against Count, Time, Latitude, Longitude, Error Radius, etc.
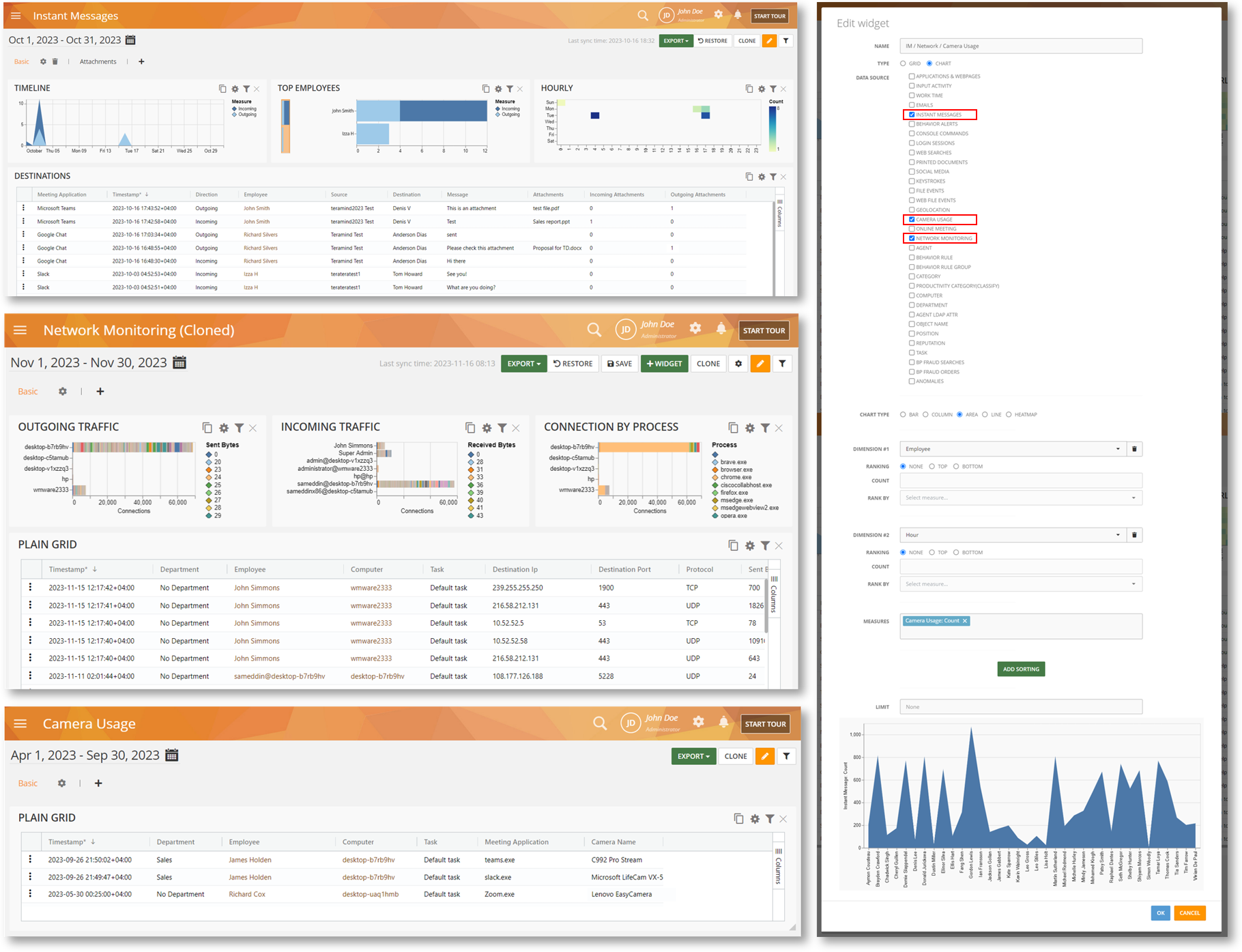
Migrate to Better Analytics and Reporting with the New BI Additions
We have added Instant Messages, Network Monitoring and Camera Usage reports (and associated Data Sources) to the BI Reports. Previously, these were only available under the Monitoring reports.
Migrating to the newer, BI versions of these reports will help you conduct thorough analysis and flexible reporting with powerful tools such as advanced filters, customized widgets, charts and more. You can even create your own custom reports.
Behavior Rules
Detect Sensitive Information on the Fly with the Keystrokes Content Sharing Rule
Previously, you could detect keystrokes and identify texts or words with the Keystrokes Activity Rule. Now, with the new Keystrokes Content Sharing Rule, you can compare keyboard inputs against sensitive information using the Predefined Classified Data (e.g., Financial Data, Personally Identifiable Data, Health Data, etc.) or your own custom data definitions.
This rule will be useful to detect data exfiltration attempts or implement etiquette rules (e.g., warn users when they type any swear words in a chat conversation) in virtually any applications or documents in real-time.
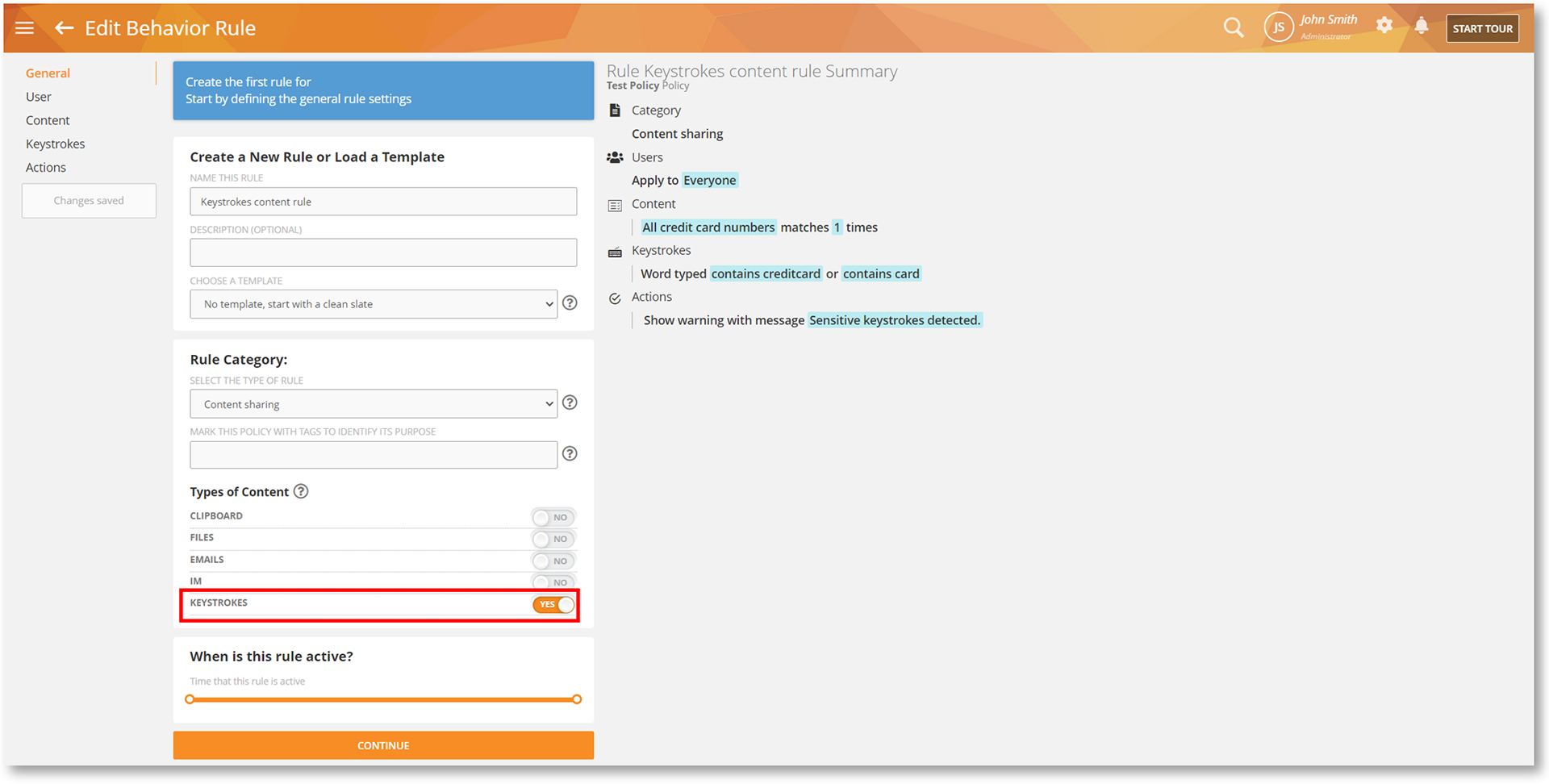
Discover System Incidents, Security Gaps and More with the Windows Log Event Rule
Windows keeps a chronological log of events for application activities, system changes, security incidents, hardware triggers, etc.
We have added a new, Windows Log Event Activity Rule that will help you detect these events.
The ability to detect these events is a very powerful tool because it allows an administrator to identify issues with the computer, discover security gaps and stop potential threats.
Windows Log Event rules will allow you to detect these Windows events by their IDs. For example, an Event ID of 4738 is triggered every time a user object is changed. This type of change might indicate malicious intent, a precursor to account compromise or insider attacks. In this case, you can use the Windows Log Event to detect such events and send an alert to an admin to take action.
For step-by-step instructions on how to create such as rule, please check out the Rule Sample 6: Using Windows Log Event to Detect Software Installation/Uninstallation section in the Rules Guide.
Administration and Management
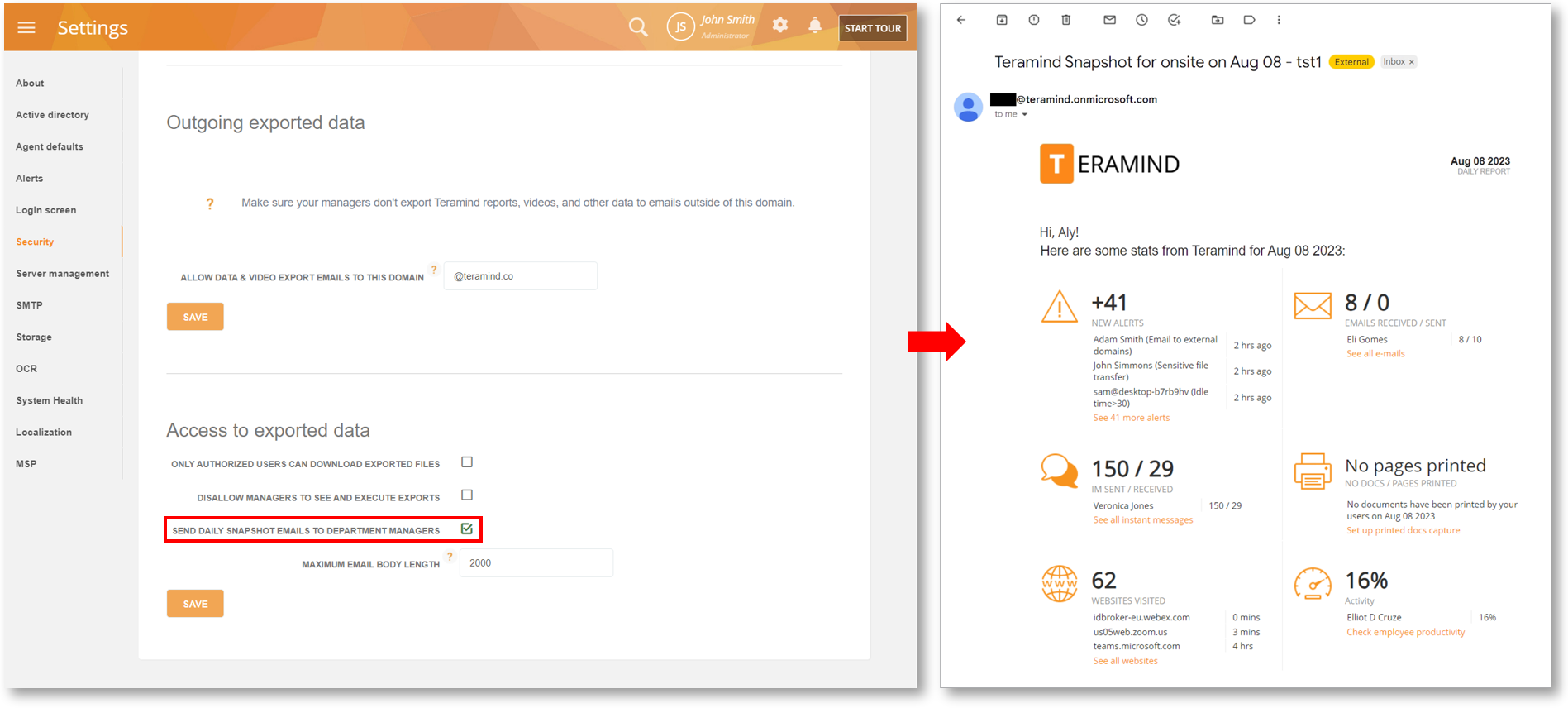
Provide Department Managers Better Team Visibility with the Daily Snapshot Report
Previously, only administrators received the Daily Digest / Daily Snapshot email report. Now, you can enable this feature for Department Managers too – giving them better visibility into their teams’ performance on a daily basis.
You can use the SEND DAILY SNAPSHOT EMAILS TO DEPARTMENT MANAGERS option on the Settings > Security screen to enable/disable this feature.
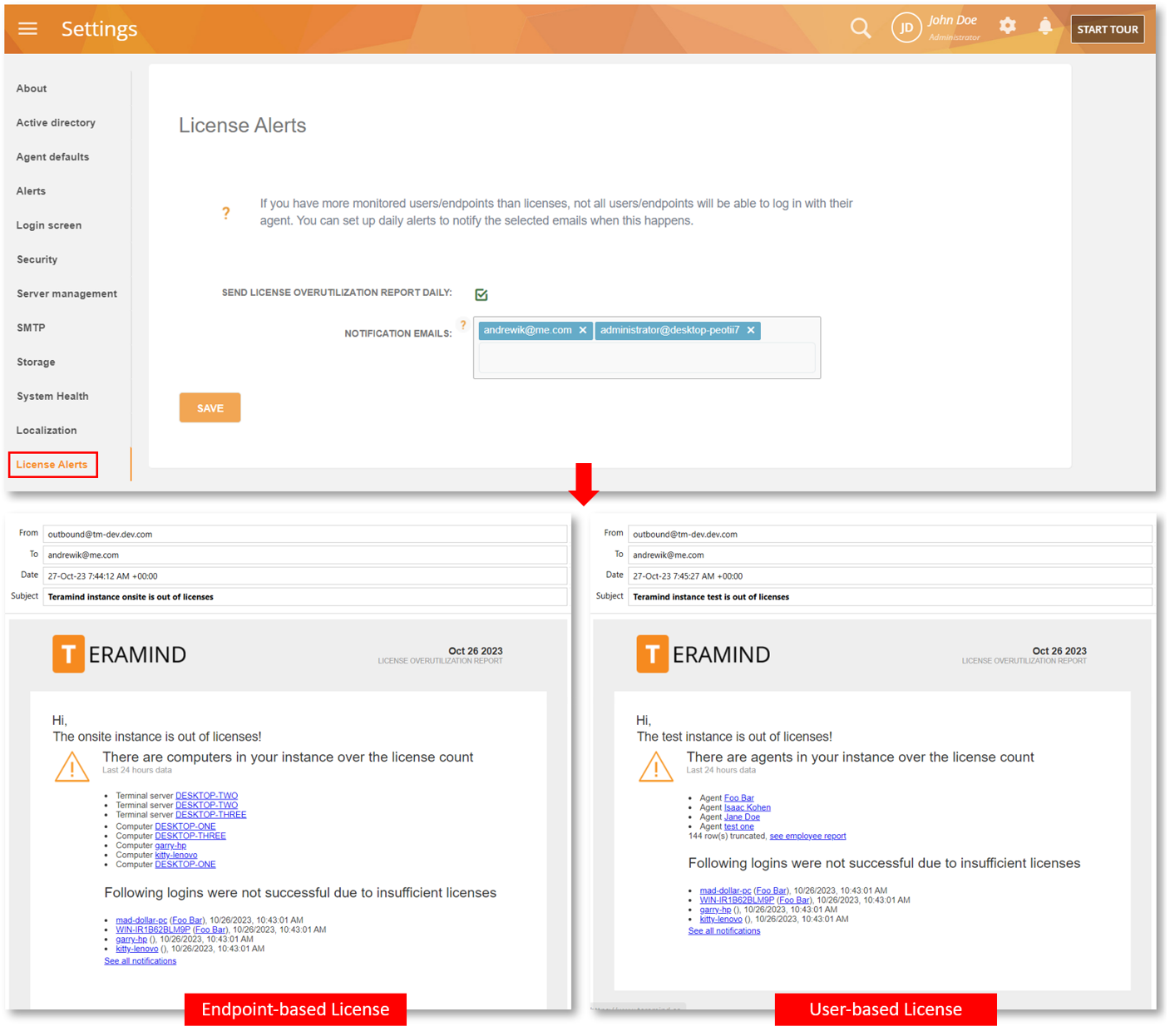
Don’t Miss Out, Get Notified when License Limit Causes Monitoring to Stop
When your users/endpoints exceed the license count, monitoring will stop for them.
We have added a new tab, License Alerts on the Settings screen which will let administrators receive email alerts when users/computers exceed the allotted number of licenses. This will help you take immediate action so that you don’t miss out on those users/computers.
Enterprise Integrations
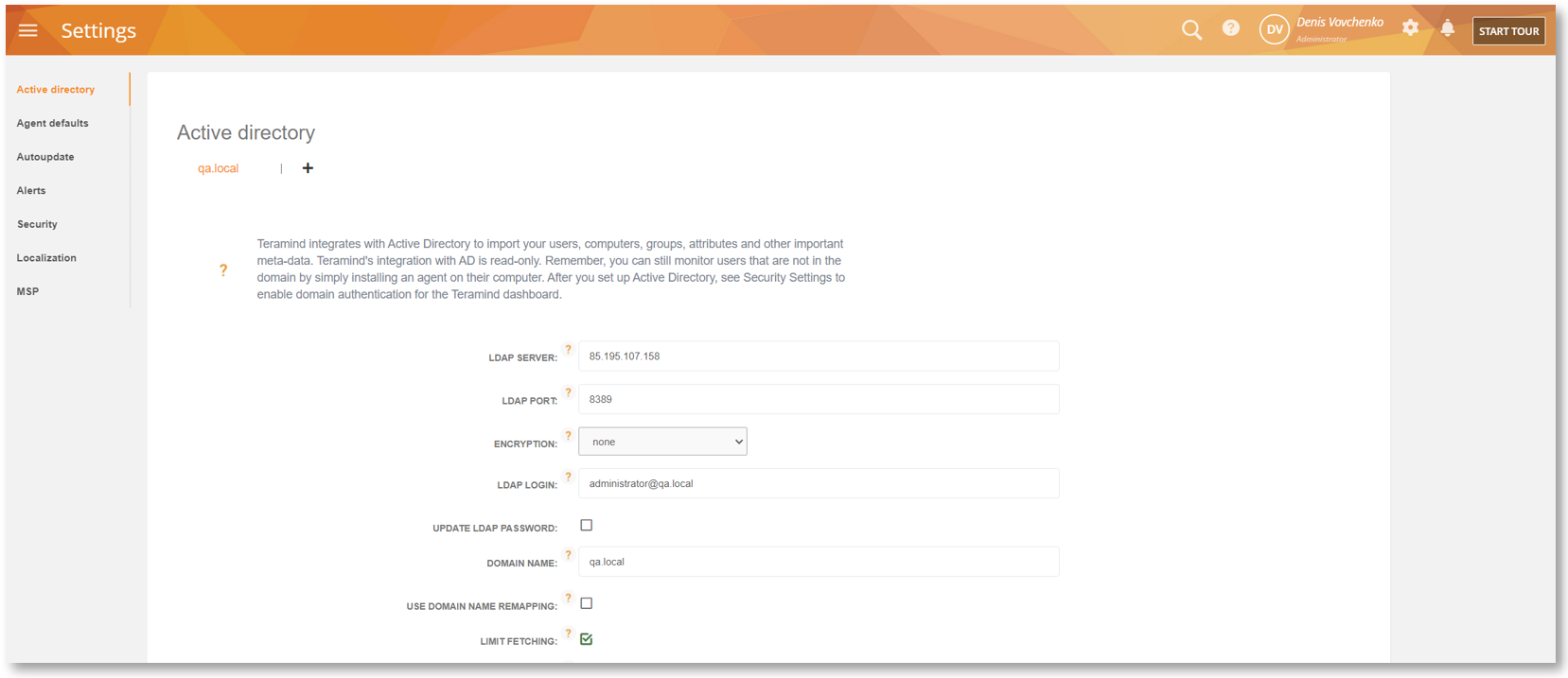
Get Active Directory on Your Cloud Instance
We have added support for Active Directory integration on Cloud instances. Previously, only On-Premise/Private Cloud deployments and custom deployments had AD support.
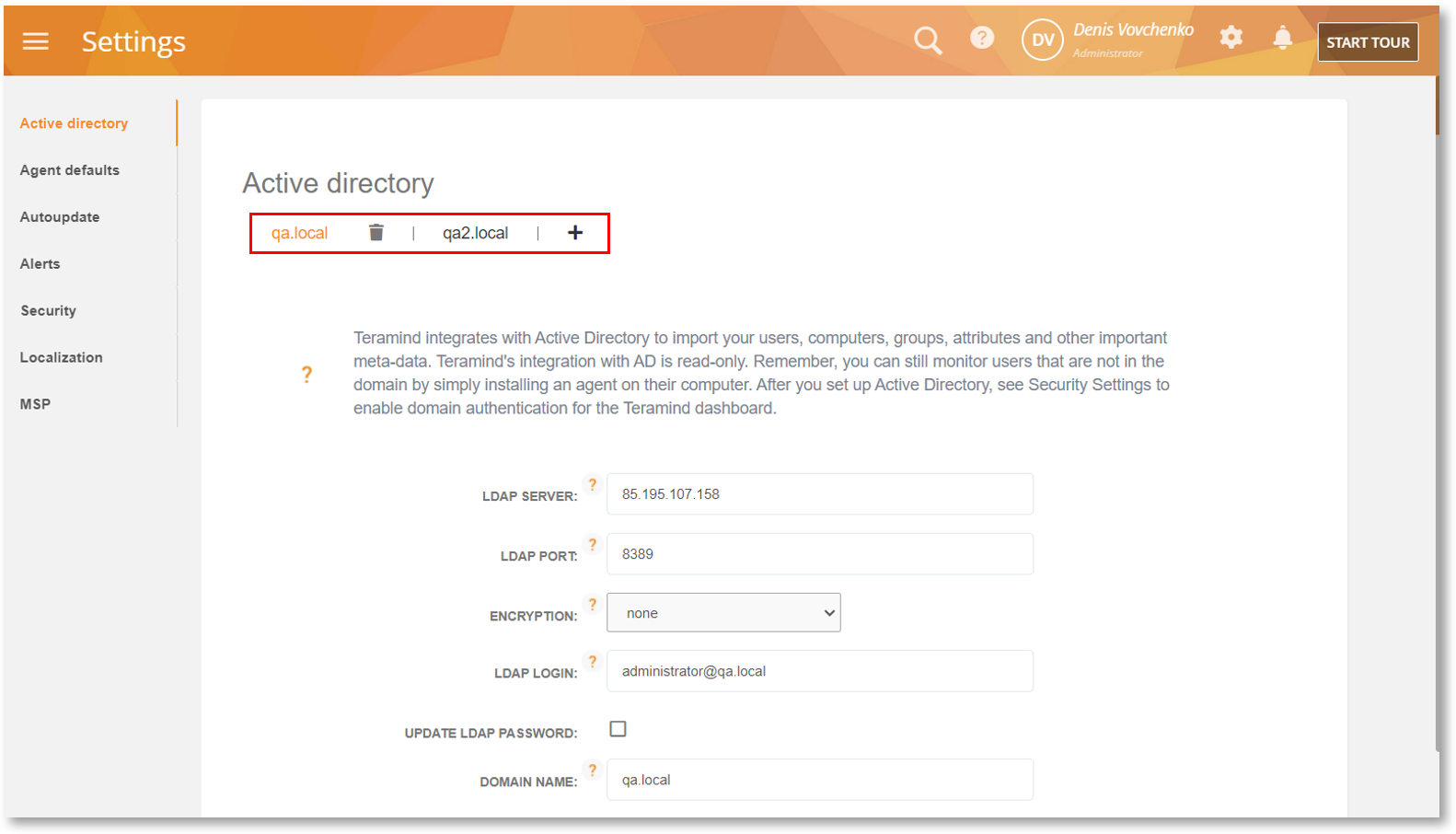
Sync with Multiple AD Domains/Servers
We have added support for multiple domains/servers in Active Directory. This will help you bring your users/computers from different organization units into Teramind without having to switch accounts, go through a complicated setup process, or domain merging.
You can add multiple domains/servers tabs and configure them independently from the Settings > Active Directory screen. Use Plus + icon to add a new tab and the Trash Can icon to remove a tab.
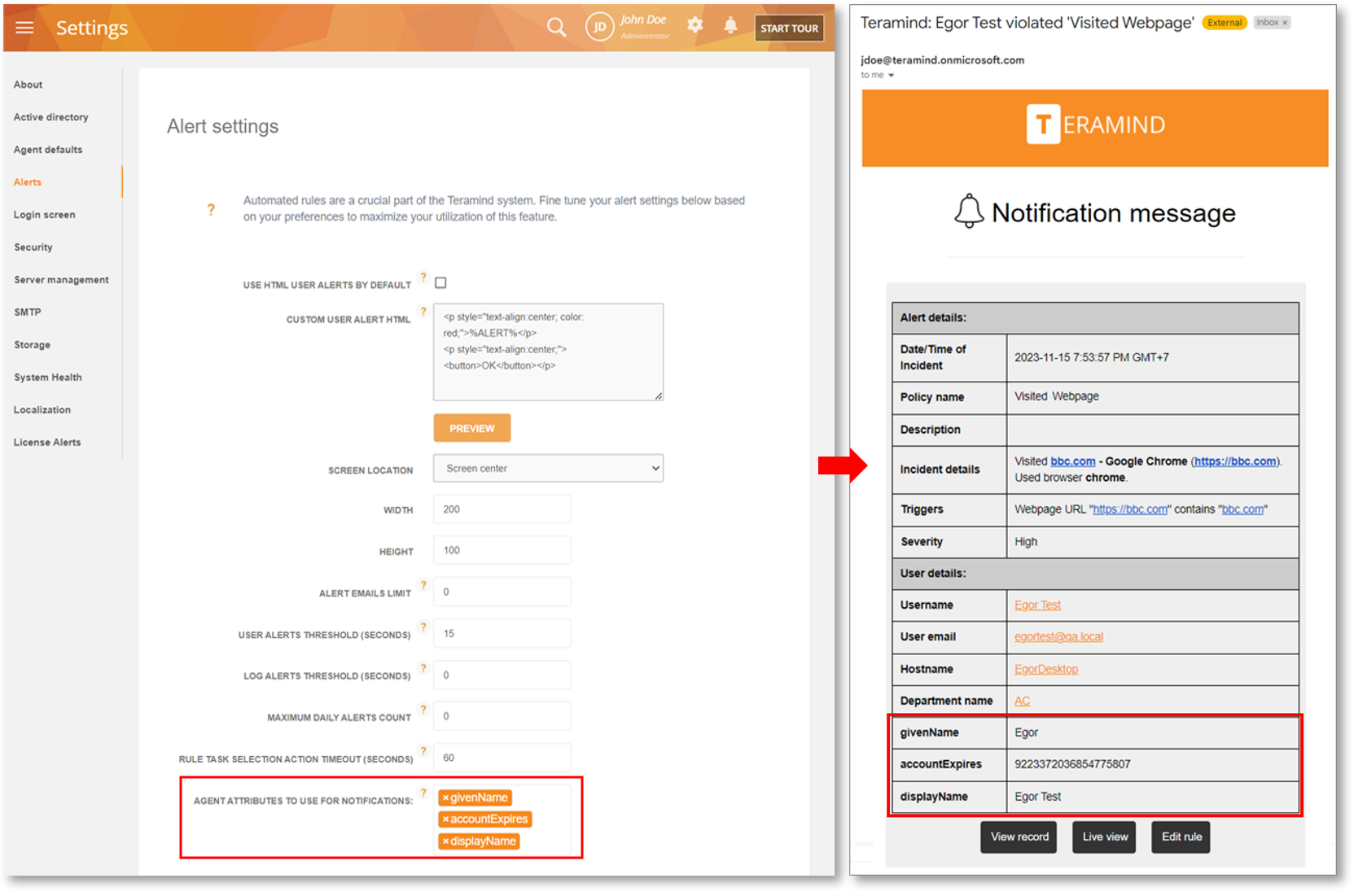
Get Better Context with Attributes in Alert Notification Emails
We have added a new Alerts option, AGENT ATTRIBUTES TO USE FOR NOTIFICATIONS to the Settings > Alerts screen. This option will allow you to choose LDAP attributes that will be added to the rule alert notification emails giving you better context about the incident and user(s) involved.
Mac
Extend Websites Monitoring to Firefox and Opera Browsers
Previously, Mac Agent could monitor user activities on the Apple Safari, Google Chrome and Brave browsers only. Now, we have added support for Firefox and Opera browsers allowing you to extend your web monitoring capabilities.
You will be able to see website activities on reports like BI Reports > Applications & Websites, Monitoring > Web Pages & Applications, etc.
Create Flexible Websites Rules with the Webpage Title Criterion
The Webpages rule now supports the Webpage Title criterion allowing you to create more flexible website-based rules quickly and easily. For example, specifying “news” will detect both https://www.bbc.com and https://edition.cnn.com as they both contain “news” in their page titles. Whereas, with the Webpage URL criterion you will have to specify individual URLs for the sites.
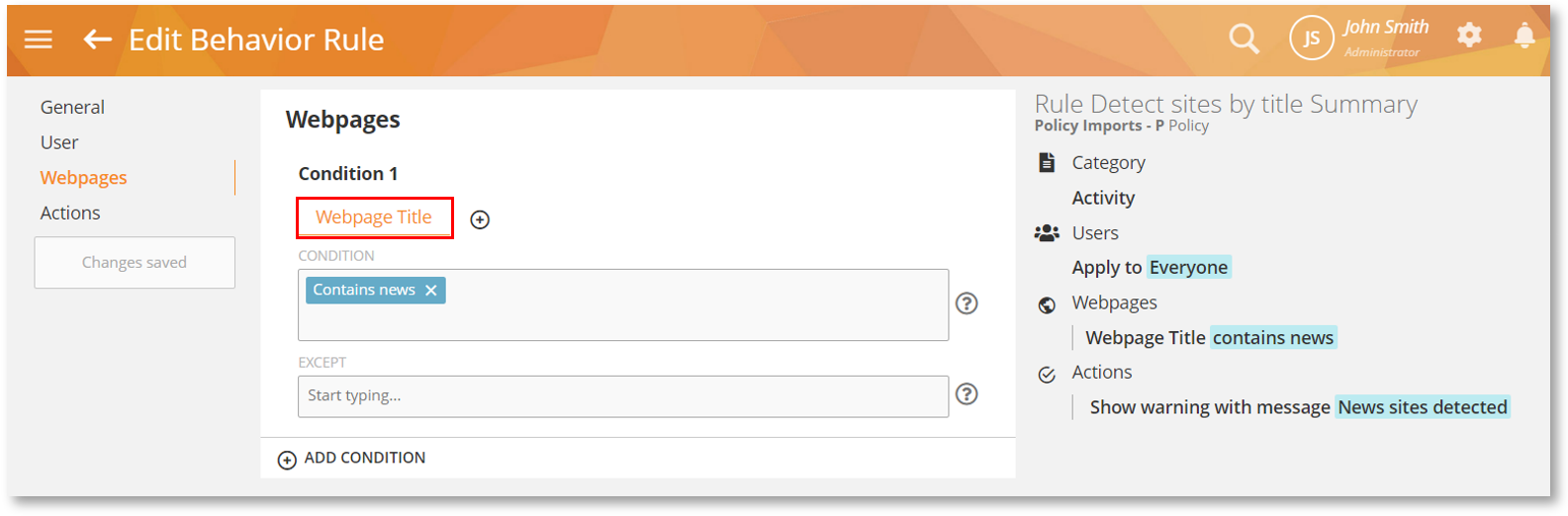
To learn more, check out the Activity Rules > Webpages section of the Rules Guide.
Monitor Locked Session for Continuous Time Tracking
We have enabled support for the RECORD LOCKED SESSIONS option available on the Monitoring Settings > Monitoring Profile > Screen panel.
It will allow you to continue recording and track time even when the user locks their computer. It will also work when the screen saver gets activated, or when an RDP (remote desktop session) window is minimized.
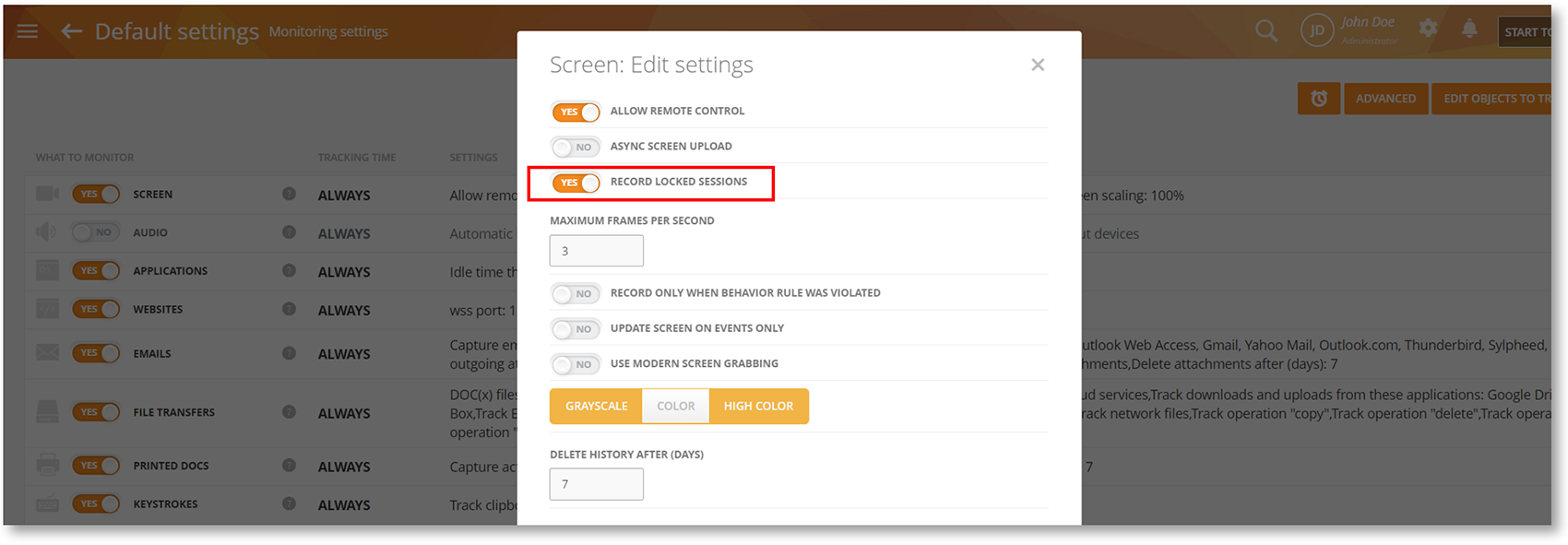
Please note that this feature affects how the user’s work time, idle time, session time, etc. are calculated and what information is displayed on the Dashboard. To learn more, check out the Monitoring Settings > Editing Screen Settings section of the User Guide.
Limit Offline Recording with the Buffer Size Option
We have enabled support for the OFFLINE RECORDING BUFFER SIZE (MB) option available on the Monitoring Settings > Monitoring Profile > Offline Recording panel.
With this option, you will be able to configure how much disk space the Agent will use before it stops capturing the screen recordings in offline mode.
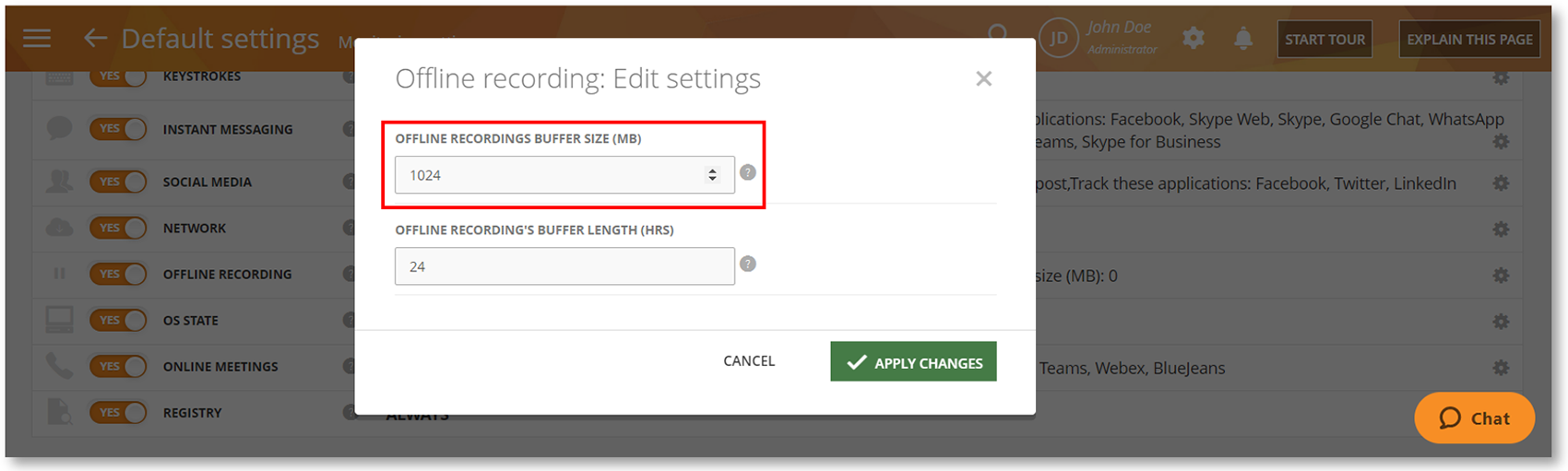
To learn more, check out the Monitoring Settings > Editing Offline Recording Settings section of the User Guide.
Detect Data Leaks by Tracking File Transfers on External Drives
We have enabled support for the TRACK EXTERNAL DRIVES option available on the Monitoring Settings > Monitoring Profile > File Transfers panel.
External drives are a common vector for data exfiltration. With this feature you will be able to easily identify such activities from reports like the BI Reports > File Events, Monitoring > File Transfers and Employees > Employee’s Details > File Transfers tab.
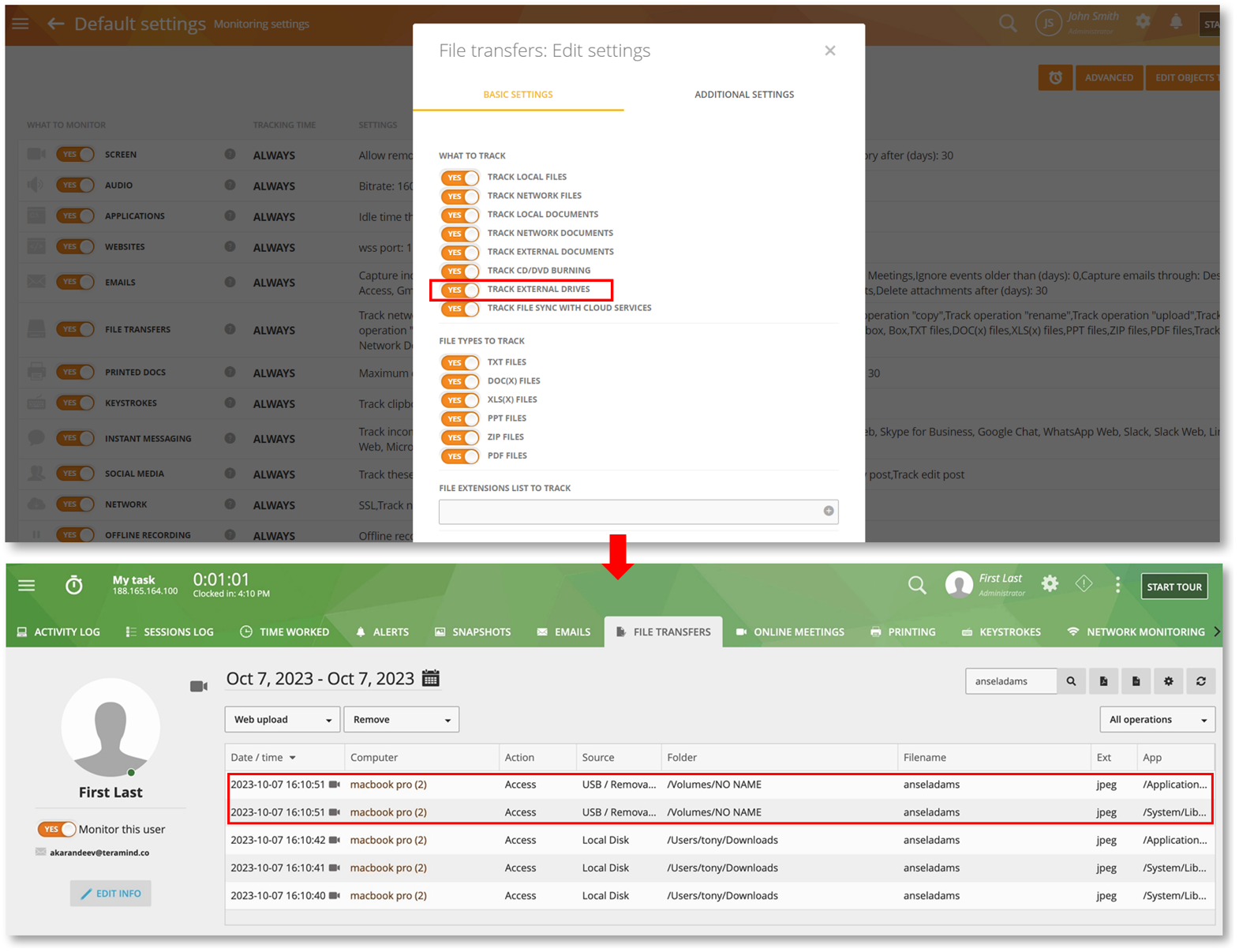
To learn more, check out the Monitoring Settings > Editing File Transfers Settings section of the User Guide.
Connect Over a SOCKS Proxy for Security and Performance
Many organizations use SOCKS proxies for security, compatibility, performance, or anonymity purposes. Previously, Teramind Agent couldn’t connect to its server if you were using any SOCKS proxy.
Now, we are adding several Agent Configuration Parameters (socks-server, socks-port, socks-user, socks-password, socks-version5) that will let you connect to a SOCKS server easily.
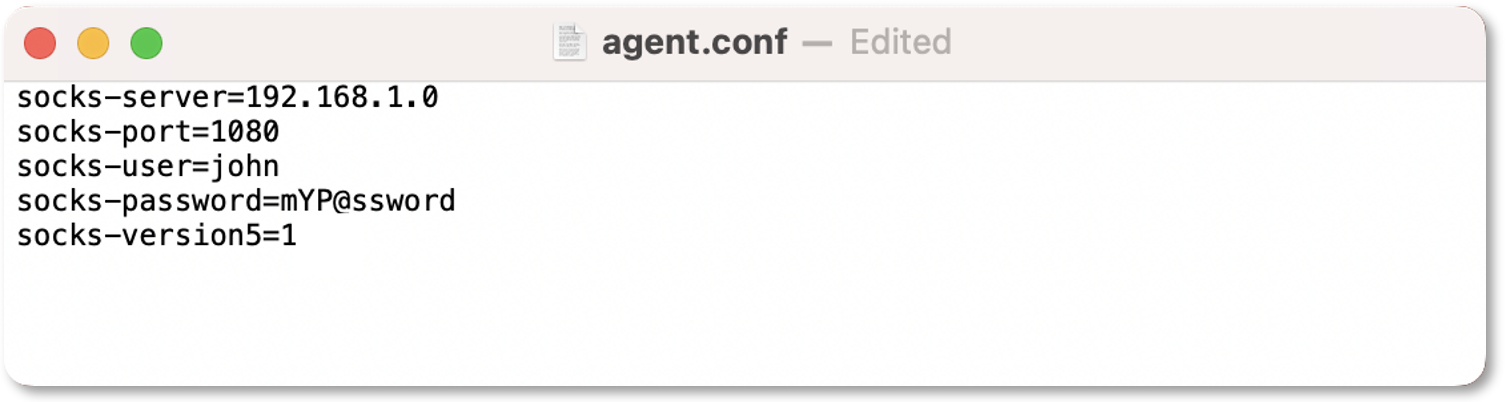
To learn more, check out the Agent Installation/Configuration Parameters (Mac) section in the Agent Installation article.
Exclude App Bundles from Network Monitoring for Privacy and Performance
We have introduced a new Agent Configuration Parameter (network-exclude-bundles) that will let you exclude application bundles from the network driver. This can be useful if you want to exclude certain apps/services from network tracking for privacy or security purposes. The feature can also be used for performance tuning and troubleshooting purposes.
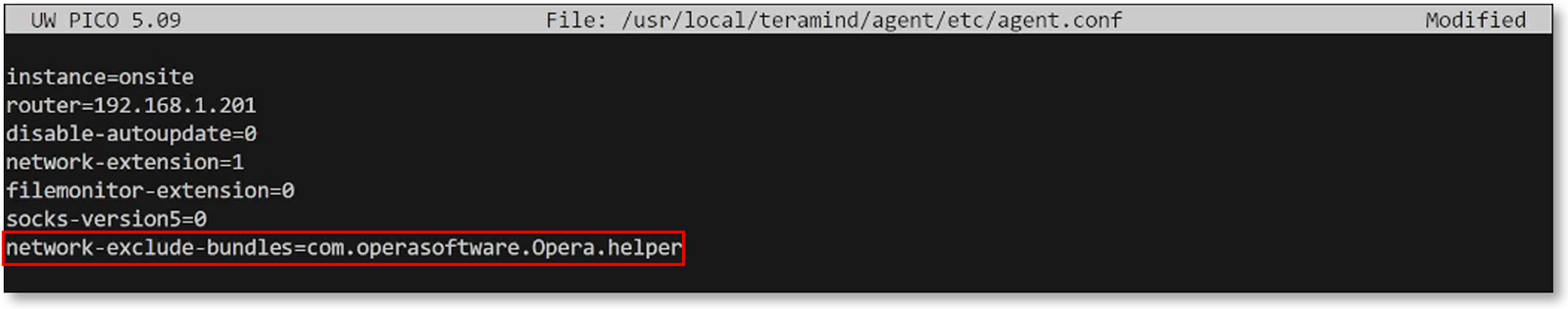
To learn more, check out the Agent Installation/Configuration Parameters (Mac) section in the Agent Installation article.
Other New Features & Improvements
There are a lot more improvements packed into this release with several general enhancements to the UI, settings, security, and performance. Below are just a few of them. Please check out the full list here.
BI Reports
Improved date filter in the Login Session report, support for Common filters in the Audit report, inclusion of the Position dimension in chart widgets, combining Global and Widget filters, and more.
Monitoring Settings
Support for conditional audio capture in remote sessions, better handling of regular expression in File Transfers monitoring, and other updates.