Check out the highlights from our most recent update, Platform Release 643. This is our biggest release so far with 433 features, improvements, and bug fixes. See the highlights below. For a full rundown, check out the complete Release Notes here.
Activity Monitoring & Business Intelligence
Find Out Where Your Employees Are with Geolocation Monitoring
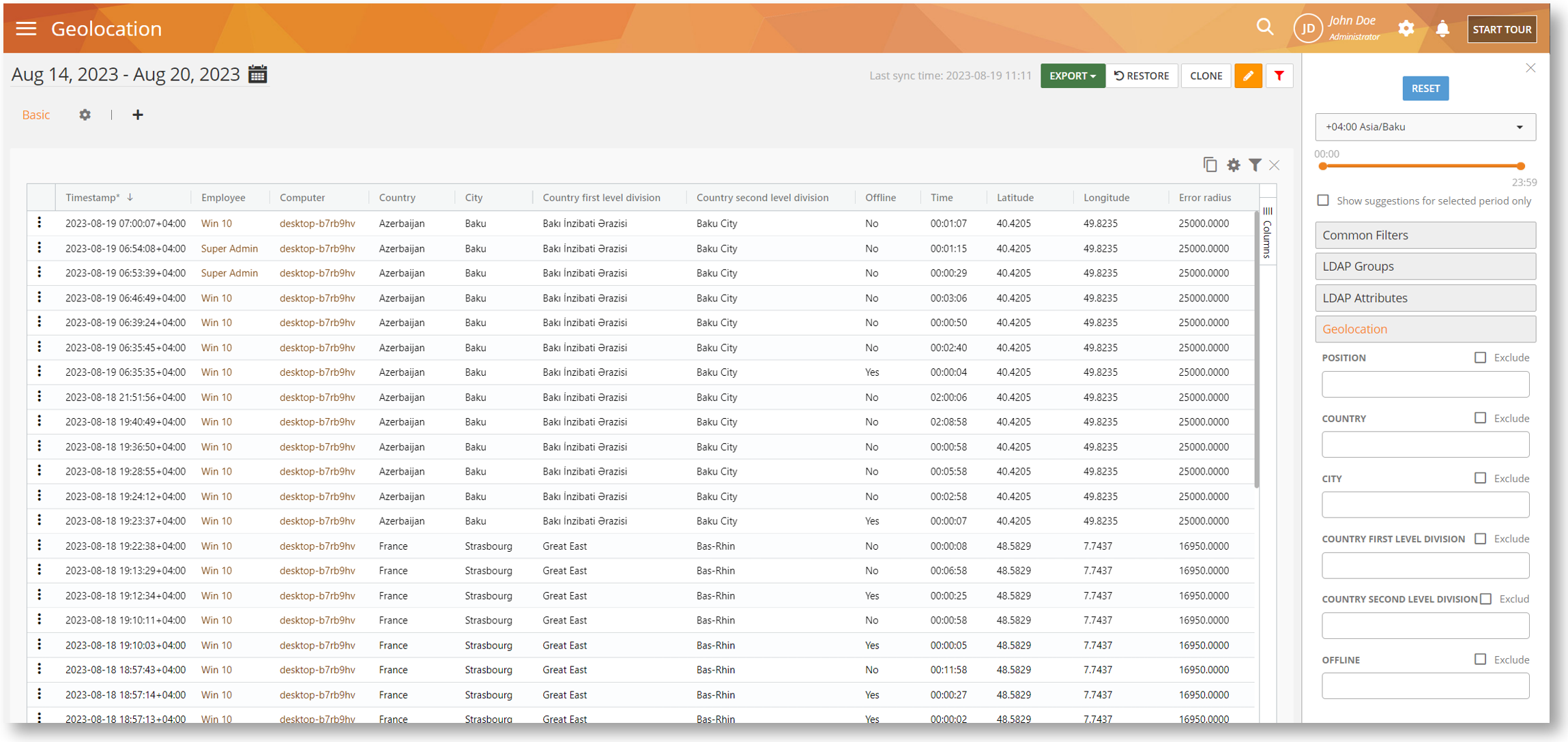
We are introducing Geolocation monitoring to help you track where your employees are working from. This might be useful if you have a remote, dispersed team or have field workers who work on different job sites. You can use the information for security, scheduling, payroll, and compliance purposes. For example, check for attendance, identify if an employee is working from home, track when a user is traveling abroad, etc.
Using the new Geolocation BI report, you will be able to track the location down to the country, city, local divisions, and the actual coordinates (latitude, longitude). The feature works even when the user is offline.
View Everything in One Place with the All Events Report
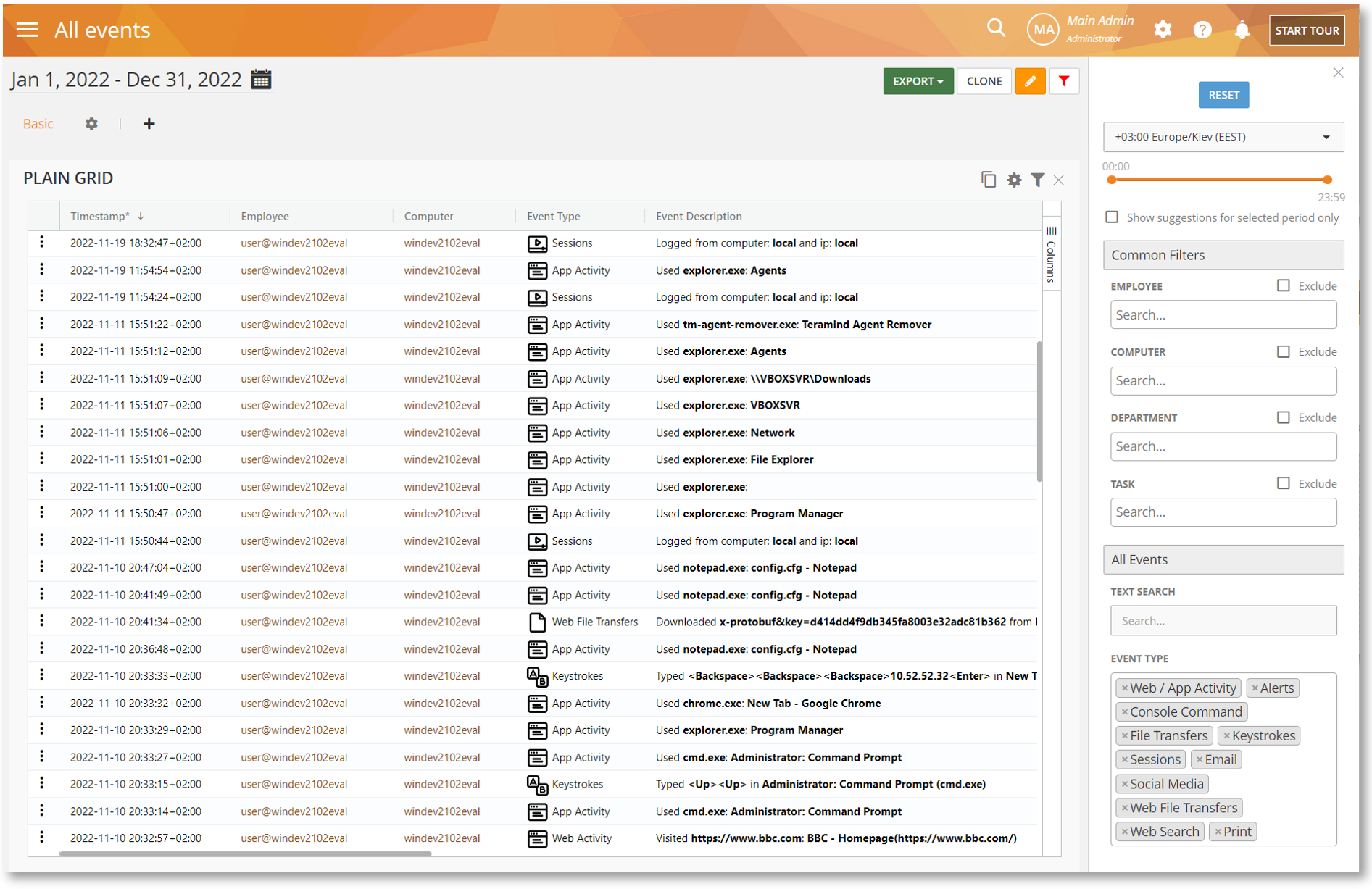
The new All Events BI report will show all the events (e.g., Web/App Activity, Alerts, File Transfers, Emails, Sessions, Print, Keystrokes, etc.) for all users and computers. This report will help you get a holistic view of the activities happening in the organization. It will also make it easy for you to conduct analysis and audits by using a single pane of view instead of having to go through different reports.
Stay Ahead of the Game, Monitor the New Outlook for Windows
If you are currently trying out the new Outlook for Windows, you are in luck! We are proactively adding support for the new Outlook desktop client that’s currently being rolled out by Microsoft as a preview version through their Insider channels.
You should be able to track incoming/outgoing emails, capture attachments, and apply behavior rules to the new Outlook for Windows.
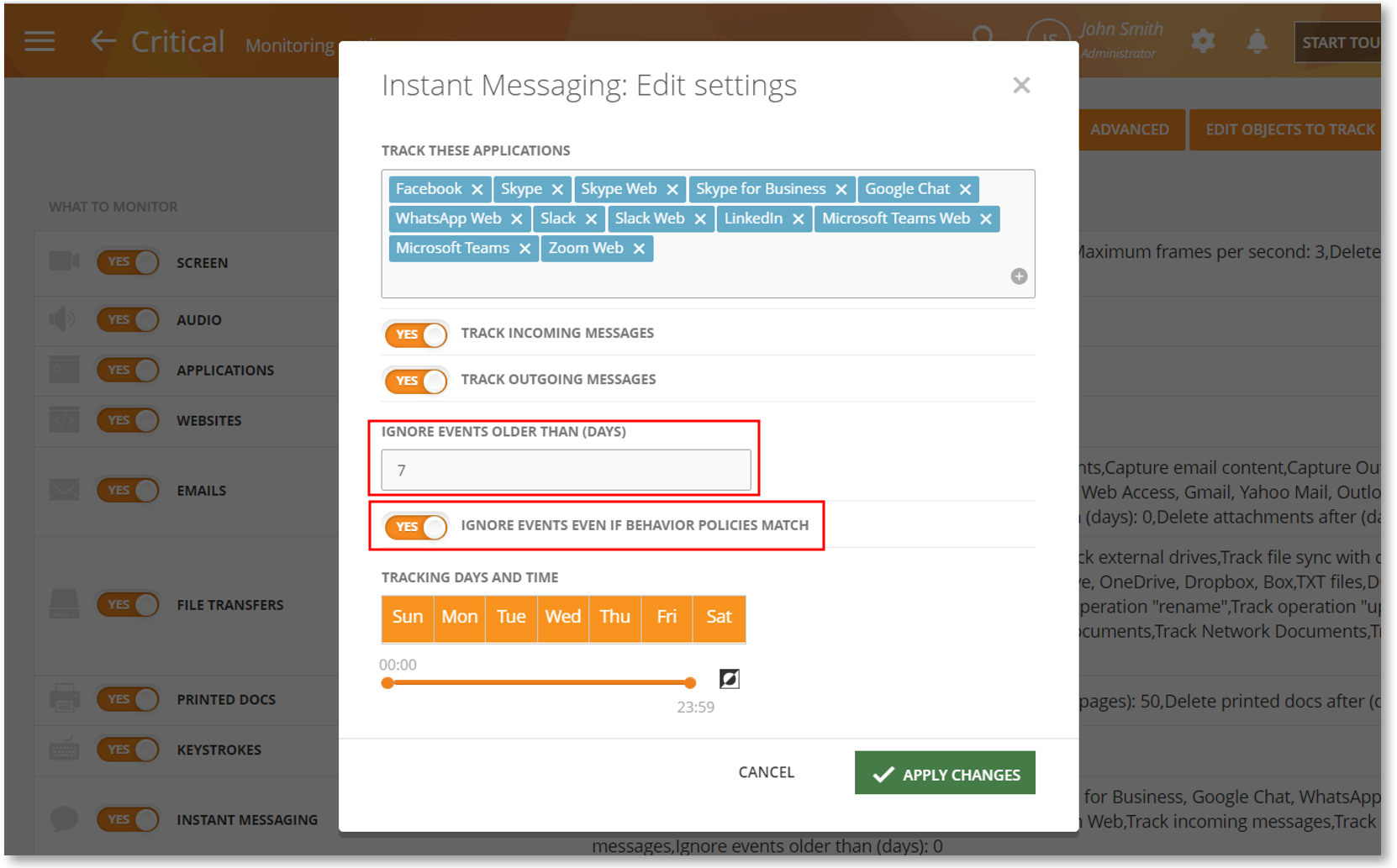
Reduce Noise and False Positives by Ignoring Old IM Activities
Sometimes, users might browse older messages on their IM client. This would unnecessarily capture irrelevant data on your IM activity reports and unexpectedly trigger behavior rules.
We have added two new Monitoring Settings for Instant Messaging which will allow you to cut off capturing IM conversations older than certain days.
Using these options, you will be able to reduce noise in your IM monitoring reports and prevent false positives.
Enterprise Security
Get the Most Security & Privacy for Your Data with End-to-End Encryption
End-to-End Encryption (E2EE) secures your data by encrypting it all the way – from its origin to its consumption. The encryption is done by multiple, strong security keys and passphrases. The data cannot be deciphered by a third-party entity or a user without the encryption keys and passphrase.
By integrating envelope encryption and end-to-end encryption alongside a TLS 1.2 or higher transport protocol, Teramind E2EE will provide you with multi-layered security for your data. This combined approach will enhance privacy, integrity, and control of sensitive information as it’s stored or accessed. This will also be a suitable option if you need to meet strict compliance requirements.
When E2EE is enabled, the Session Player, Keystrokes activities, and other supported data* will be masked. A user, even an administrator will not be able to view the data unless they have the right passphrase.
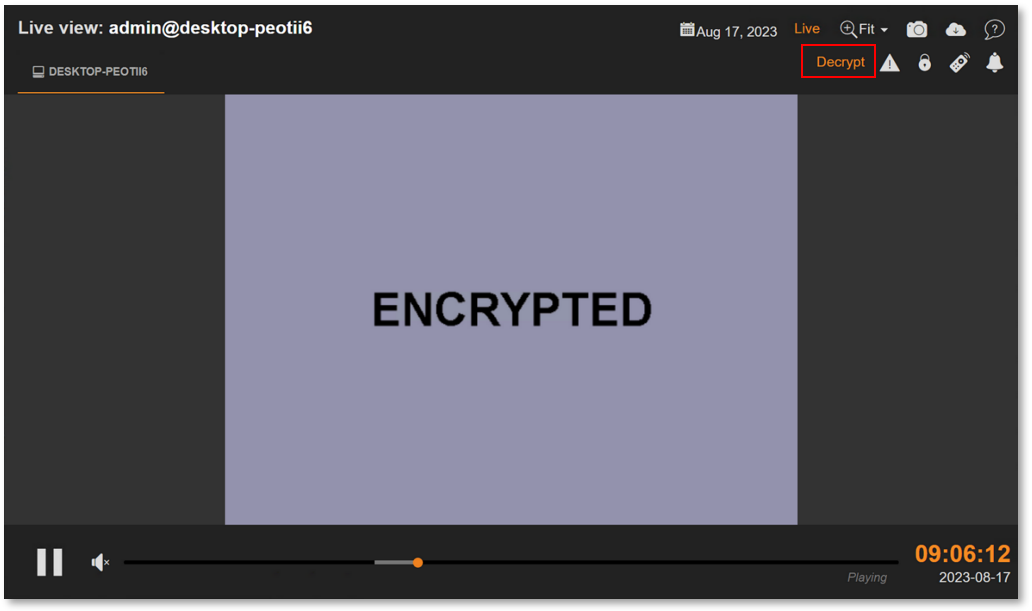
*Currently, screen recordings and keystrokes data are encrypted under E2EE.
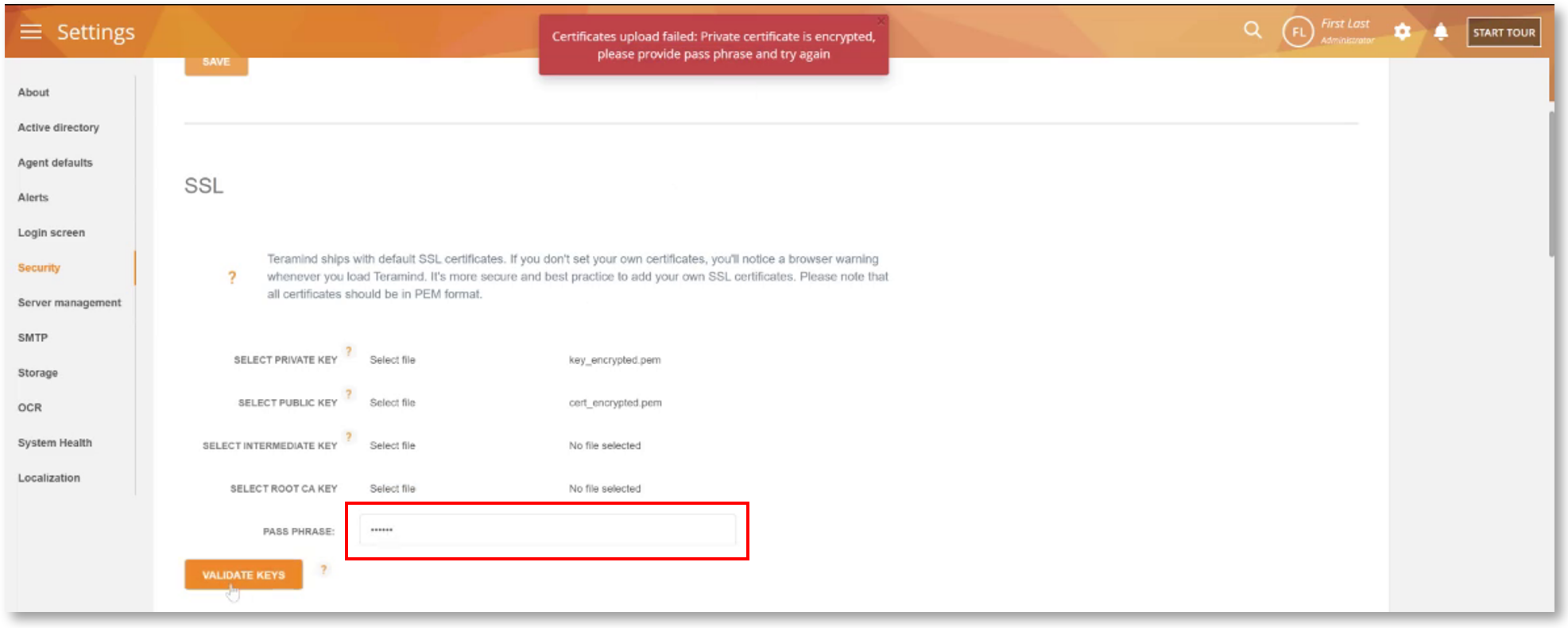
Use An Encrypted Third-Party SSL Certificate for Additional Security (On-Premise)
Previously, we only supported unencrypted SSL certificates with an On-Premise deployment.
From this version, we have added support for third-party signed, encrypted certificates. You will be able to upload such a certificate from the Settings > Security > SSL section of your Dashboard.
There are many benefits to using a private key-encrypted SSL certificate. For example, the private key’s secrecy ensures additional security through asymmetric encryption, prevents authorized users from decrypting the data, and reduces risks from brute-force and man-in-the-middle type attacks. Additionally, it improves the authenticity and trust of the data transmission.
Having Issues with LDAP Authenticate? Use Your Own Certificate (On-Premise)
We have added a few options to the Active Directory settings that will allow you to use your own CA certificate for LDAP authentication.
While it’s not recommended to use a self-signed certificate, sometimes you may need to use one. For example, if you are testing out a new deployment or running it on a low-risk internal site and you don’t want to see security alerts from browsers and operating systems. Also, Teramind will not let you use LDAP password verifications for Dashboard changes if it detects an invalid/untrusted certificate. This feature will help you mitigate such issues.
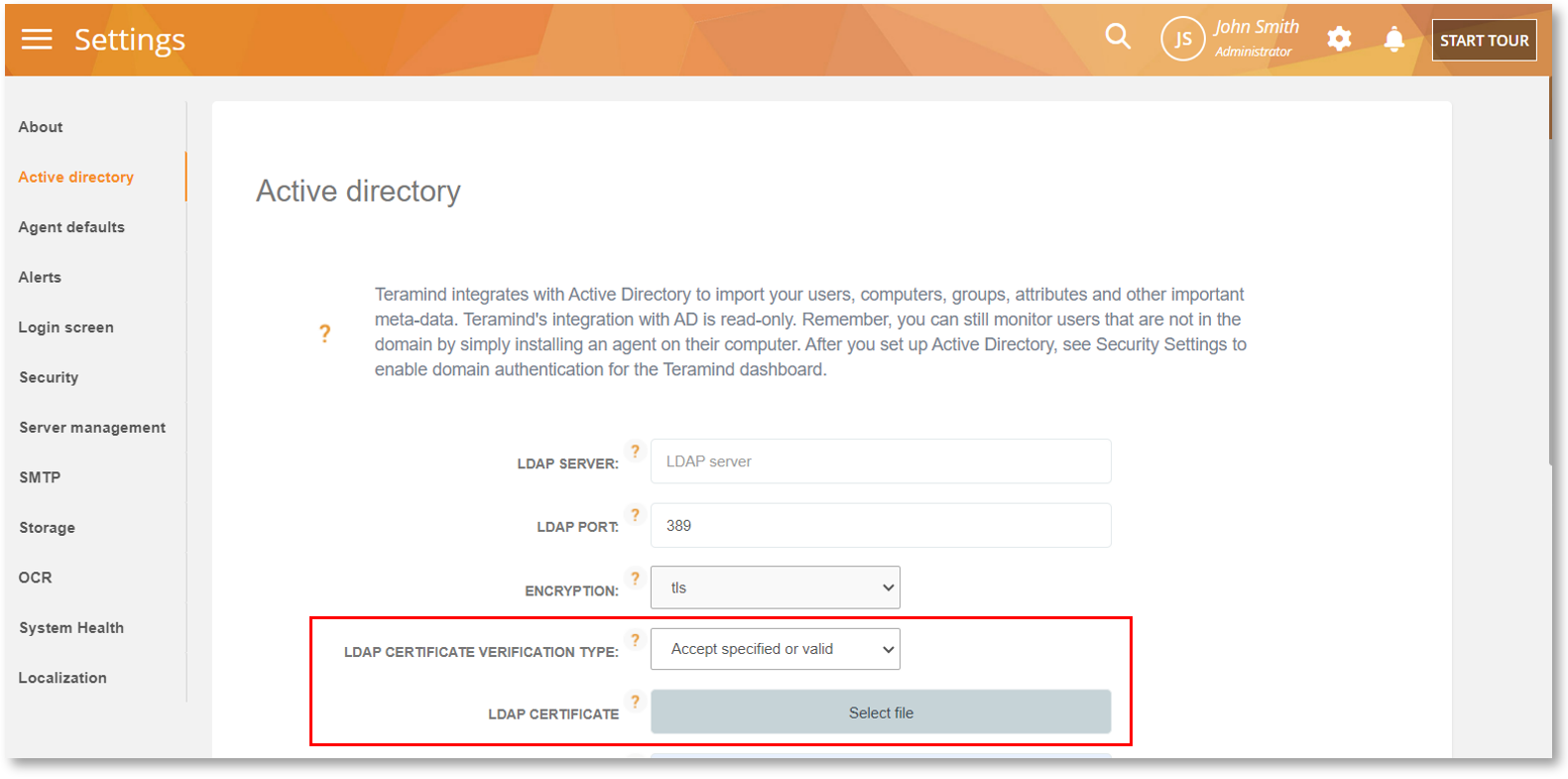
Want to Enforce the CA Authority (or Mask it)? Use Your Own Proxy Certificate
By default, Teramind injects a web proxy certificate into websites to monitor encrypted/HTTPS traffic. This certificate is signed by our root certificate Quick Web Proxy, which acts as the Certificate Authority (CA) for the domain’s certificate.
It’s now possible for you to use your own root certificate instead of Teramind’s default Quick Web Proxy certificate. This might be useful in an enterprise setting where you need to enforce your own certificate authority for security and compliance purposes.
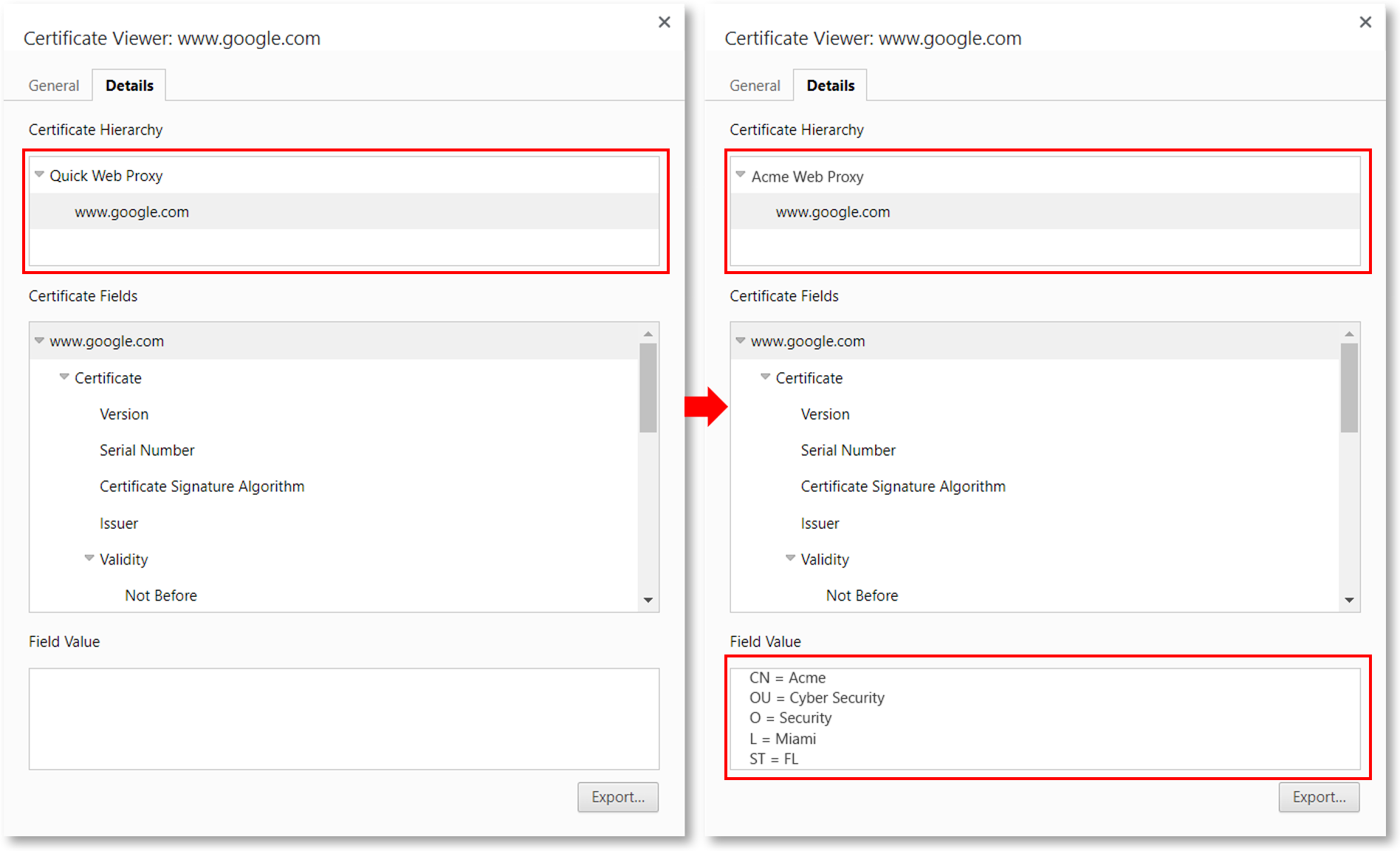
Automate Certificate Installations, Add Them Though Nginx (On-Premise)
In some situations, you might have a locally incorporated CA, and sign your certificates by it. In order for this to work, you might need to install Root CA and Sub CA certificates on each of your web servers.
To make it easier for you, we have added support to add your own SSL certificate bundle to your master node through the Nginx configuration.
Mac
Don’t Miss Out, Track Secure Web Traffic on All Popular Browsers
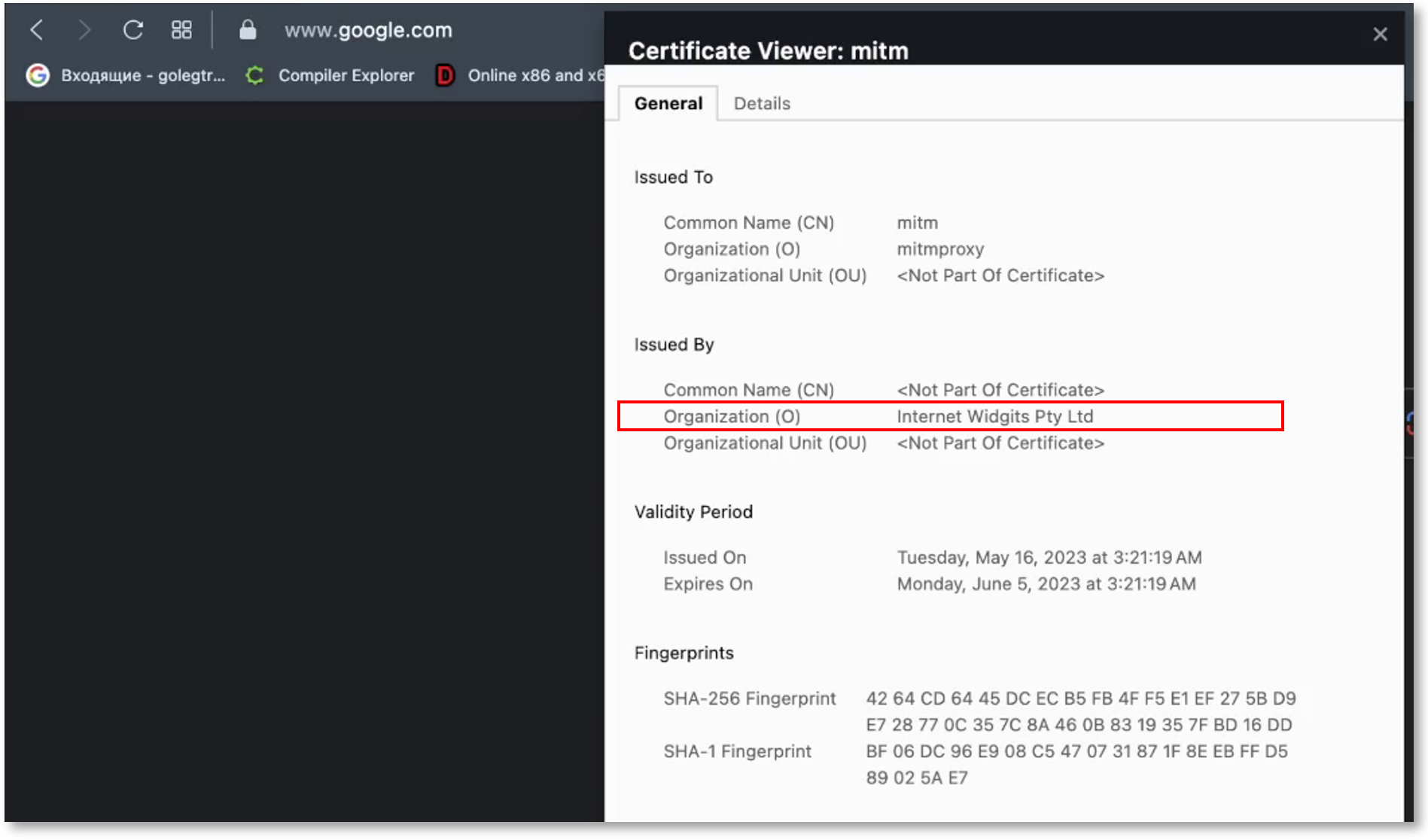
The Mac Agent is now able to decrypt HTTPS/TLS traffic. This will give you the ability to create Webpages-based behavior rules – warn users and block network connections. This capability applies to all apps and browsers that use HTTPS/TLS.
As part of the feature, a proxy certificate will be injected into the websites to monitor HTTPS/TLS traffic.
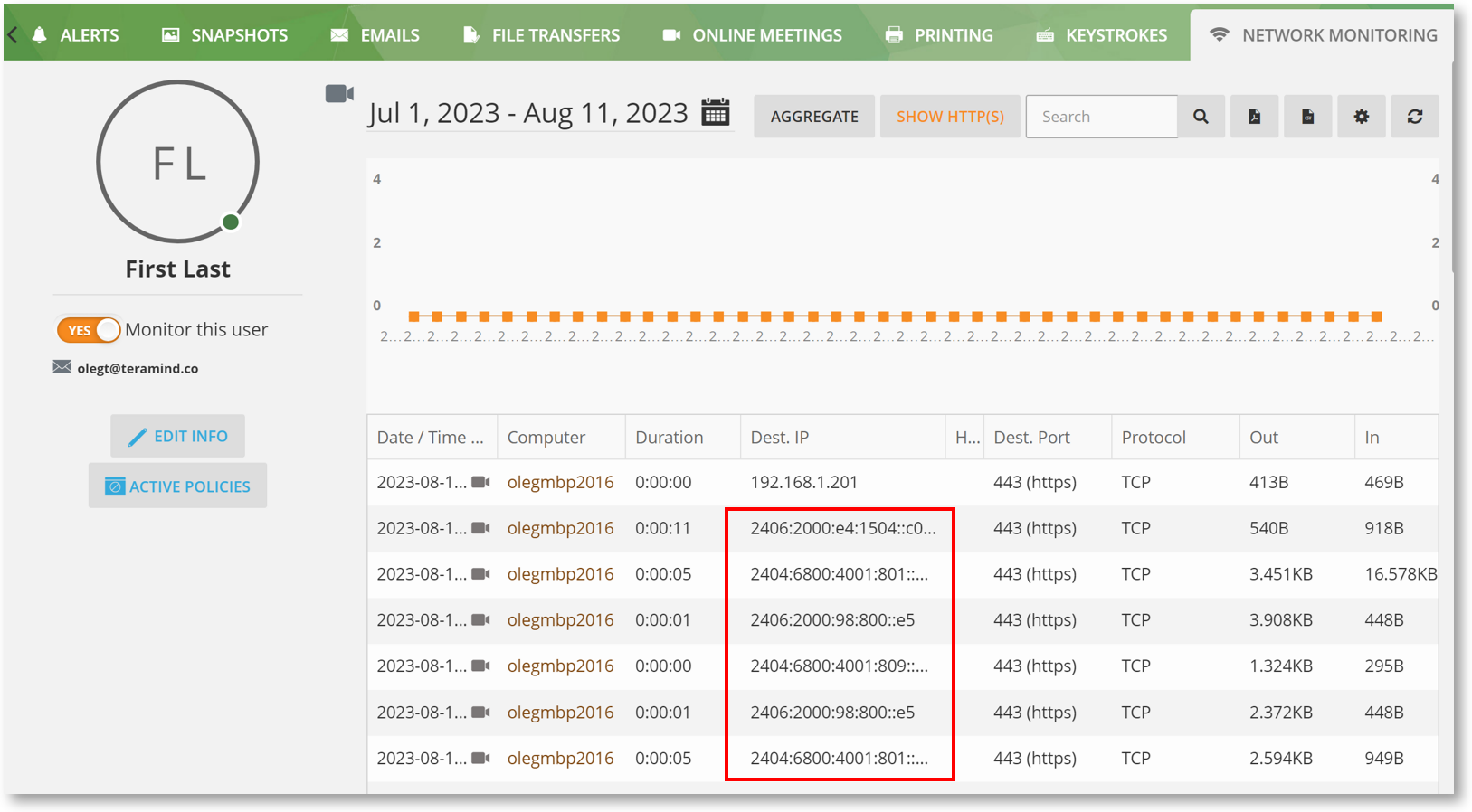
Monitor the Modern Web by Intercepting IPv6 Connections
Before this release, the Mac Agent only supported network monitoring for IPv4 addresses. As a result, you might have noticed missing activities on the Network Monitoring or Applications & Webpages reports. For the same reason, some of the Webpages or Networking-based Behavior Rules wouldn’t work either.
From this version, we are adding support for filtering network activities over IPv6. This will allow you to track network activities, web browsing, etc. on sites that use IPv6 and apply behavior rules.
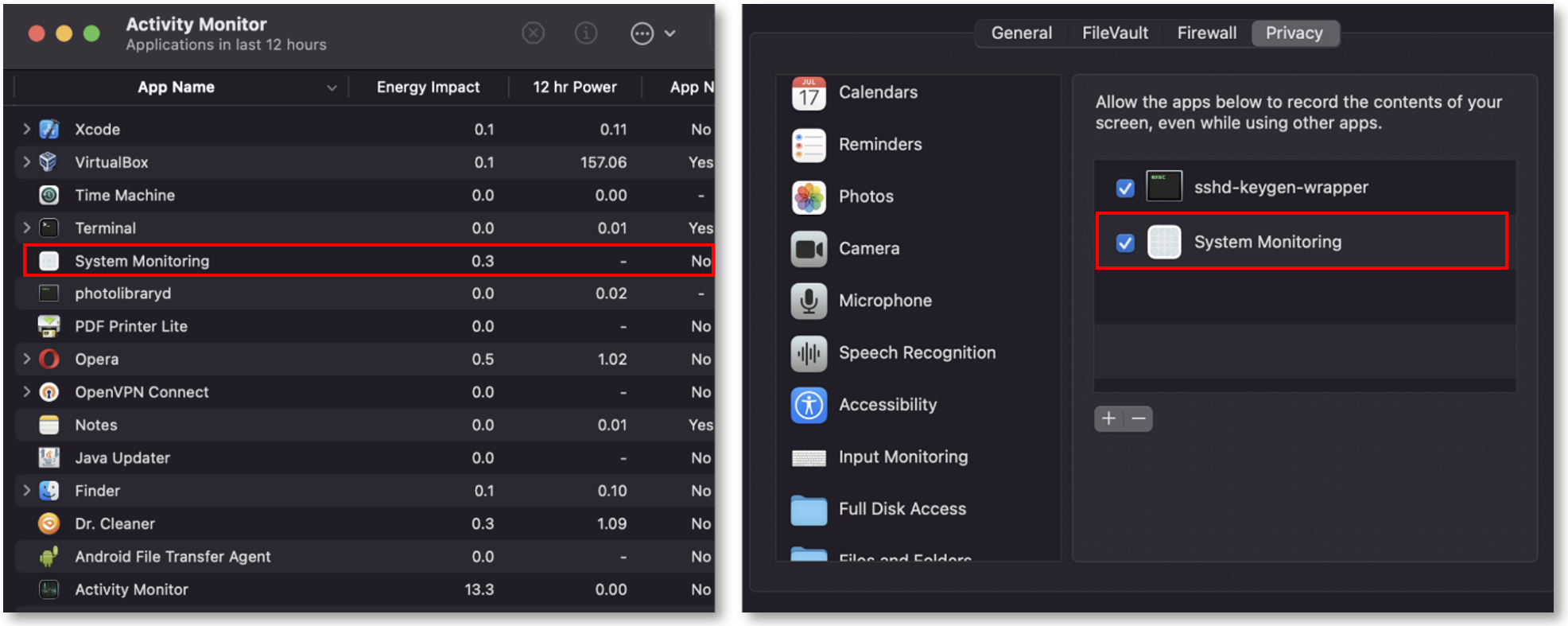
Obfuscate the Agent by Changing Its Process Name
We are providing customers with the option to change the process name of the Hidden/Silent Agent.
The ability to change the process name will allow you to obfuscate the Agent so that it will not be obvious to a regular user that the Agent is running.
Other New Features & Improvements
There are a lot more improvements packed into this release with several general enhancements to the UI, security, and performance. Below are just a few of them. Check out the full list of improvements here.
Prevent Bypass of URL Logging
We are introducing a better method to detect browsers to prevent bypass of URL logging. The Agent is also now able to detect custom browsers that were modified.
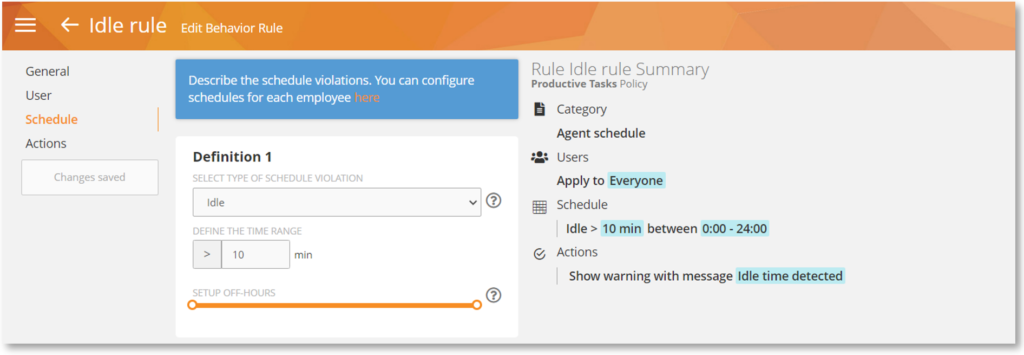
Limit Alerts Generated by Idle Rules
We made changes to the Idle rule’s alert behavior so that it will generate a single alert – when the rule is violated. This will prevent unnecessary triggering of the rule.
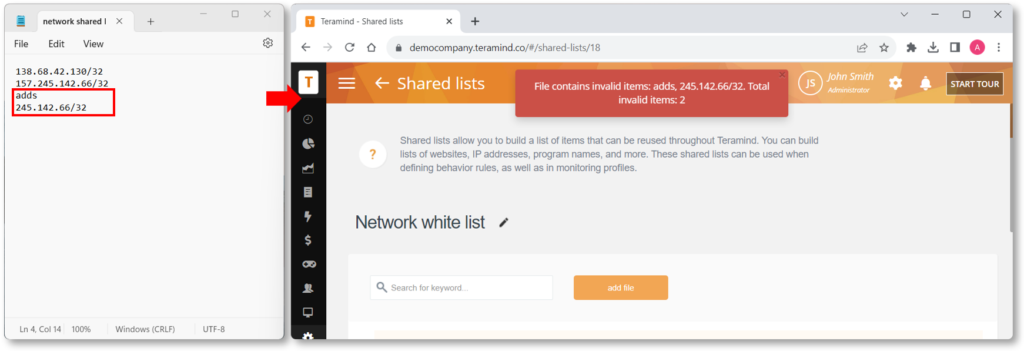
Better Handling of Uploaded Files
We improved how file uploads are handled when importing employees, shared lists, etc. For example, now, the Dashboard will show an error if it encounters any invalid lines in a shared list and list which items caused the error.