Check out the highlights from our most recent update, Platform Release 620, boasting ten new features and dozens of enhancements and improvements that increase security and reliability. See the highlights below and for a full rundown, check out the complete Release Notes here.
Reporting & Analytics Enhancements
Changes we made to the Dashboard, BI Reports, and Employees Report offer greater controls and data visualization features to get the information you need quicker.
Filter Out the Data You Don’t Need on BI Reports
Platform Availability: Cloud, On-Premise
Where to Find it On the Dashboard: BI Reports> Filter panel
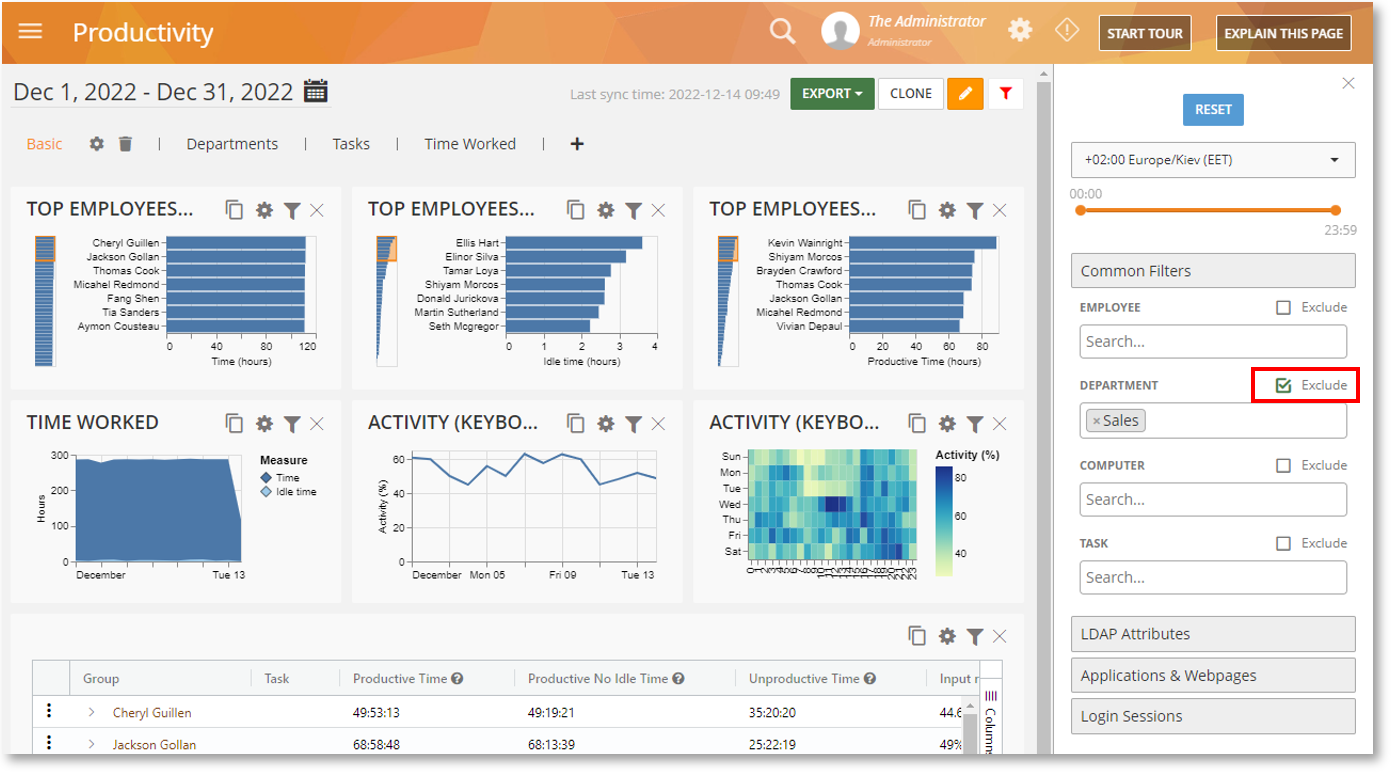
The Filter panel on the BI Reports allows you to select specific users, departments, LDAP attributes, and other data points to be included in the report. But until now, there was no way to exclude unnecessary items.
The Exclude option now makes it possible to eliminate unnecessary data from the report. For example, you can create a report that includes all employees in the organization while excluding certain departments with the DEPARTMENT filter:
Quickly View and Edit Active Policies & Rules for an Employee
Platform Availability: Cloud, On-Premise
Where to Find it On the Dashboard: Employees > Employee’s screen
We’ve made it easier for you to find out which policies or rules apply to an employee.
The new ACTIVE POLICIES button added to the Employees > Employee’s screen lets you quickly access the policies and rules applied to the user:
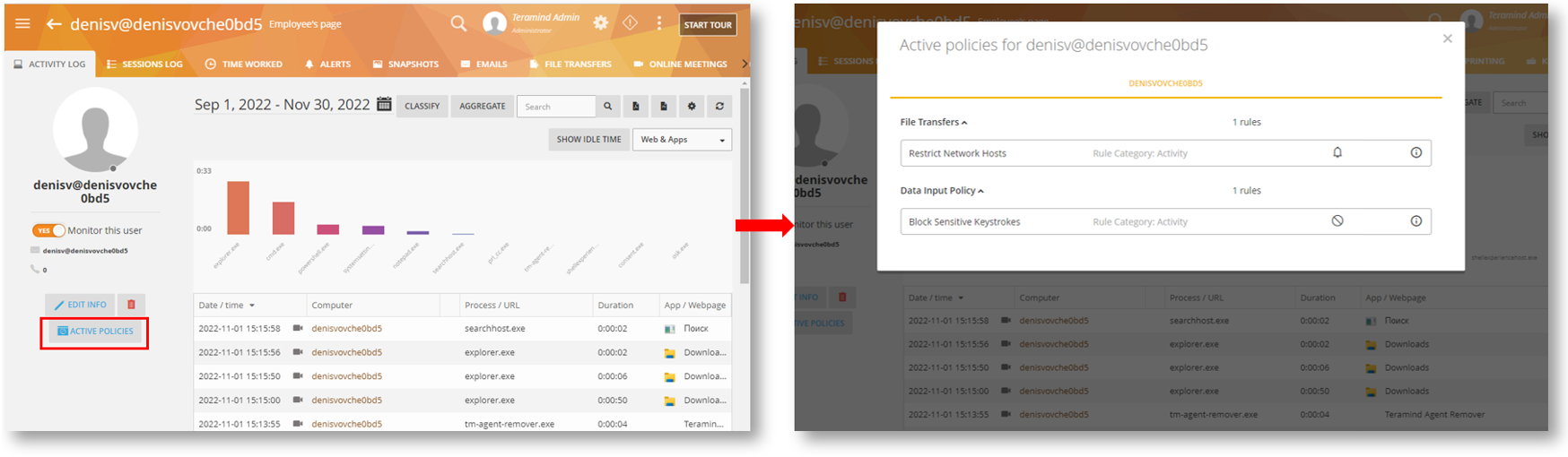
To make things even easier, the pop-up window will also allow you to edit a policy or rule without navigating away from the employee page.
Stronger Endpoint Protection
Changes we made to Behavior Rules strengthen your insider threat management and data loss prevention strategies. And now, Activity-based behavior policies and rules are supported on Mac! Note, Mac Agent 0.1.231 or above is needed.
Improve Your System Security by Detecting when UAC is Invoked
Platform Availability: Cloud, On-Premise
Where to Find it On the Dashboard: Behavior > Policies > Rules Editor
A new rule criterion, Running elevated is added under Activity Rules > Applications. This will allow you to detect any application that’s launched with elevated permission using Windows User Control (UAC):
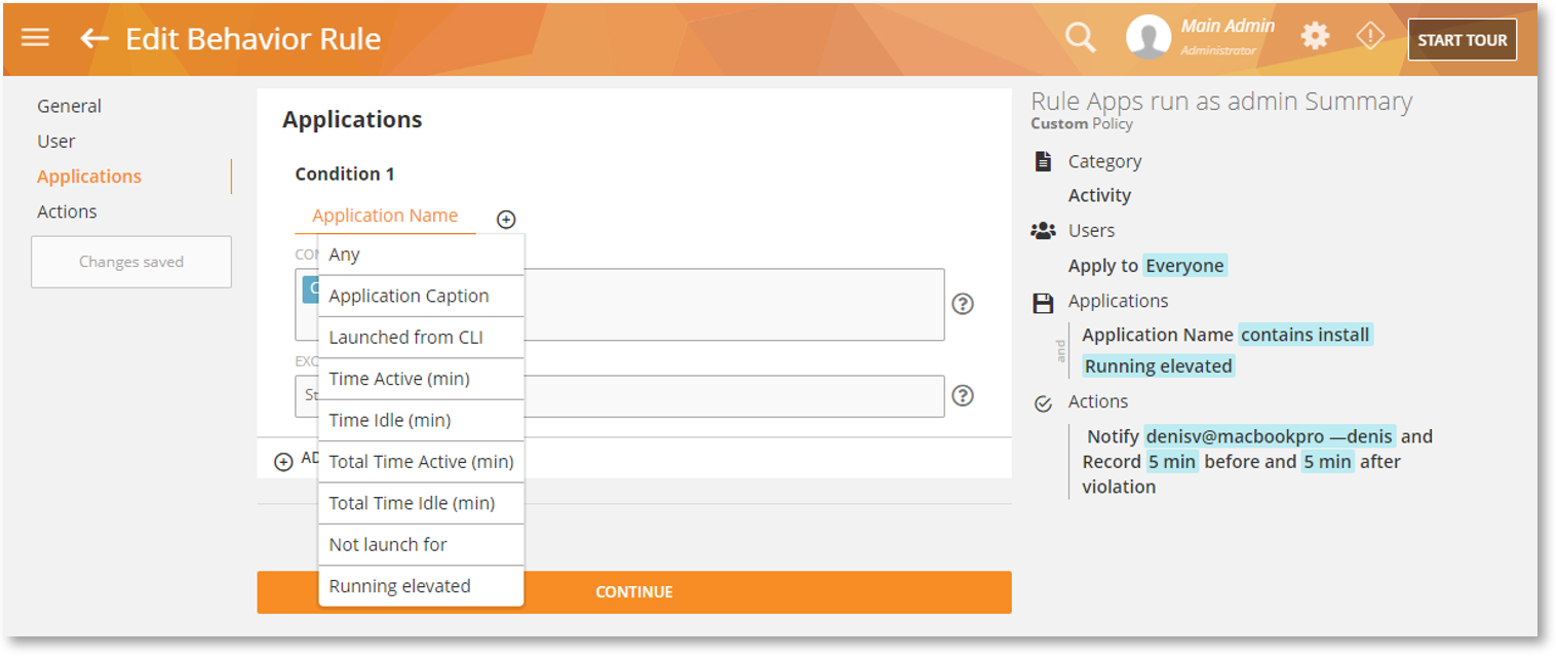
An app is usually run as elevated when you launch it from the Windows Start menu while holding down the SHIFT+CTRL keys. Or, when you run it from Windows Explorer with the right-click and then select the “Run as Administrator” option. This new rule feature enhances the security of your system as software that usually requires admin permission might make changes to your system. Among other advantages, It also helps mitigate the impact of malware and prevent unauthorized privilege escalation.
Mac: Stop Unwanted Apps with Applications Rules
Platform Availability: Mac / Cloud, On-Premise
Where to Find it On the Dashboard: Behavior > Policies > Rules Editor
The Applications Activity-based rules helps detect the running of unauthorized apps, and optionally warn the user or block the app. These rule violation events are also viewable via BI Reports > Behavior Alerts.
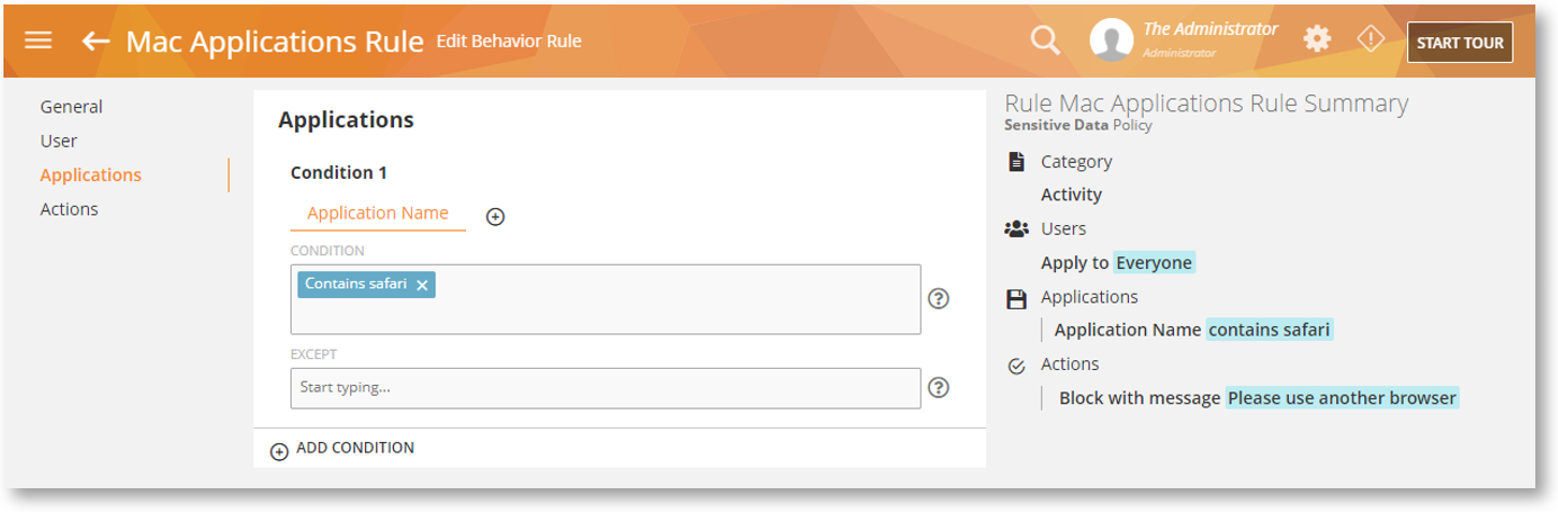
Mac: Track & Control User Inputs with Keystrokes Rules
Platform Availability: Mac / Cloud, On-Premise
Where to Find it On the Dashboard: Behavior > Policies > Rules Editor
The Keystrokes Activity-based rules help detect what text or words are typed by users, and optionally warn or block them when sensitive, inappropriate or unauthorized text and keyboard shortcuts (such as screen capture) are detected. Like any other rule violation, you’ll be able to view these violations on BI Reports > Behavior Alerts.
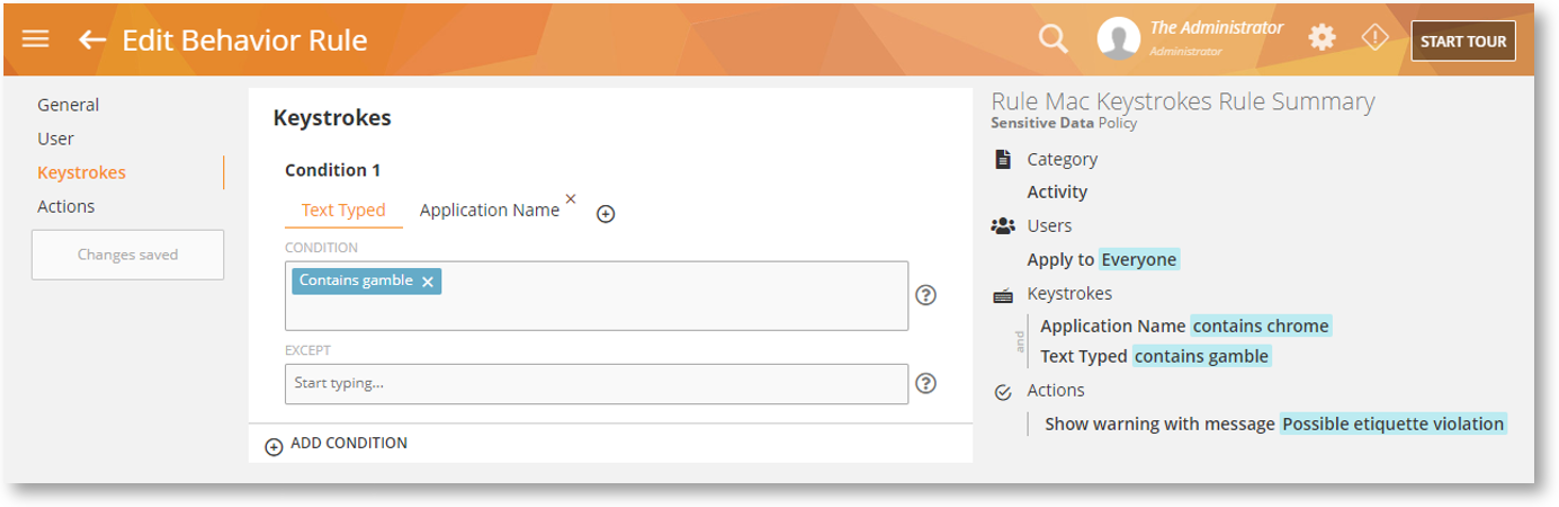
Mac: Prevent Data Exfiltration, Reduce Waste with Printing Rules
Platform Availability: Mac / Cloud, On-Premise
Where to Find it On the Dashboard: Behavior > Policies > Rules Editor
Printing Activity-based rules detect what’s being printed on a local or network printer, helping limit print orders and reduce paper waste. You can also enable/disable output to certain printers, prevent the printing of specific documents, automatically save a copy of the document being printed, and more. You can warn or block a printing job and view the rule violation events on BI Reports > Printing.
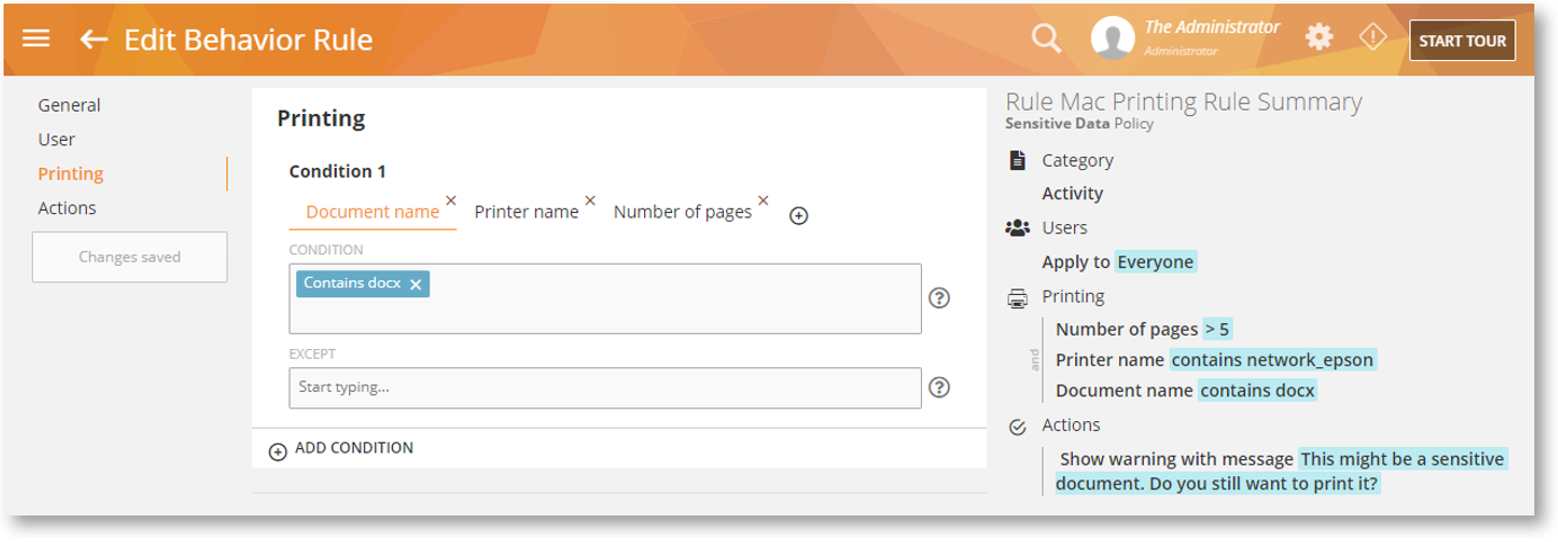
Other Mac Features and Enhancements
This release came with several other features, enhancements, and bug fixes just for our Mac users, including:
- The ability to configure auto-update from your desktop
- Cached behavior policies and rules to speed up processing and offline enforcement
- Bug and performance issue fixes on M1 Mac
Better Enterprise Integrations with API Enhancements
We’ve introduced several new API calls, tracked down and fixed some hiccups, and otherwise improved the API experience for enterprise users and IT developers. For example:
- A new GET request agent/me API call to return information about the logged user and the features they are allowed
- A new GET request to get application settings such as Instance Name and Instance Type
Other New Features & Improvements
This release also came with feature enhancements and bug fixes to create easier and more streamlined platform use and navigation. See the highlights below and check out the full list here.
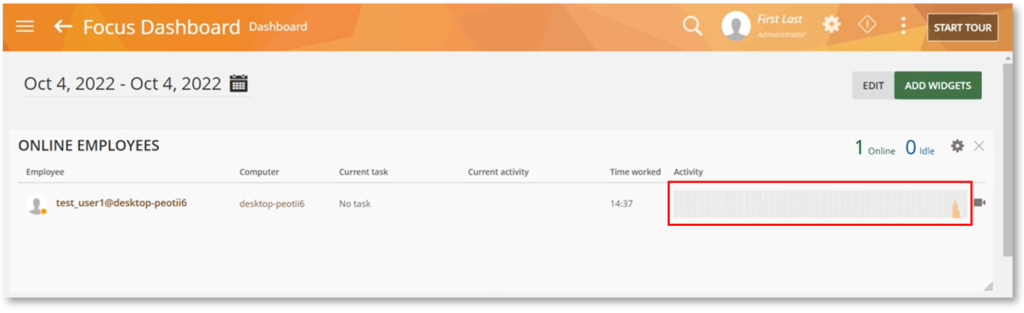
Better Graphs on Online Employees Widget
The Online Employees widget on the Dashboard now has a better graph making it easier for you to visualize the Activity score of each employee.