Teramind’s latest update, Platform Release 617, delivers six new features and five platform enhancements to deliver stronger data protection and improved reporting capabilities. Check out highlights below. For a full rundown of what was included, check out the complete Release Notes here.
Stronger Endpoint Protections
Changes we made to Monitoring Settings, Employees Report, and System Log strengthen your insider threat management and data loss prevention strategies.
Enhance Security of Remote Sessions with Advanced RDP & Clipboard Restrictions
Platform Availability: Cloud, On-Premise
Where to Find it On the Dashboard: Monitoring Settings > (select a profile) > Advanced
Remote Desktop Protocol (RDP) is a network-level service that allows users to remotely connect to another machine. With RDP, a user can log in to a remote computer (called a Host) and work on it from their local machine (called a Client). Usually, companies use it to allow employees, contractors, and external consultants access company systems remotely. The company can then apply security policies to the Host machine, protecting critical resources. However, the company cannot control what the user does on their local machine once they have access. For example, a user can copy sensitive company files to their personal machine or take screenshots on the remote terminal and save it on their local machine
Teramind already had Behavior Policies & Rules you could use to control the RDP access. Now, we have added even more features for you to control RDP sessions at the core monitoring level.
Under the Monitoring Settings > (profile) > Advanced screen, you will see some additional options to control RDP and clipboard sharing:
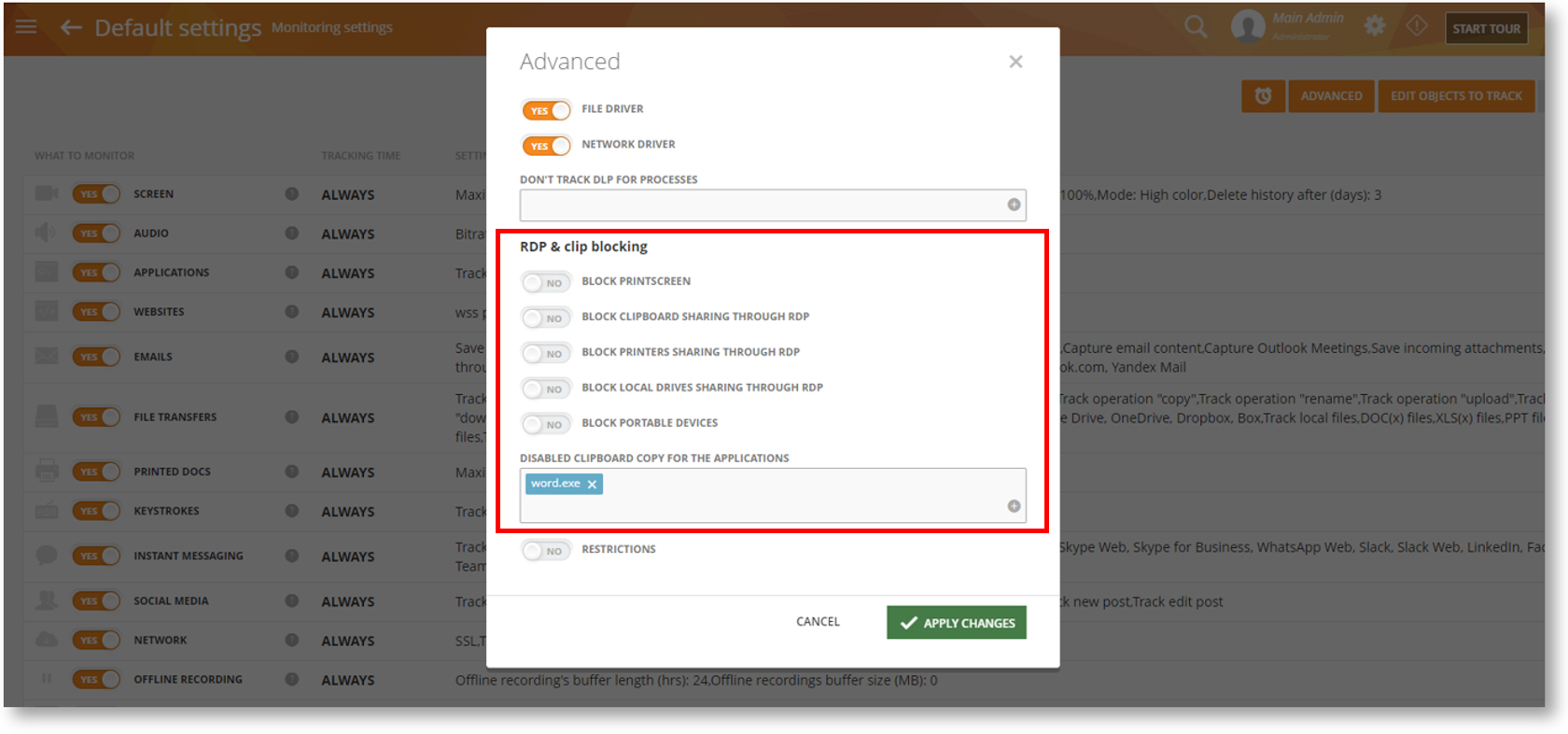
These options will let you enable/disable activities such as the sharing of printers over RDP, use of portable (USB) devices, taking screen snapshots and more. You can also disable clipboard copy/paste operations for select apps.
Track Employee Login Behavior Better
Platform Availability: Cloud, On-Premise
Where to Find it On the Dashboard: Employees
We’ve added two new columns on the Employees (List of employees) report: First online time and First online from:
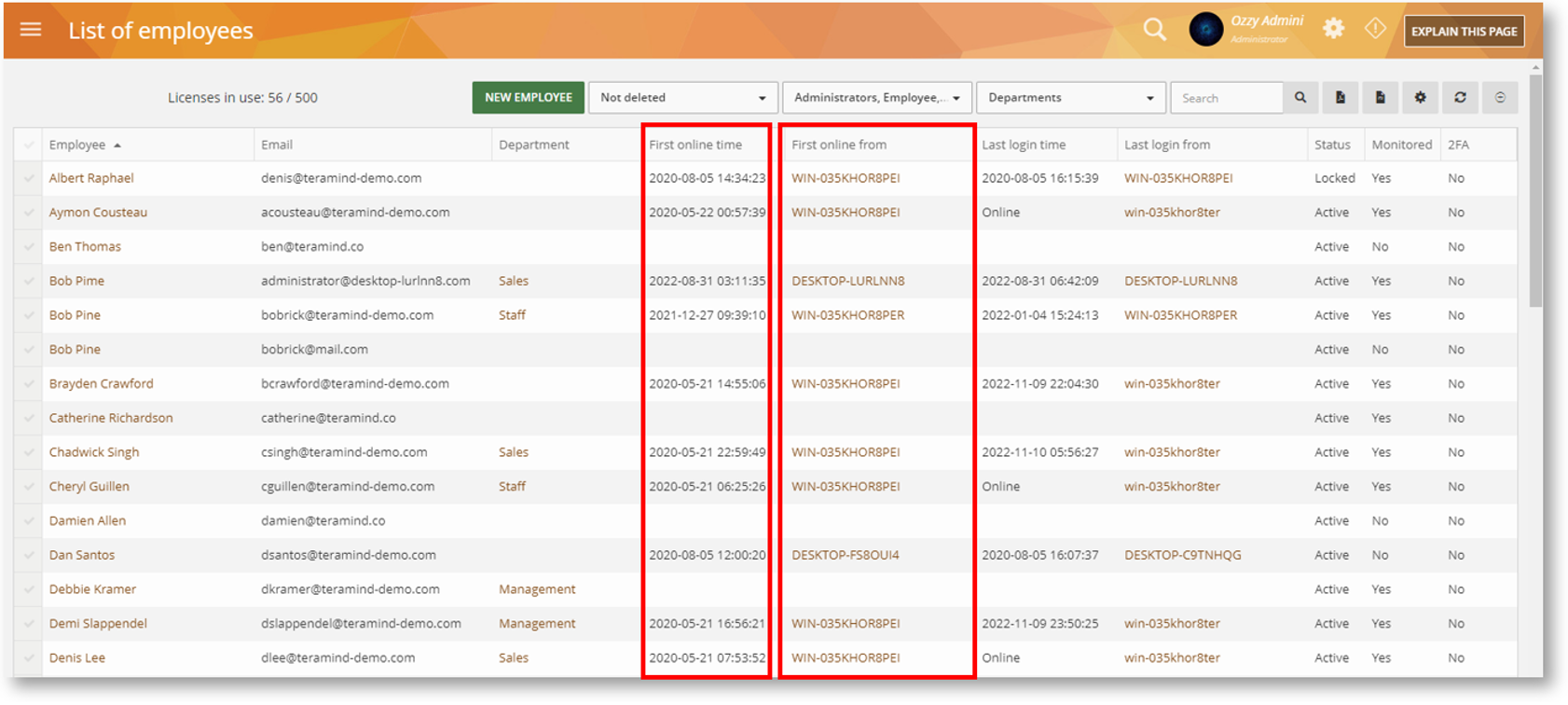
These columns, together with the Last login time and Last login from columns help you track employee sessions, especially when your employees work remotely from multiple locations or computers.
Better Audit Trails with the New System Log Objects
Platform Availability: Cloud, On-Premise
Where to Find it On the Dashboard: System > System Log
The System Log will now capture events from the Session Player (Video Player) such as when a privileged user views the live screen of another user’s desktop, starts/finishes a remote control session, freezes/unfreezes user input and more:
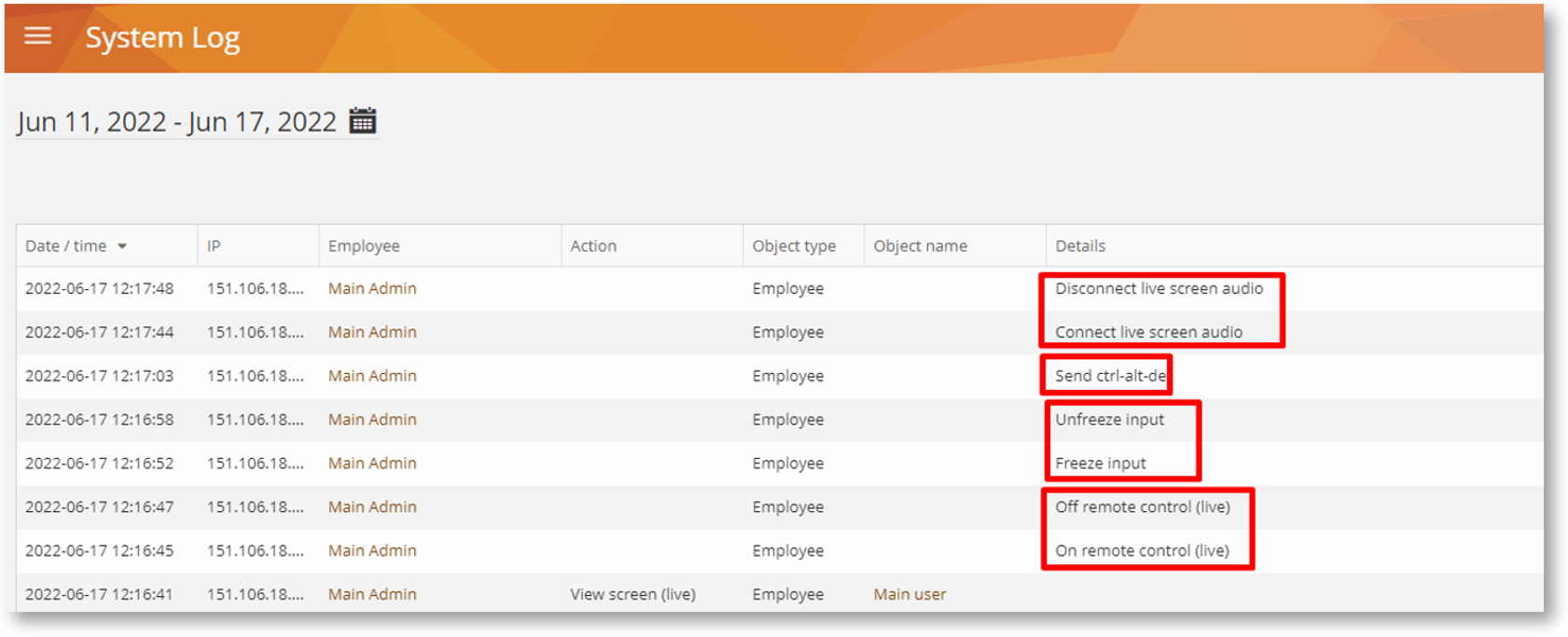
This type of additional logging details will allow you to verify if your privileged users are misusing their access rights or using them for personal objectives (like spying on a co-worker, for example). A great addition to your “zero trust” security toolbox, this feature helps establish a strong privilege user management policy and maintains detailed audit trails for compliance.
Extend Enterprise Security & IT Service Intelligence
Many of our enterprise customers use Teramind with SIEM, log analytics, or threat prevention systems to enhance their intelligence capabilities and better data resolution. The recent updates to our Integrations and API make it easier to connect these third-party systems.
Support for Splunk CIM Integration
Platform Availability: Cloud, On-Premise
Where to Find it On the Dashboard: Settings > Integrations
You can now set up a Splunk integration using the CIM (Common Information Model) on Teramind:

The CIM helps standardize data collection using the same field names and event tags for equivalent events from different sources or vendors. Relying heavily on CIM-compliant data for searches, reports and dashboards, Splunk Enterprise Security™ (Splunk ES) and Splunk IT Service Intelligence™ support this feature as a premium add-on.
With Splunk CIM now supported by Teramind, you can better utilize the events, logs, and user activity details on Splunk for enterprise observability, unified security orchestration, and threat analysis.
The Splunk CIM integration process is similar to our standard Splunk integration but uses the CIM: JSON schema, giving you more options to smoothly integrate with this popular SIEM solution.
Other New Features & Improvements
This release also came with feature enhancements and bug fixes to create easier and more streamlined platform use and navigation. See the highlights below and check out the full list here.
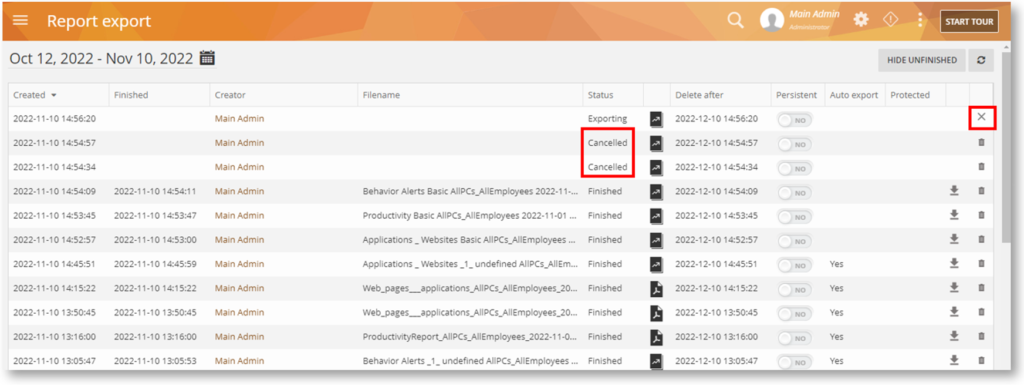
Cancel a Report Export Operation
Video or report exports can now be canceled after being started if you no longer need it.
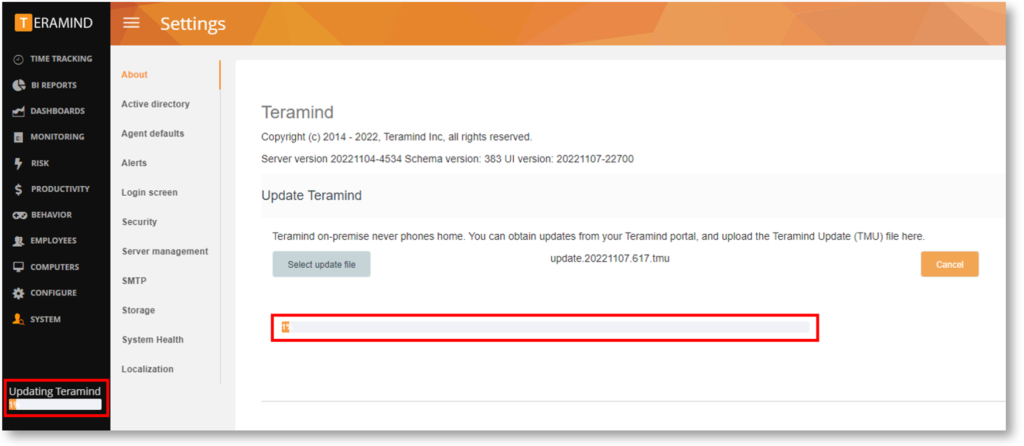
Work During Server Updates
The server update now continues to work in the background and shows a continuous progress bar even if you switch pages.
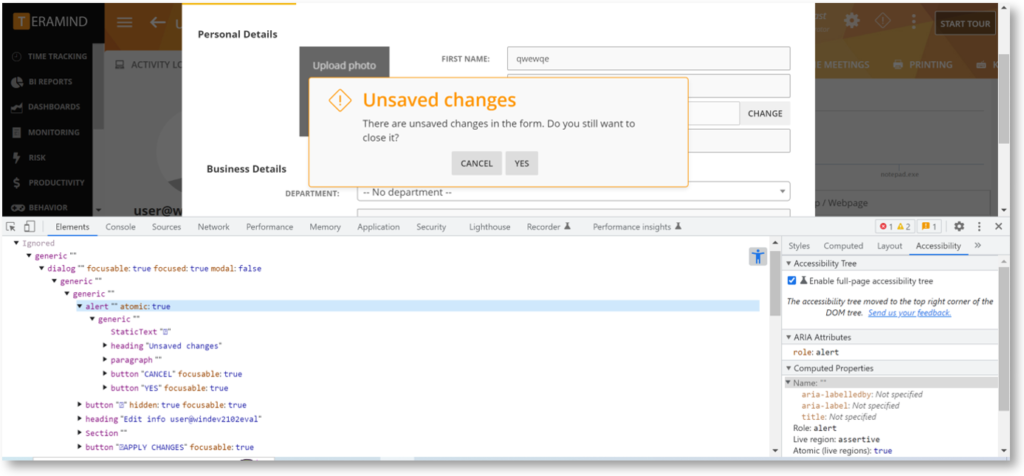
Improved Accessibility Experience
UI alert messages are now announced as a ”live region” as per the APG/WPI guideline improving the web experiences for users of assistive technologies.
Discover what Teramind can do for you!



