Platform Release 716 contains 308 new features, improvements, and bug fixes from Windows Agent 24.45, Mac Agent 24.45, Web 24.47.1, Server 24.45, and BI 24.42 as well as other components since the last release.
See the highlights below. For a full rundown, check out the complete Release Notes.
User Activity Monitoring
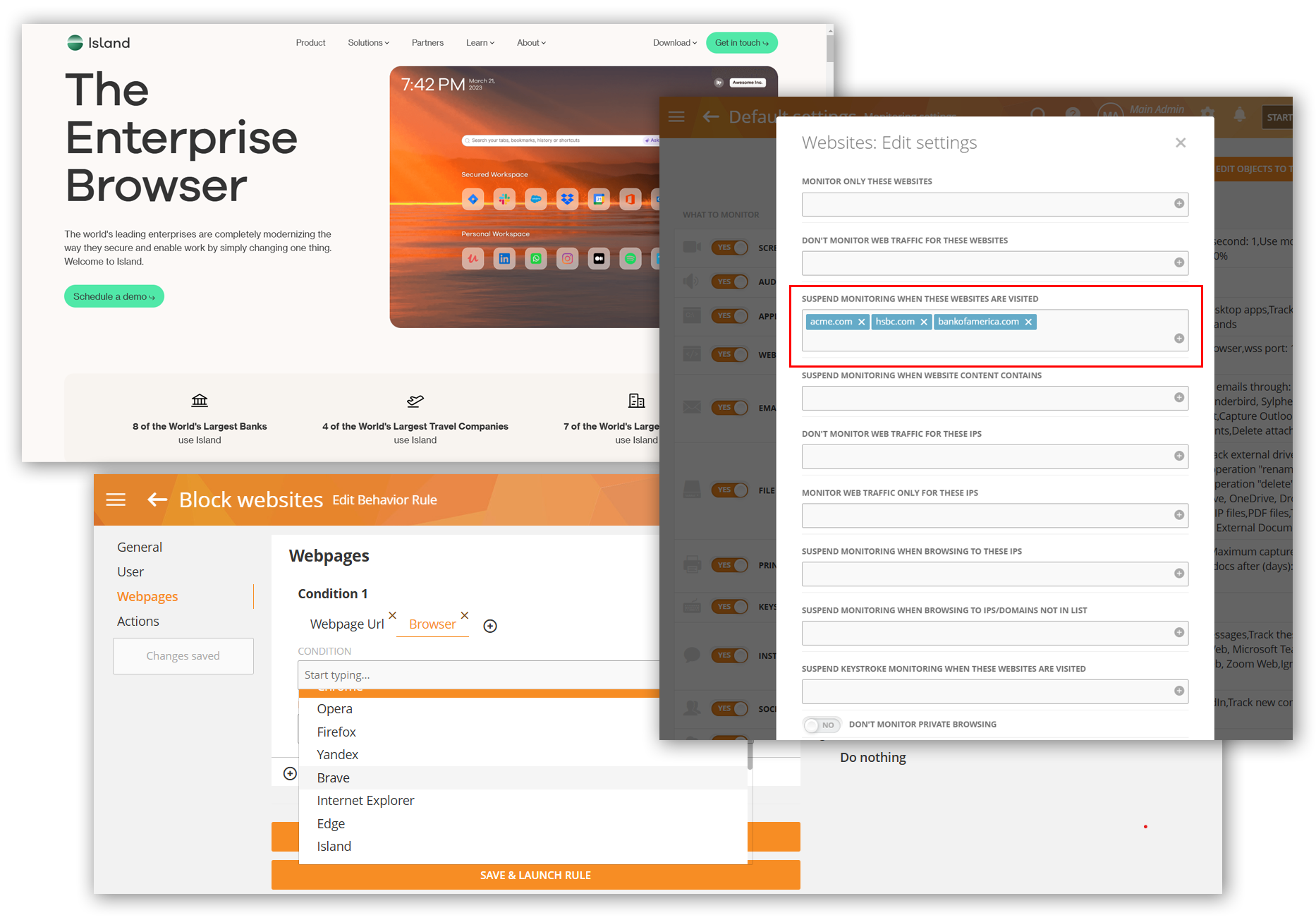
Support for Island Browser
Webpages, instant messages (chats), and online meetings on the Island browser are now being tracked. Customers using the Island browser can also apply Webpages rules and use the SUSPEND MONITORING WHEN THESE WEBSITES ARE VISITED option to limit the tracking.
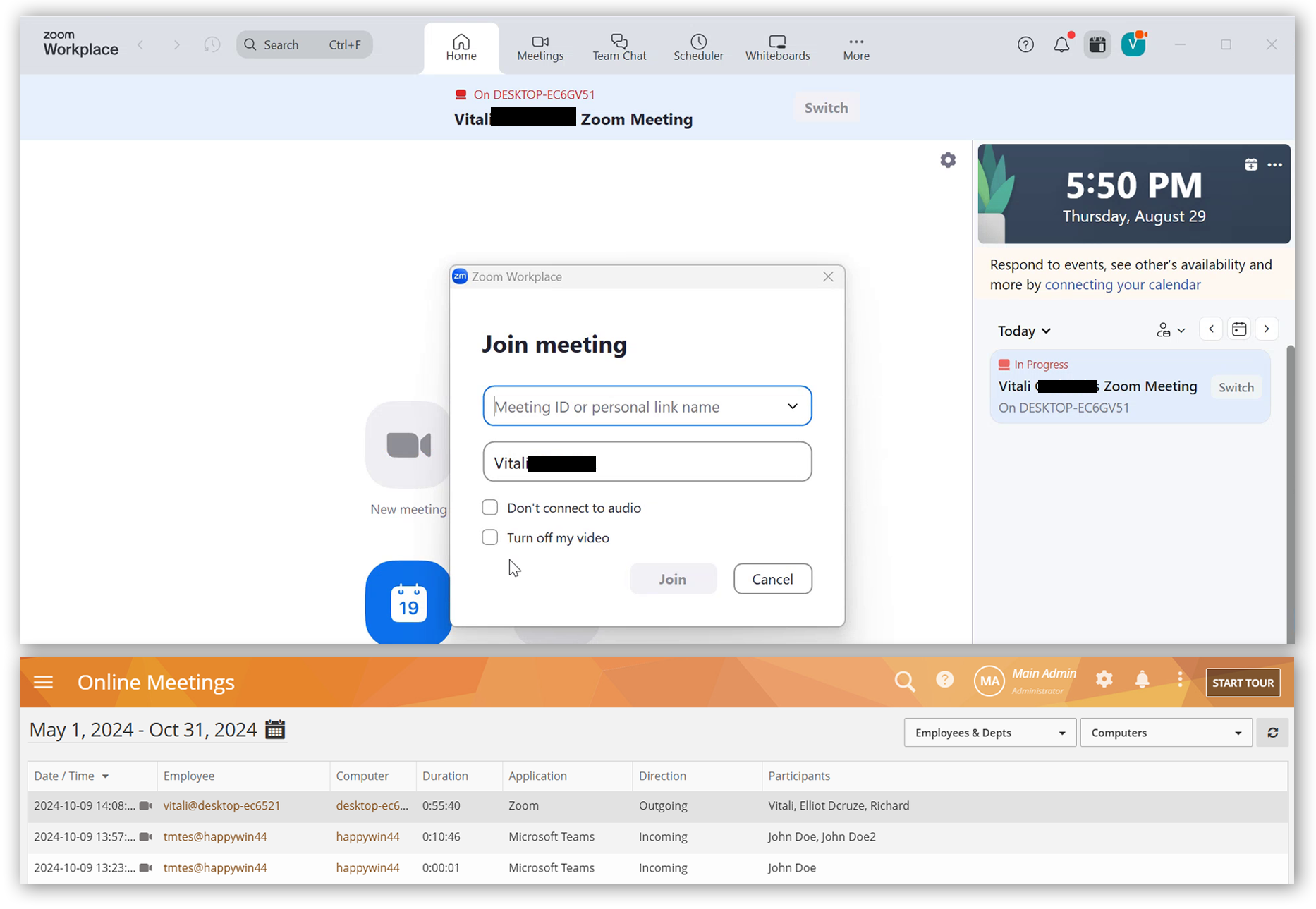
Support for Zoom Workspace
Online meetings on the Zoom Workspace app will now be tracked.
Support for uniFLOW Printers
Printed documents can now be tracked over uniFLOW printers.
Behavior Policy & Rule
New OS Version Criterion in Applications Rules
The new OS Version criterion of the Applications rule can be used to detect the OS version installed on the user’s computer. For example: ‘Windows 10’, ‘Windows 11’, etc. The OS version matching the trigger will be shown in the alert’s description.
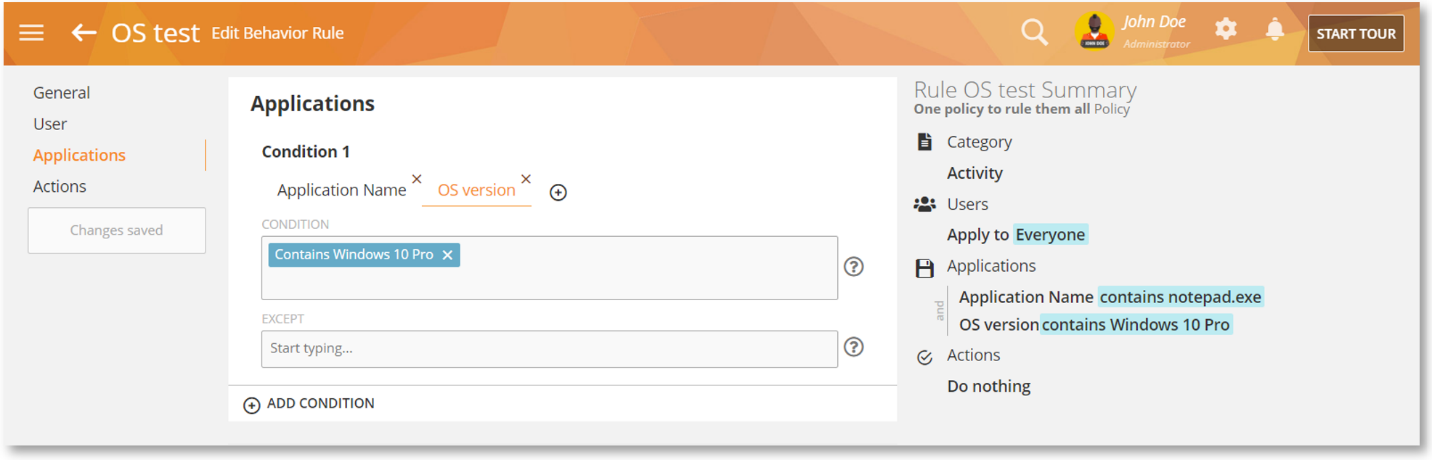
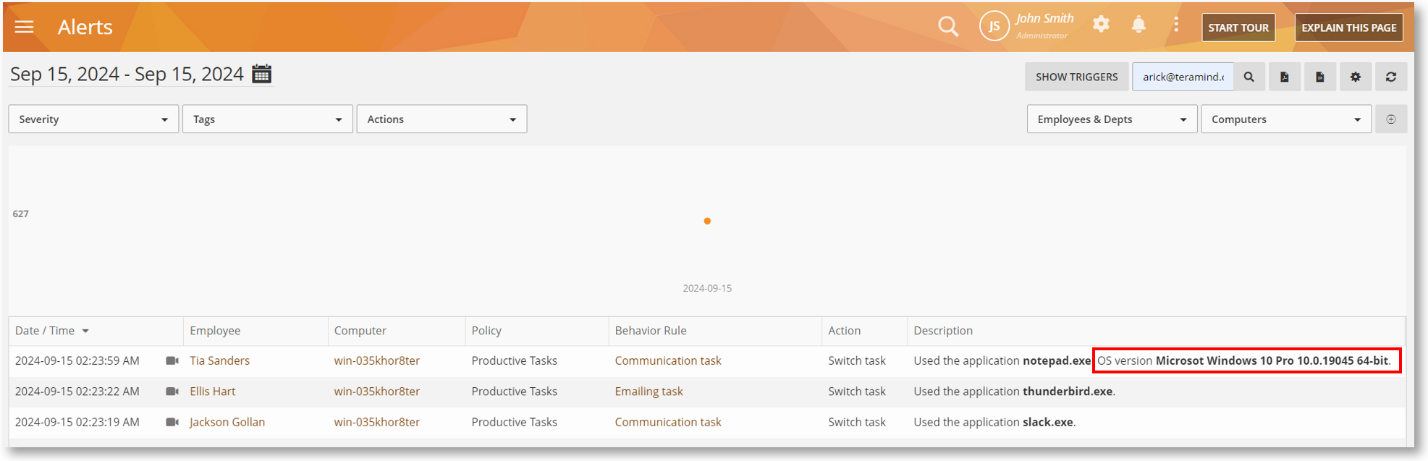
The detected version of the OS will be displayed in the alert’s description on the BI Reports > Behavior Alerts and the Behavior > Alerts reports.
Ability to Change the OCR Rule Notification Frequency
Category: Behavior Rules
By default, the OCR Notification Alerts are limited to 1 per rule/application/agent/computer in a 4-minute window.
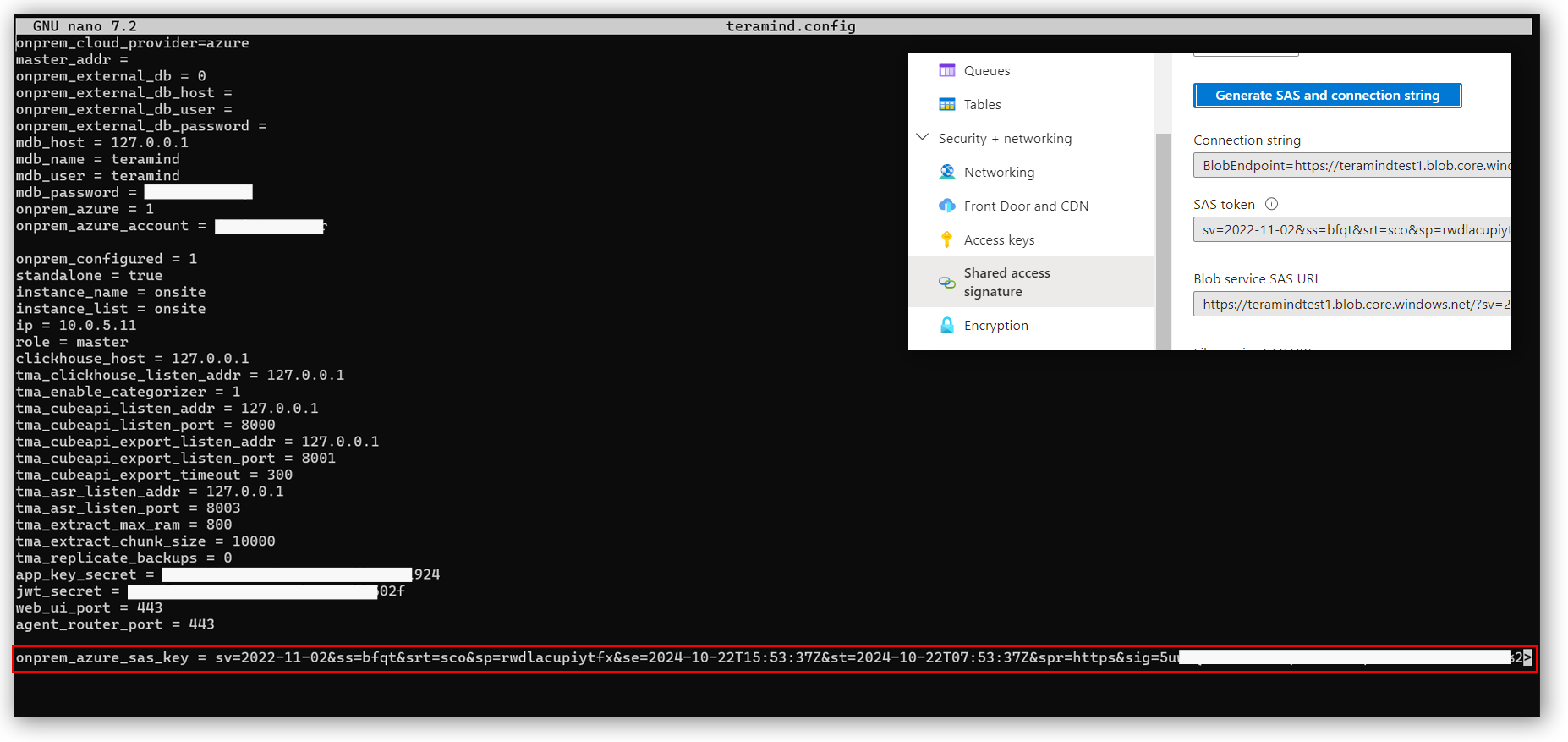
If you are an On-Premise customer, you can now receive all the alerts by adding the following parameter to your teramind.config file:

Deployment & Security
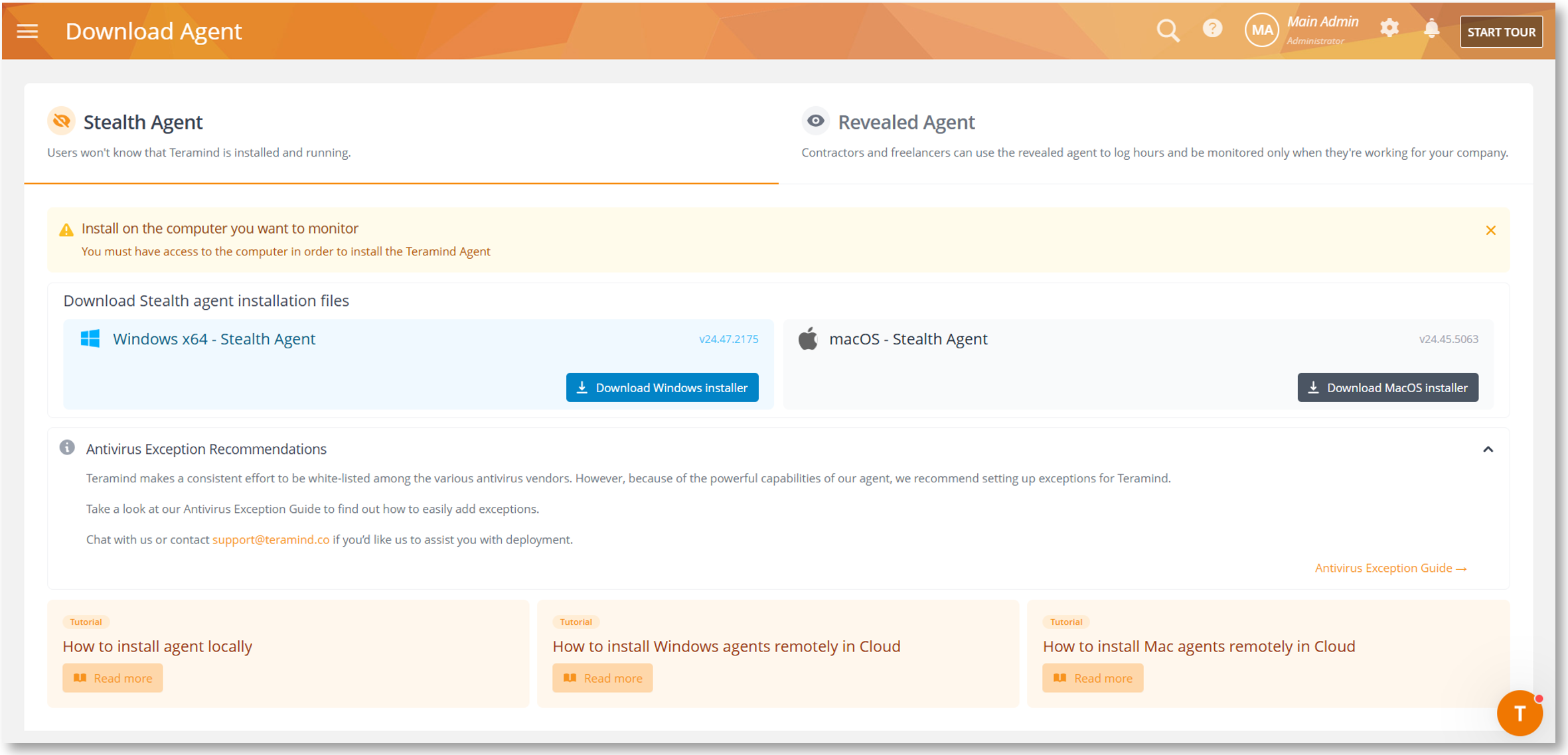
New Agent Download Screen
The Download Agent screen is now updated with a new interface and resources.
Support for New Authentication Method for Azure Storage Accounts
You can now use the Shared Access Signature (SAS) Token to access your Azure storage bucket, in addition to the Primary Access Token. This update provides more flexibility for secure access.
Mac Updates
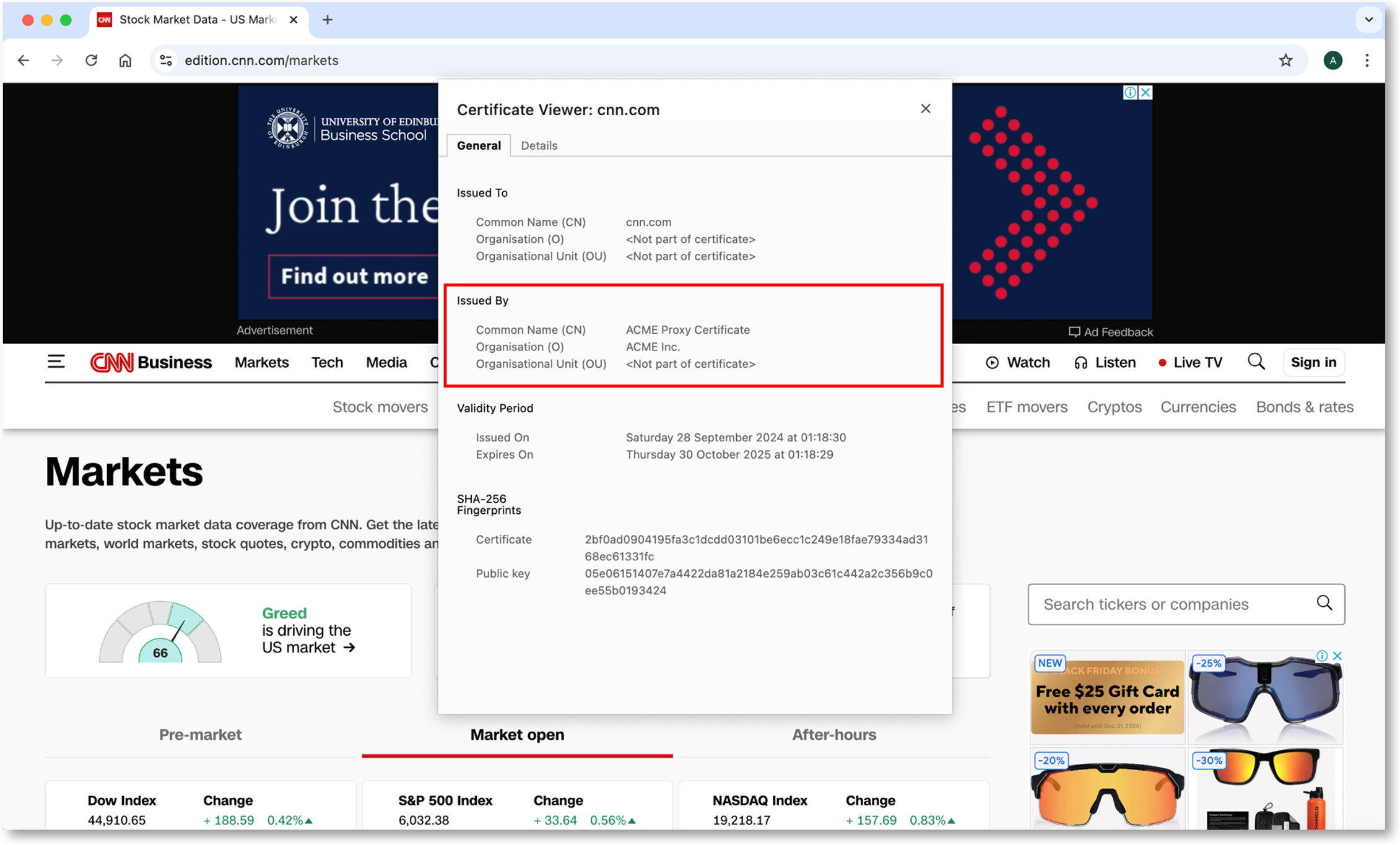
Ability to Use a Custom Proxy Certificate
Previously, the Mac Agent came with its own proxy certificate named “Internet Widgits”.
Now, you will be able to use your own custom certificate and assign it whatever Common Name (CN) you want. For example, “ACME Proxy Certificate”.
Other New Features & Improvements
This release also comes with several enhancements in BI reports, remote troubleshooting, Mac, etc. See the highlights below and check out the full list here.
Enhanced Activity Monitoring
We’ve enhanced our monitoring and tracking features to make them even more efficient. Key updates include optimized email monitoring that uses less RAM, improved offline printer handling, more precise geolocation tracking, support for the new Microsoft Teams API, a streamlined way to manage monitoring profiles, and conditional registry events processing.
Optimized Agent Services
Key upgrades to the Agent and its services have been made to improve performance, stability, and security. These include certificate caching for faster connectivity, optimized threading, enhanced automated logging for the Revealed Agent, and more.