Check out the highlights from our most recent update, Platform Release 672. This is our biggest release so far with 918 features, improvements, and bug fixes. See the highlights below. For a full rundown, check out the complete Release Notes here.
Table of Contents
- Introducing Omni: AI-Based Insider Threat Detection
- Activity Tracking and Behavior Analytics
- Behavior Policy & Rule
- Active Directory Integrations
- Technical Support
- New API Additions and Improvements
- Agent Improvements
- Mac Updates
- Communicate Securely and Anonymously with HTTP and SOCKS Proxies
- Other New Features & Improvements
Introducing Omni: AI-Based Insider Threat Detection
“Omni” stands for ‘all’ or ‘universal’. It’s Teramind’s AI/ML module that’s currently in public beta.
Omni provides a snapshot view of the most critical insights and incidents about your organization in a social media-like interface with scrolling video feeds.
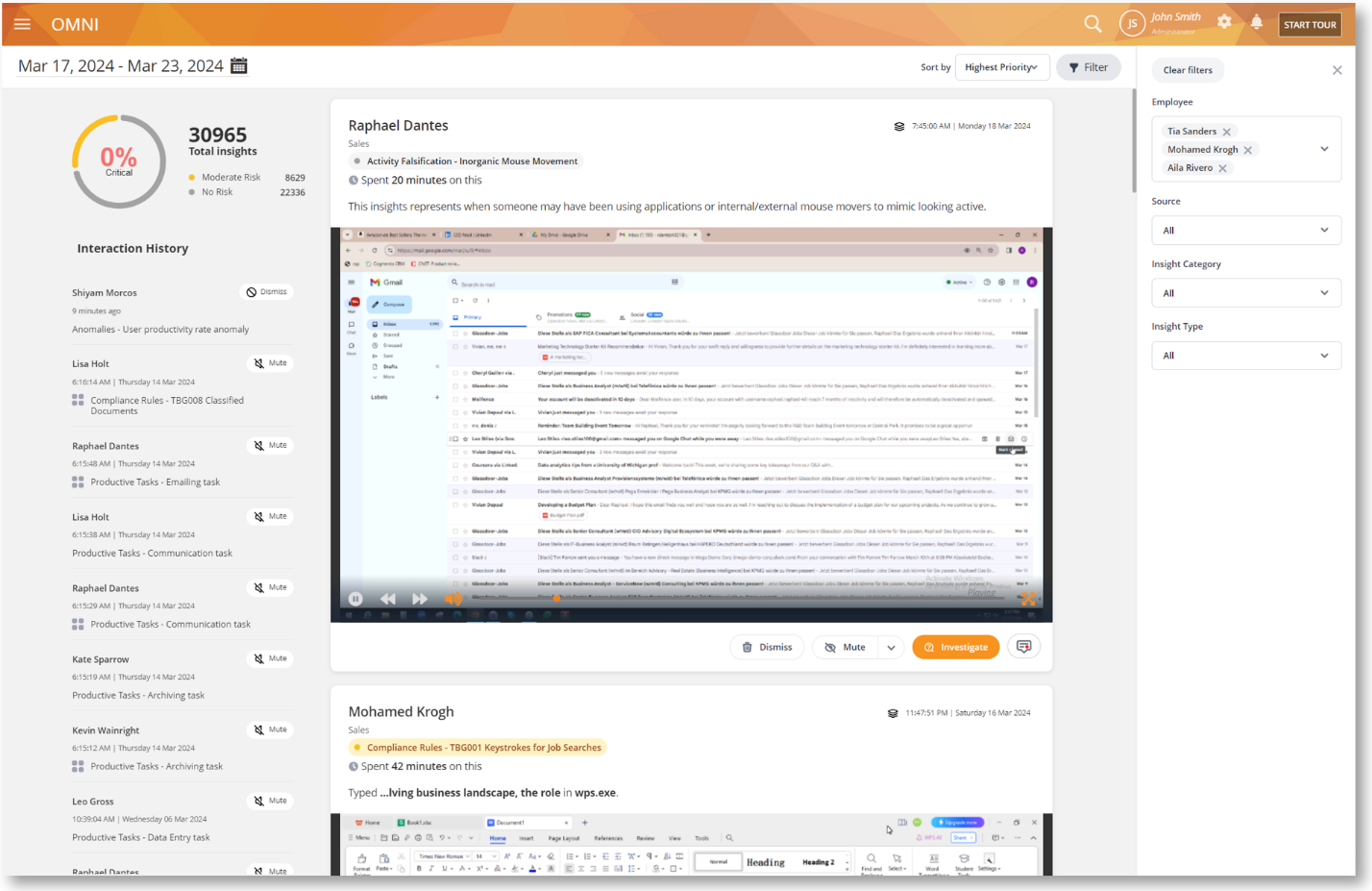
It’s an oversight tool that will help business owners and managers keep an eye on the organization’s security and productivity without digging through detailed reports. It’s also a powerful investigation tool that can be leveraged by your analysts for identifying threats, detect anomalies, flag frauds, etc., and conduct forensic investigations, and case management for data leak incidents.
Omni will provide predictive analytics, insider risk scoring, anomalous persona drifts, and sentiment analysis.
Activity Tracking and Behavior Analytics
Find Out Onsite and OOO Employees with the New Geolocation Features
We have introduced several new features related to geolocation that will make it easy for you to track in-office and out-of-office employees.
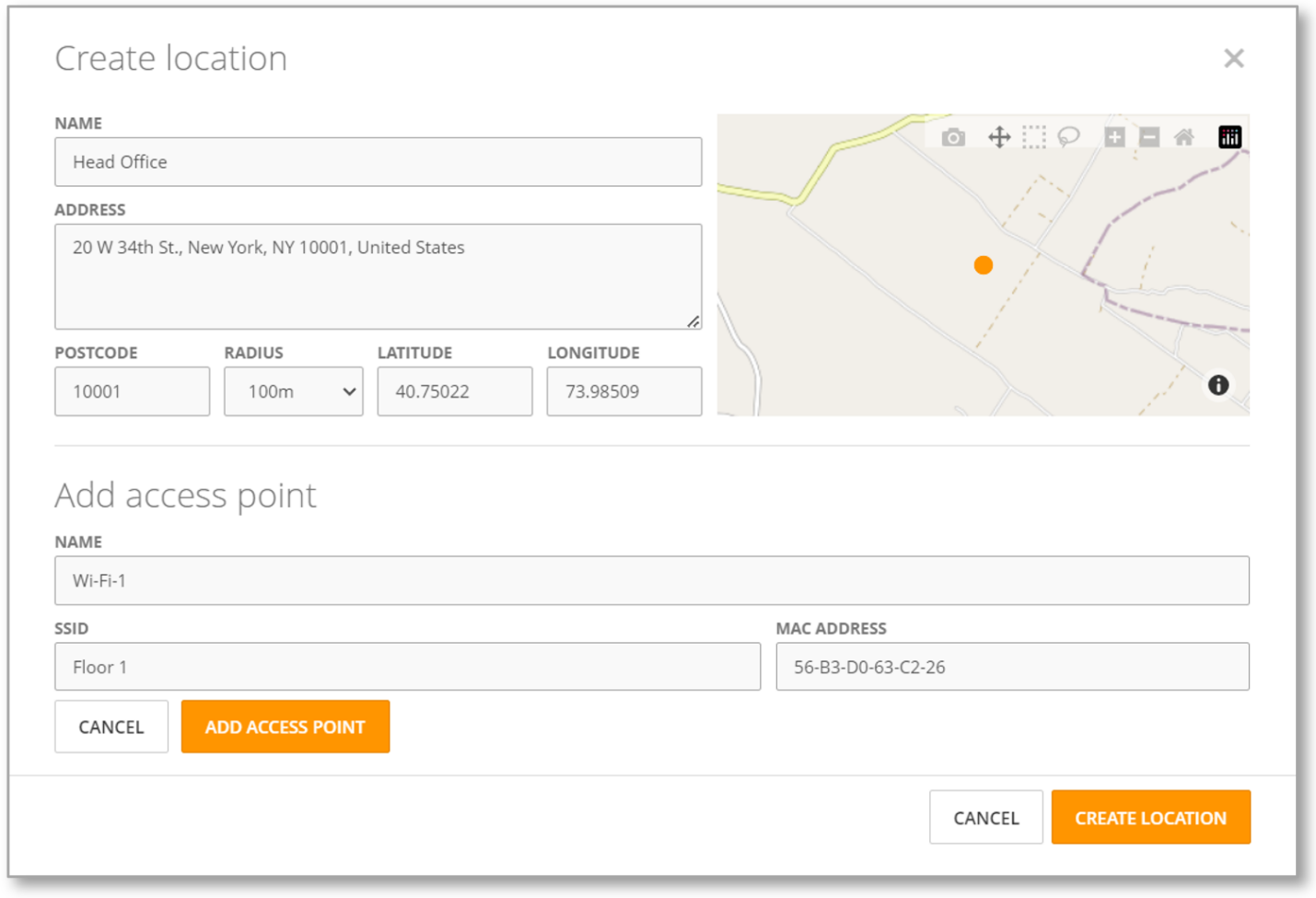
Create Custom Locations
We have added a new Locations sub-menu under the Configure menu. The Locations screen will allow you to create your custom locations using geolocation and network access points. Teramind will then match a user’s geolocation and network information (e.g., Wi-Fi names) to determine if the user is in a particular location.
Use the Custom Locations with the BI Reports
As part of this feature, a new “Office” Dimension is added to the BI reports. It can be used with any Chart or Grid widget. The Office location will show if a user is in any of the locations created under the Configure > Locations screen. If not, they will be shown as “Out-of-office”. For example, here the Application & Websites report is shown with the Office column on the grid widget:
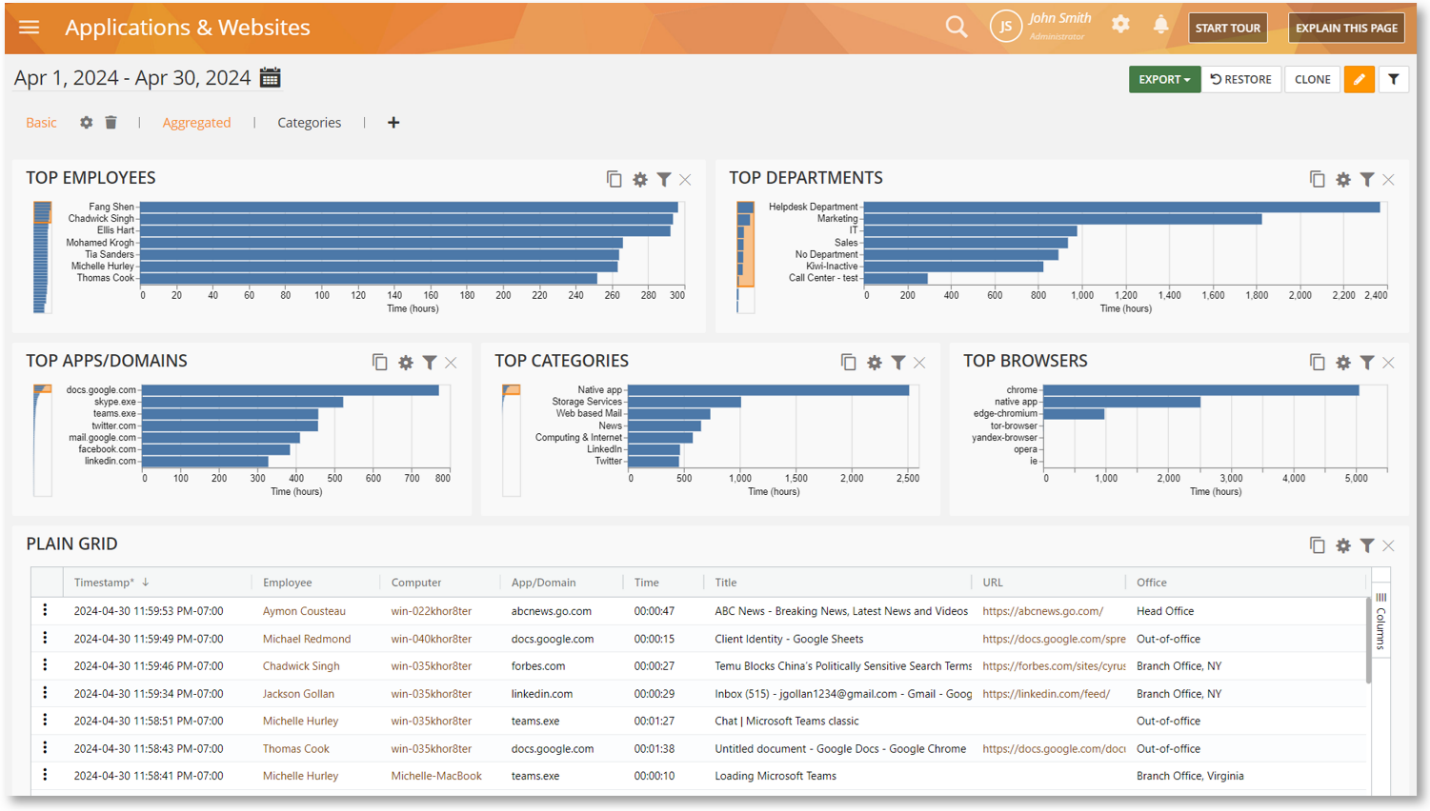
View Location Information on the Online Employees Widget
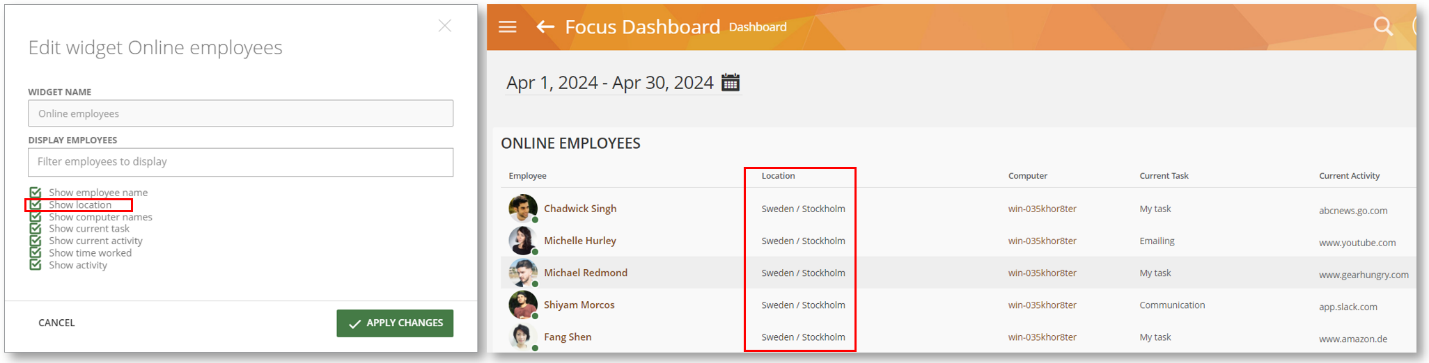
The Online Employees Dashboard widget is also updated to show location information:
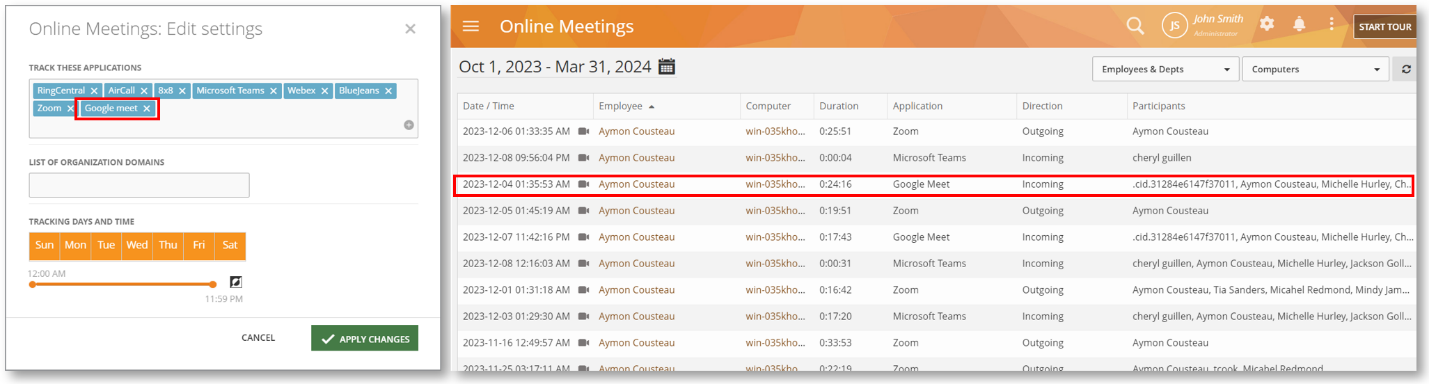
Monitor Online Meetings on Google Meet
We have added support for Google Meet monitoring. You will be able to select it from the Monitoring Settings > Online Meetings window and view the meeting activities on the Monitoring > Online Meetings report:
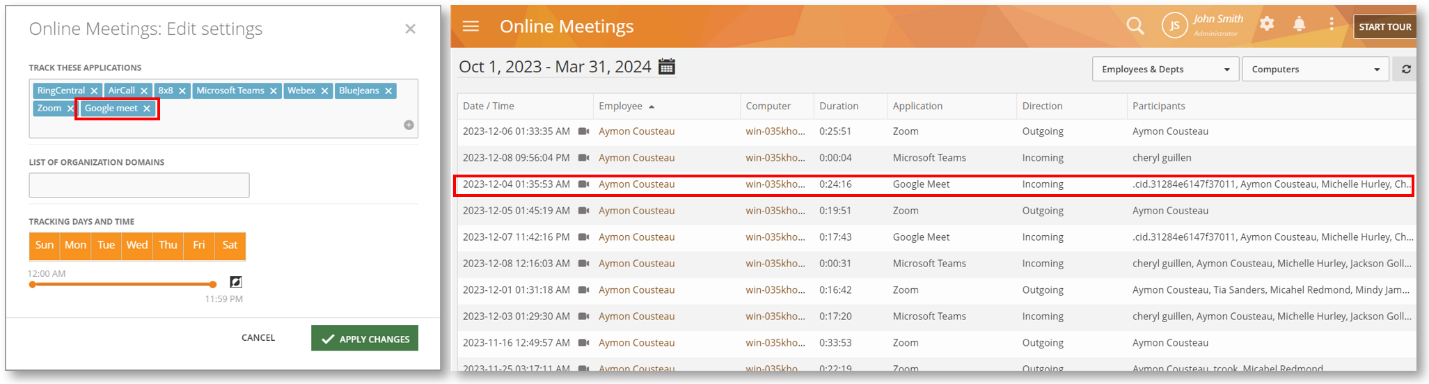
Google Meet has over 31% of the market in web-and-video-conferencing market. If your organization is using Google Workspace, chances are your employees are using it for day-to-day business communications. It’s also used by users for personal chats.
With support for Google Meet monitoring, you will be able to track these meetings and chats. You will be able to view who is participating in the meetings, if it’s incoming or outgoing, etc. Additionally, if the audio and screen recording are turned on, you will be able to view and hear the conversations.
Track IM Conversations on WeChat
We have added support for WeChat monitoring. You will be able to select it from the Monitoring Settings > Instant Messaging window and view the IM activities on the BI > Instant Messages and Monitoring > Instant Messaging reports:
WeChat is becoming one of the fastest-growing chat platforms. With the ability to view its usage, you will be able to see which of your employees are using it, who they are chatting with and if it poses any threat to your communications strategy. By monitoring the conversation, you will understand employee sentiment and conduct psychometrics analysis of the conversations.
You can also create behavior policies and rules to prevent data exfiltration via messaging or attachments.
Behavior Policy & Rule
Change Rule Violation Severity, Use It for Risk Analysis
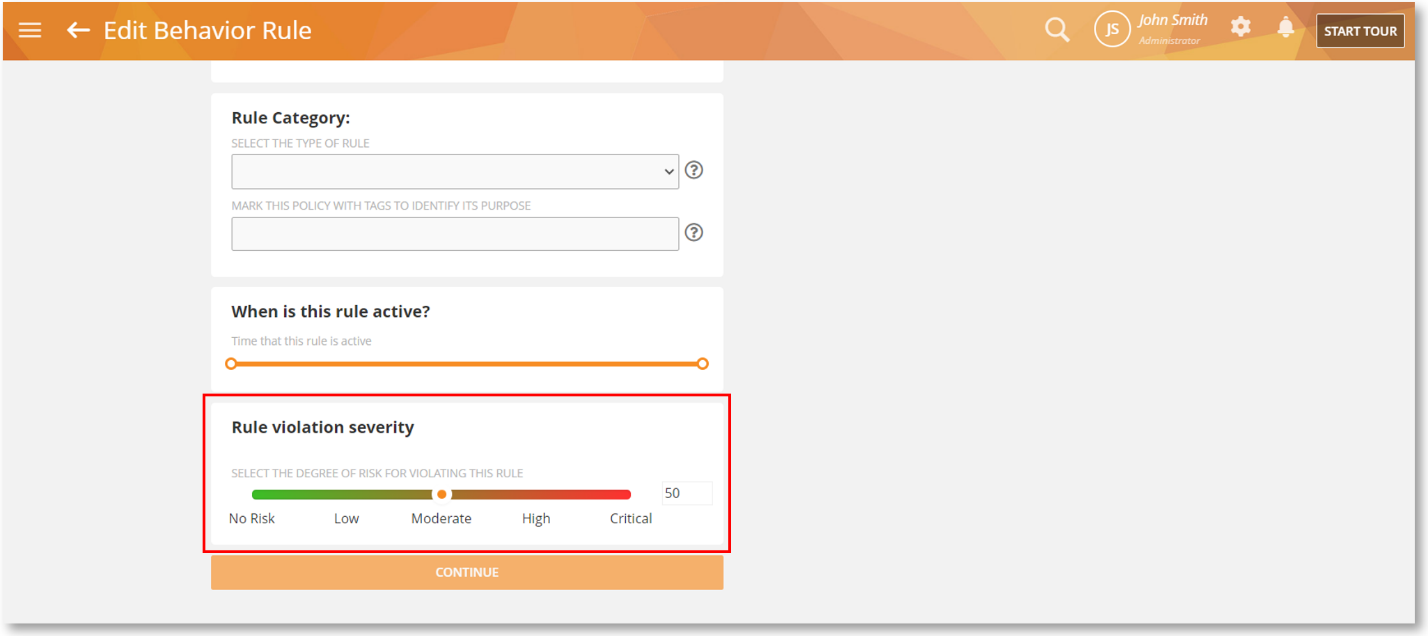
We have added an option to adjust the risk severity of all rules. It can be found below the General tab on the Rules Editor:
The severity is also shown on the Behavior > Policy screen:
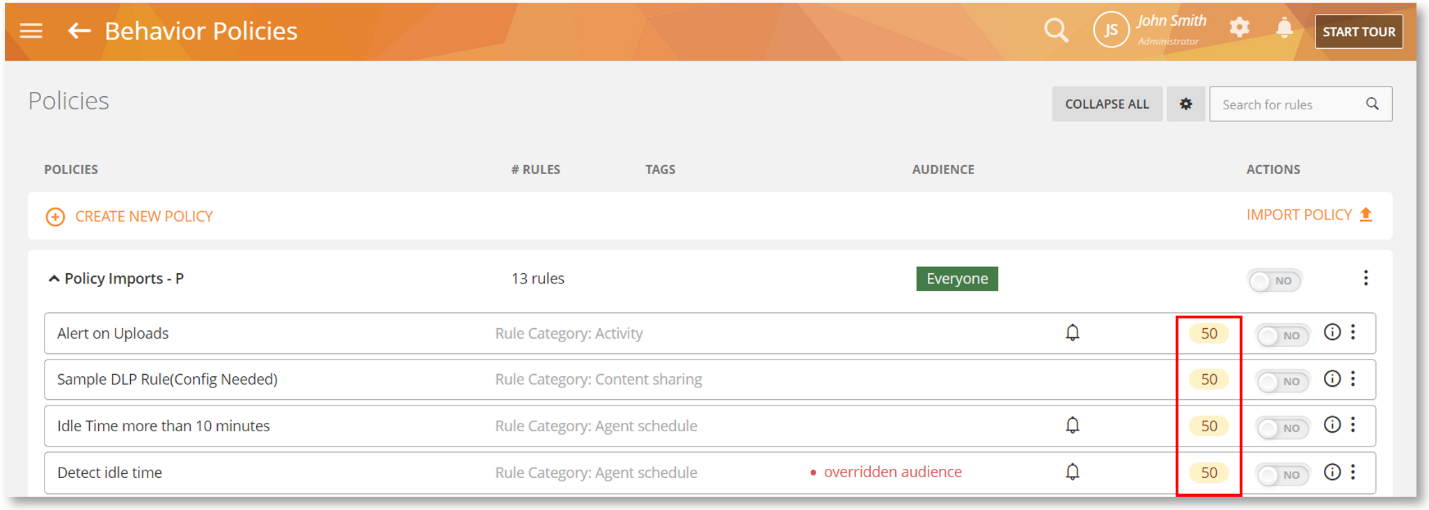
Rule violation severity is a way to understand the risk aptitude of a user’s behavior when they violate certain rules. This information will be used with Omni to understand your overall risk posture and if needed, drill down to specific risk indicators and profile them for better risk management.
Conducting a risk analysis can help you determine what users or resources are vulnerable in your organization and what actions you should take to protect your interests. This type of analysis will facilitate a balance between risks and risk reduction.
Use the Improved Windows Log Event to Respond to System Events
Windows events are all the activities tracked by Windows. These include Applications, System, Security, Hardware, etc. The ability to detect these events is a very powerful tool because it allows an administrator to identify issues with the computer, discover security gaps, and stop potential threats.
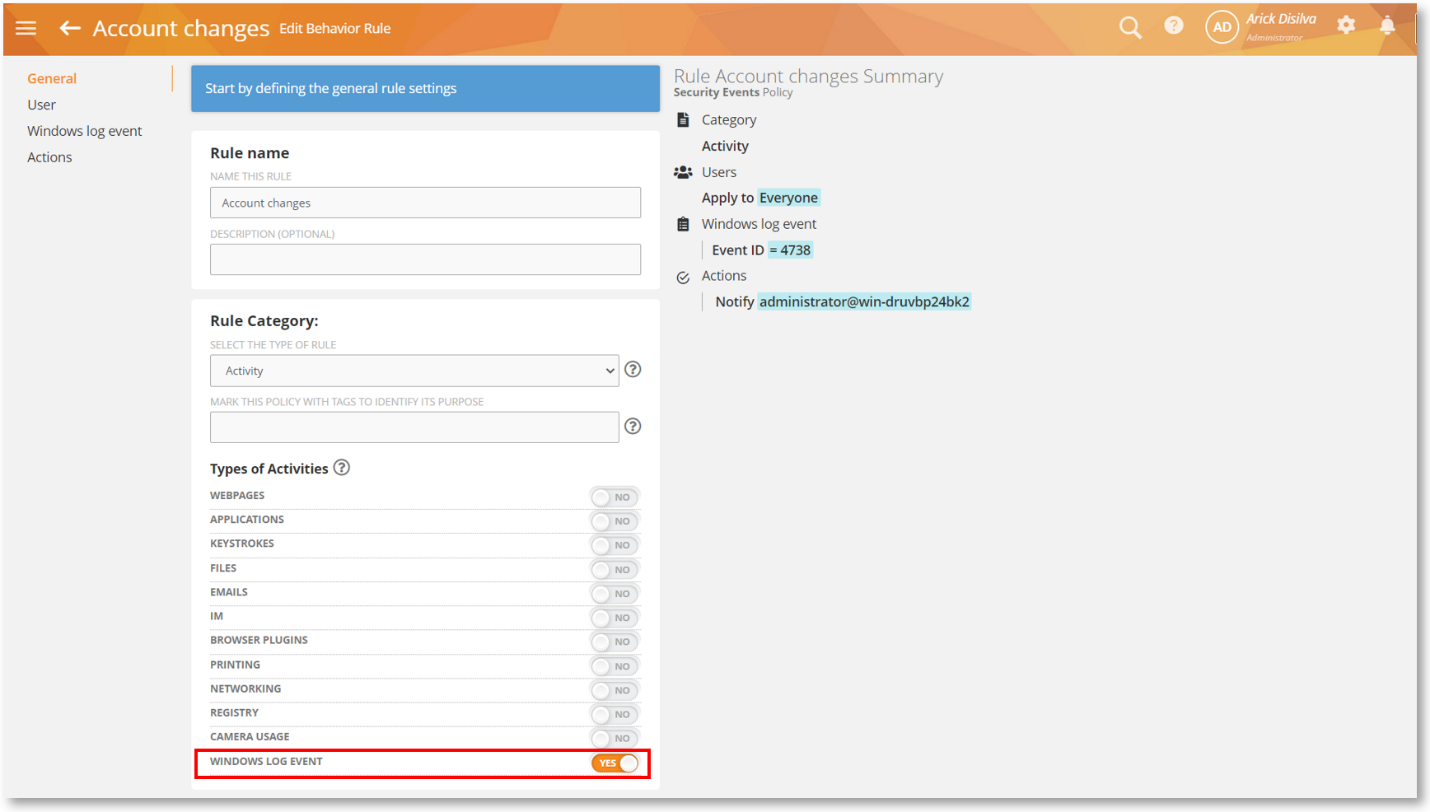
We introduced the Windows Log Event rules in Platform Release 650 to detect these events and respond to them automatically with rule actions. We have made two critical improvements since then to make it more streamlined, faster, and better:
Detecting Events without a User ID
Currently, the Agent only triggers any Windows Log Event rule for the currently logged-in user. To do so, it checks to see if any event generated by Windows has a user ID and matches that with the current user. However, many events such as login, logout, lock, power state changes, starting PowerShell, etc. do not have any user ID associated with them. The Agent wouldn’t trigger any rules for those events.
We made changes to the Windows Log Event so that the Agent will now trigger a rule even if it doesn’t have a user ID. We have also built a mechanism so that on a computer with multiple users (e.g., a terminal server), it will not duplicate the same event for multiple users and trigger such an event only once.
Better Windows Event Logs Processing
Previously, for the Windows Log Event rule to work, the Agent would process the entire Windows event log making this process slow and cumbersome. Especially, if you had multiple users on the same computer.
Now, we have made improvements so that the Agent will subscribe to the OS event channels (e.g., Authentication, Services, Process-Execution, Object-Manipulation, Sysmon, etc.) and listen to the Event IDs specified in the rule. This way, it will not have to scan the event log all the time. This should boost the performance and processing time significantly.
Active Directory Integrations
We have added several features for better Active Directory LDAP Group support.
LDAP groups are organizational units within Active Directory that streamline user management and access control. LDAP Groups simplify administration by allowing common attributes and permissions to be assigned to multiple individuals simultaneously. LDAP groups and roles are essential for efficient identity and access management within an organization.
By allowing Groups supports with employee and computer management in Teramind, we made it simpler to help you filter the report by LDAP groups making tighter AD-Teramind integration possible.
Filter Employees and Computers by LDAP Groups
We have added a new filter, “LDAP Groups”, to the Employees and Computers screen.
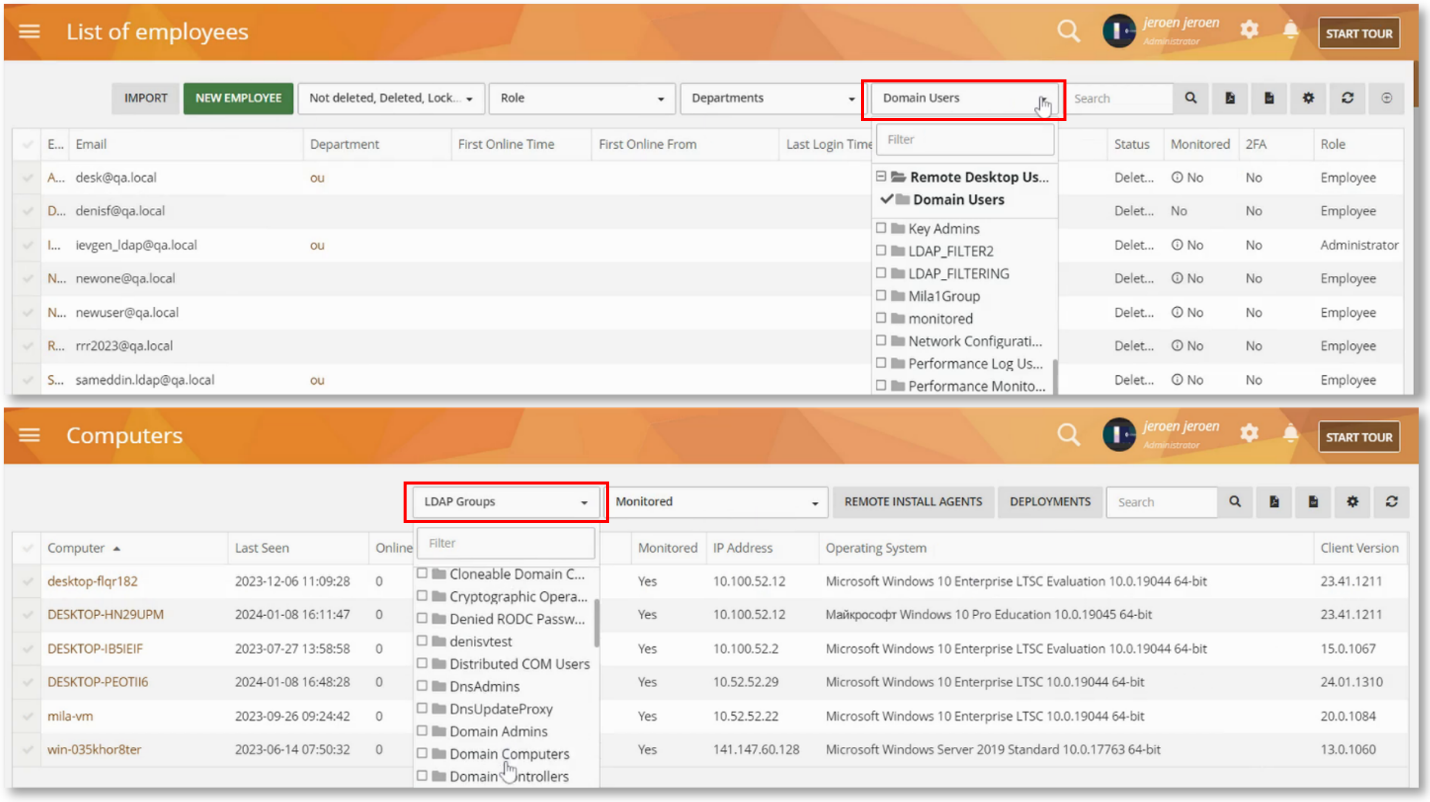
This will help you filter the report by LDAP groups if you have an Active Directory integration set up.
Show LDAP Group Info on Employees and Computers Settings
We have added the ability to view which LDAP groups an employee belongs to from their Monitoring Profile > PERSONAL INFO tab, and on the Computer’s Settings window:
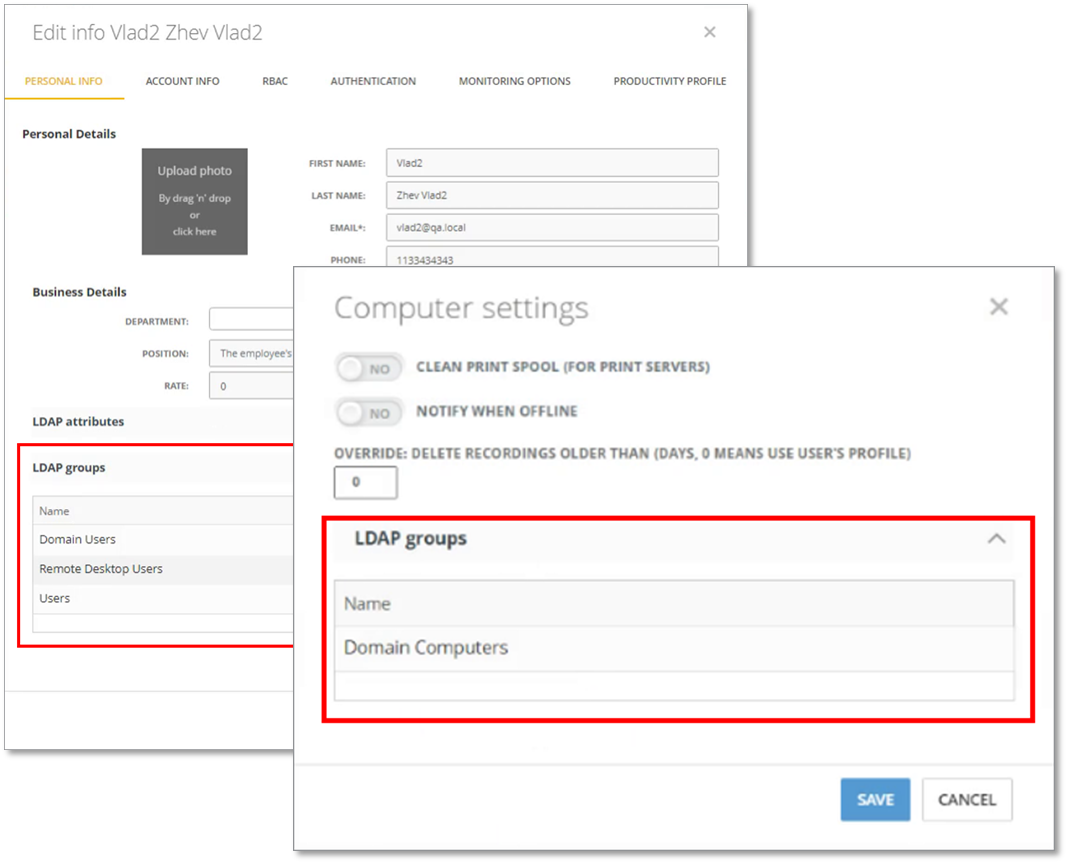
This will help you quickly find out which LDAP group an employee or computer belongs to.
Technical Support
Conduct Computer Troubleshooting Remotely
We have added a TROUBLESHOOTING button to the Computers > Computer’s Details screen:
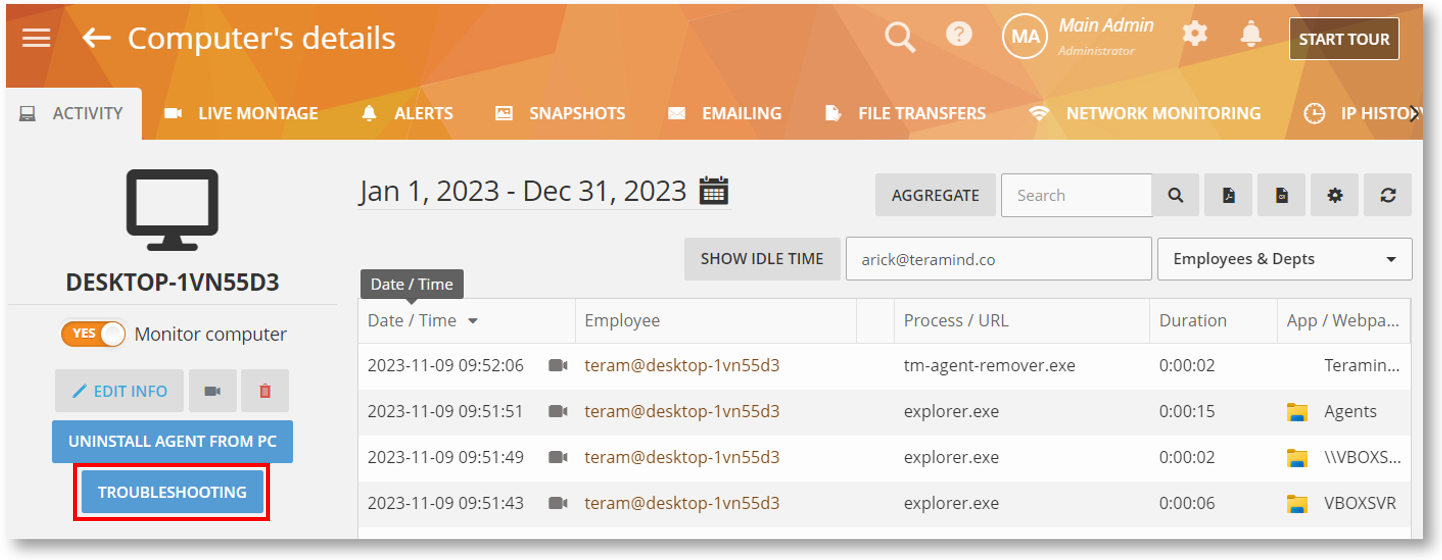
The remote troubleshooting feature will allow you and Teramind Support Engineers to conduct troubleshooting of a computer and collect diagnostics logs. This feature will let you run troubleshooting from the dashboard instead of accessing the computer locally or through a separate remote session (such as TeamViewer). It works without interrupting the Agent or revealing the troubleshooting to the user:
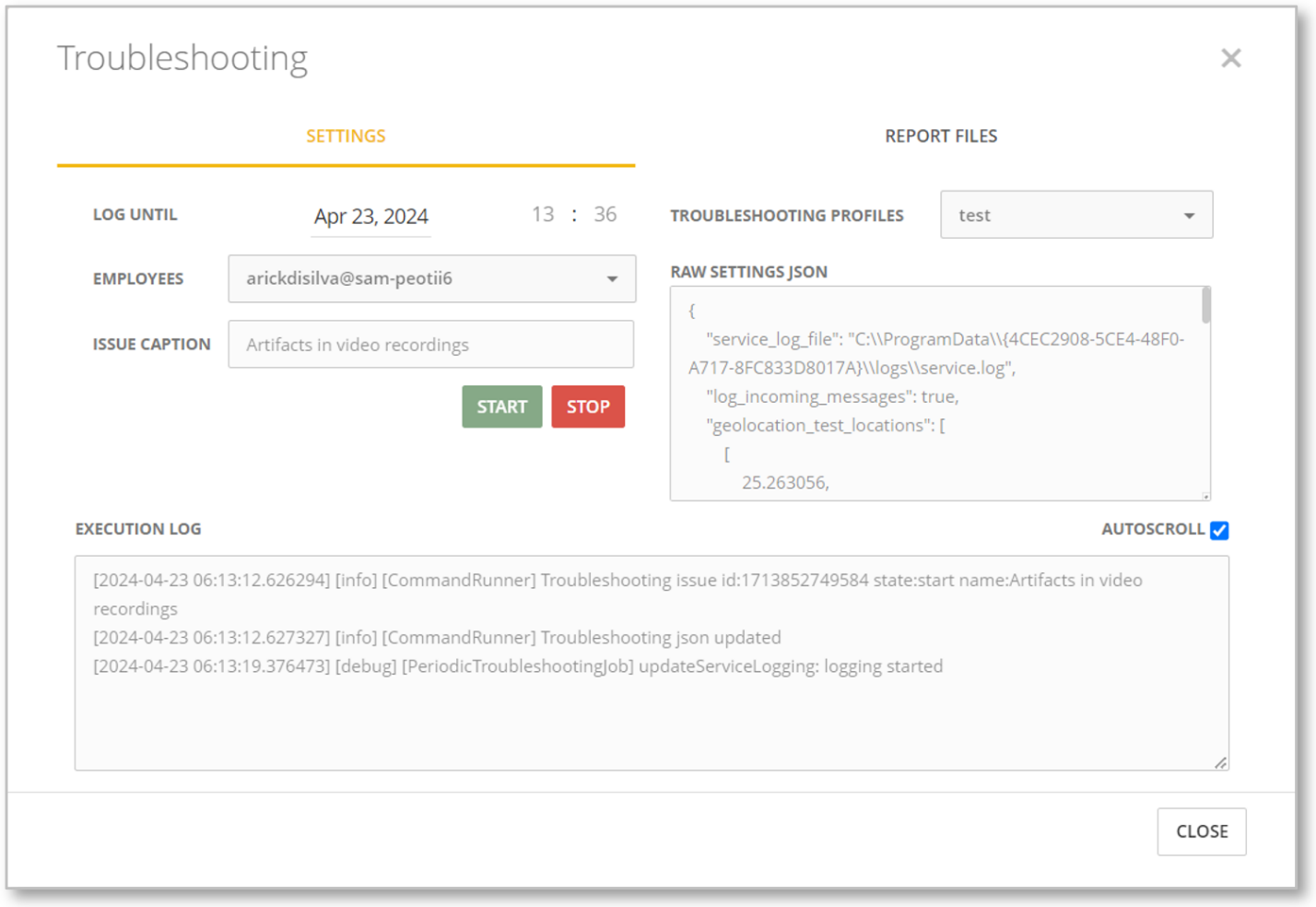
In the future, Teramind Diagnostics Tool (TMDiag) will be incorporated with the troubleshooting feature making it even more powerful.
Use the New Chat for a Faster and Better Support Experience
We have migrated our support system to Intercom. This will let you have a better support experience by giving you direct access to our support agents and Knowledge Base content powered by AI.
Cloud customers will be able to access the support by clicking the T icon near the bottom-right corner of the Teramind Dashboard. On-Premise customer will be able to access the same icon from their Self-Serve portal. The support chat can also be accessed from the Teramind website and Knowledge Base.
New API Additions and Improvements
APIs allow you to integrate the Teramind system with other third-party solutions, your own custom applications, and help automate tasks that are otherwise too difficult or impossible to achieve through the user interface.
Teramind has a robust set of APIs, and we keep adding new features and improvements to it. In this version, there were several such improvements made:
Filter BI Report by Measures & Dimensions Together
Previously, it would have been impossible to filter a BI report with both Measures and Dimensions together. For example:
Now, it’s possible to apply filters by both Dimensions and Measures together. For example:
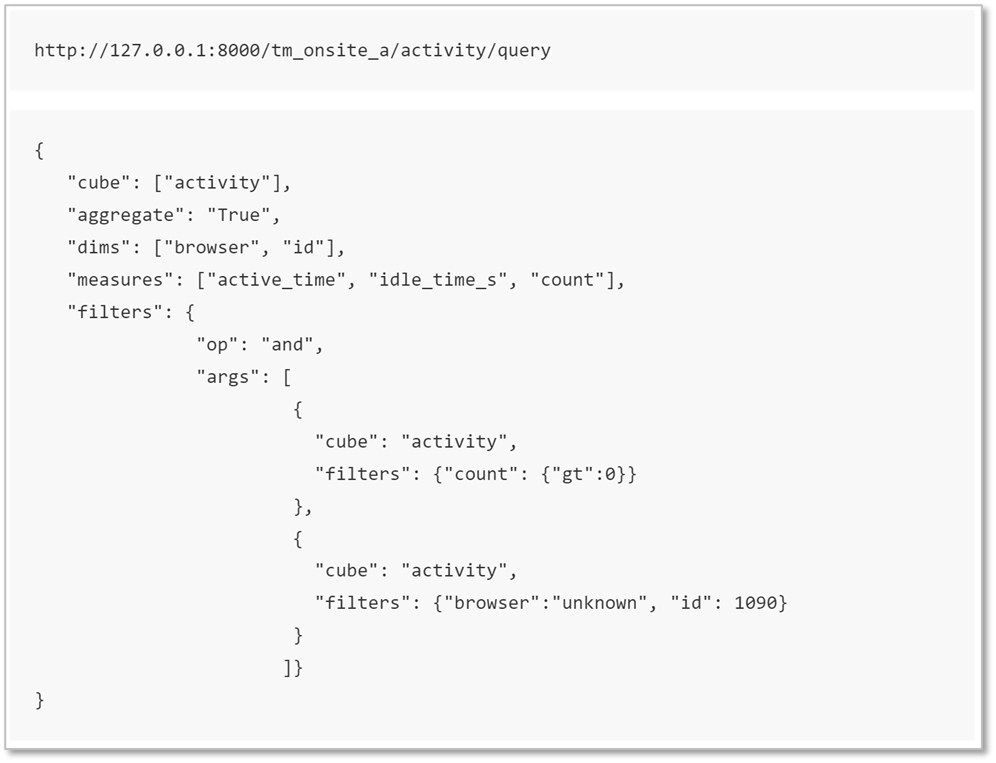
This will help you generate complex quarries easily and build custom reports using the API.
Get/Update LDAP Groups Easily
We have added an API command, /tm-api/ldap/groups/content that can be used with a GET method to retrieve a list of Active Directory LDAP groups. A POST method can be used with the same command to change the group:
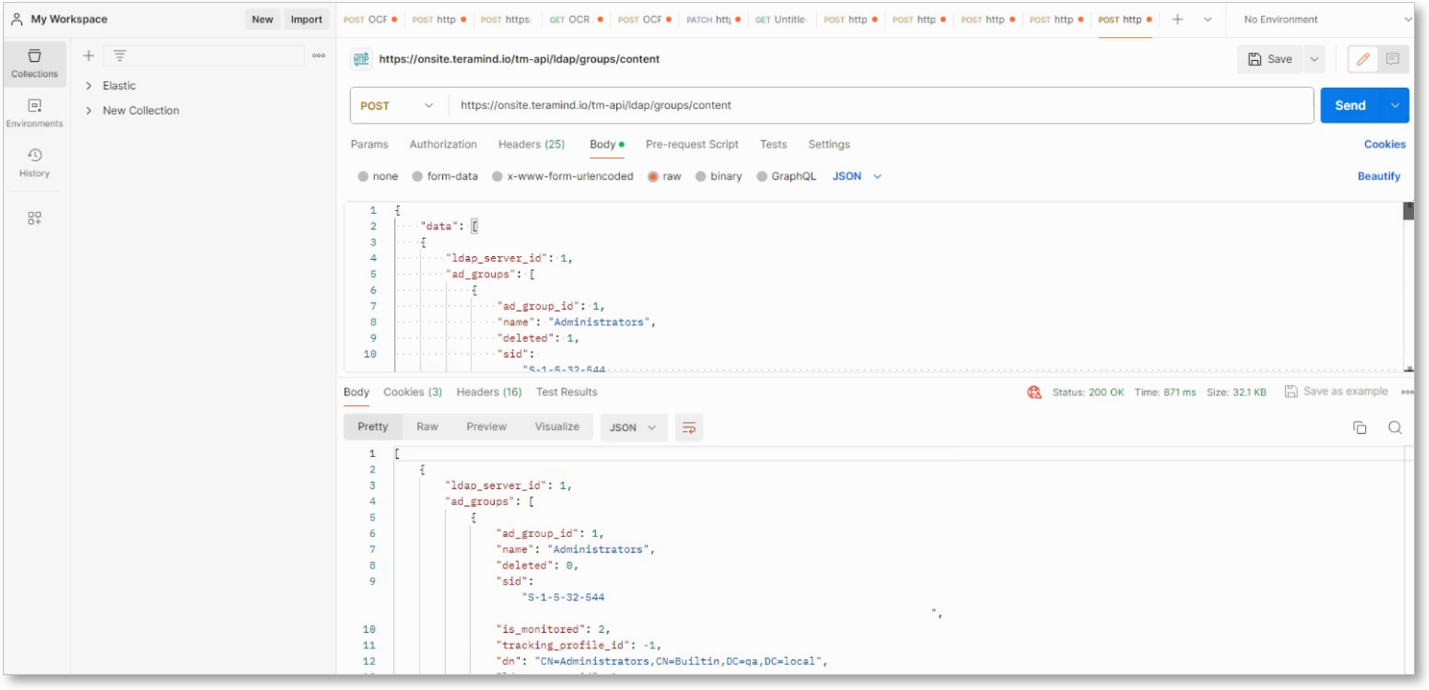
This will be helpful in situations where you may use solutions like BambooHR to manage employees and computers. With this API call, it will be easy to synchronize user groups and their associated resources, such as computers and employees, between Teramind and the other solution.
Agent Improvements
We have made at least ten distinct improvements to the Agent around performance, stability, reliability, and usability. Some of these include:
Improved Network Monitoring
Previously, if you had a slow network connection, the Agent would frequently disconnect, cause poor performance, or other network issues.
We have improved how the Agent handles and transfers heavy workloads such as screen and audio recordings so that it will perform much better on slower networks causing fewer dropouts and other connectivity issues.
Performance Fix for Windows Location Service
Due to a bug with the Windows Location Service (which the Agent uses for the Geolocation feature), on some systems, network performance would drop every time the Agent collected the location data. By default, it was set to 30 seconds. For this reason, the network performance would drop every 30 seconds too.
As a fix, the Agent will now collect Geolocation data based on the TIME THRESHOLD value set under Monitoring Settings > Geolocation. This will reduce the effect significantly.
Better Connection Attempts
Previously, if the connection took more than 10-70 seconds, the Agent would drop the connection and try to initiate a new connection afterward. This was inefficient and would cause more connection attempts than necessary.
We have implemented some changes that will allow the Agent to wait for up to 120 seconds before it terminates a connection attempt. This will help improve the Agent connectivity and reduce network loads.
Better Handling of Password Manager Configurations
Previously, the settings for Monitoring Settings > ADVANCED > DISABLE BUILT-IN PASSWORD MANAGER OF KNOWN BROWSERS option was saved in Windows Registry:
This could interfere with the Windows Group Policy.
We made changes so that the settings for the password managers will be handled by the Agent and not saved in the Windows Registry.
Automated Task Restart
We have made changes so that if the Agent has to restart for some reason (e.g., the Agent service crashed and recovered), any active task will resume.
If the user has the “Stay logged in” option enabled, the task will automatically resume. Otherwise, the task will resume as soon as the user logs in.
Synchronized Updating of the Configuration File
Currently, the Agent Configuration file (config.cfg) is used by both the Agent and the services for reading and writing data. However, in rare situations, both of them might try to update the file at the same time causing a race condition. As a result, the file might get corrupted.
We have made changes to how the config file is handled so that any update/write to it will now be synchronized to avoid any race conditions.
Mac Updates
Prevent File Exfiltration with New File Transfer Monitoring Options
We have extended the File Transfer monitoring capabilities to support more options that were previously unavailable. The options will let you track network drives, monitor files by their type/extension, track specific locations, change the monitoring schedule, and do more.
All these options will let you keep an eye on sensitive and critical file movements and identify any data exfiltration events such as copying files to external drives, uploading to a cloud sharing site, etc.
Support for Monitoring the Network Drives
Previously, Files Transfers monitoring would only work for the Users folder, external drives, and Cloud drives (OneDrive).
Now, we have added support for network drives (SMB) too. All the supported file operations, e.g., access, copy, rename, delete, etc. will be captured.
The network drives will appear as “Volumes” on reports like the BI Report > File Events, Monitoring > File Transfers, etc.:
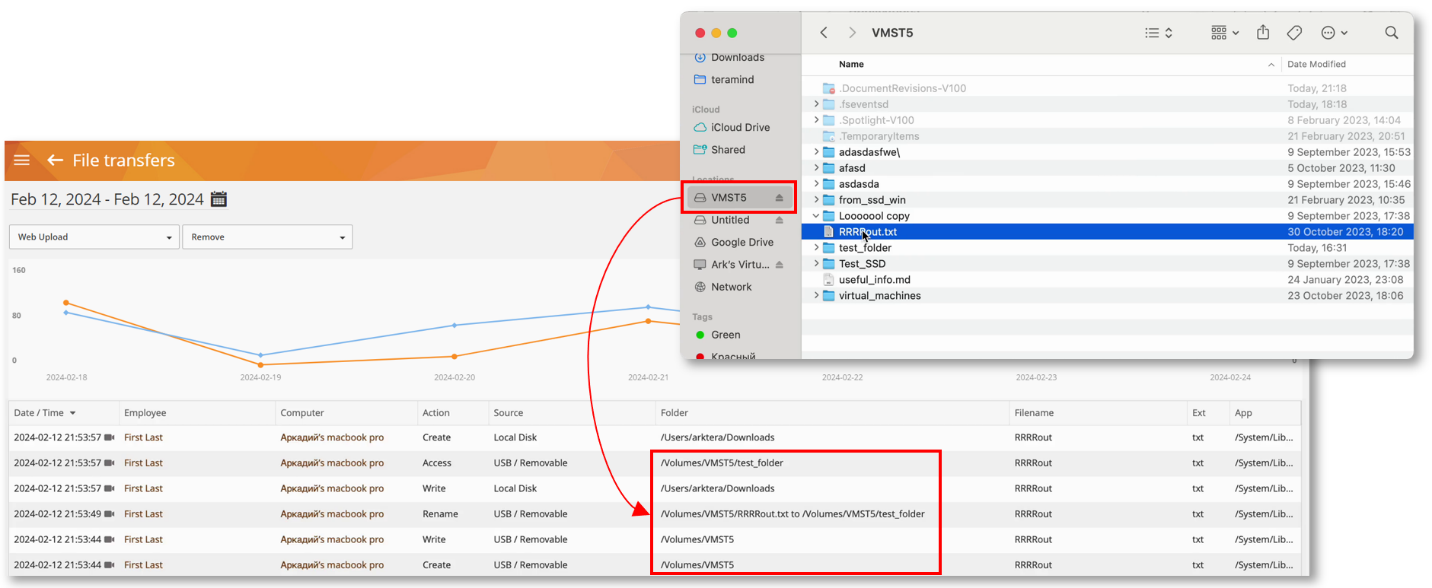
The Files behavior rules will also work for these drives.
Support for New File Transfers Monitoring Options
We have enabled Mac support for several File Transfers monitoring options.
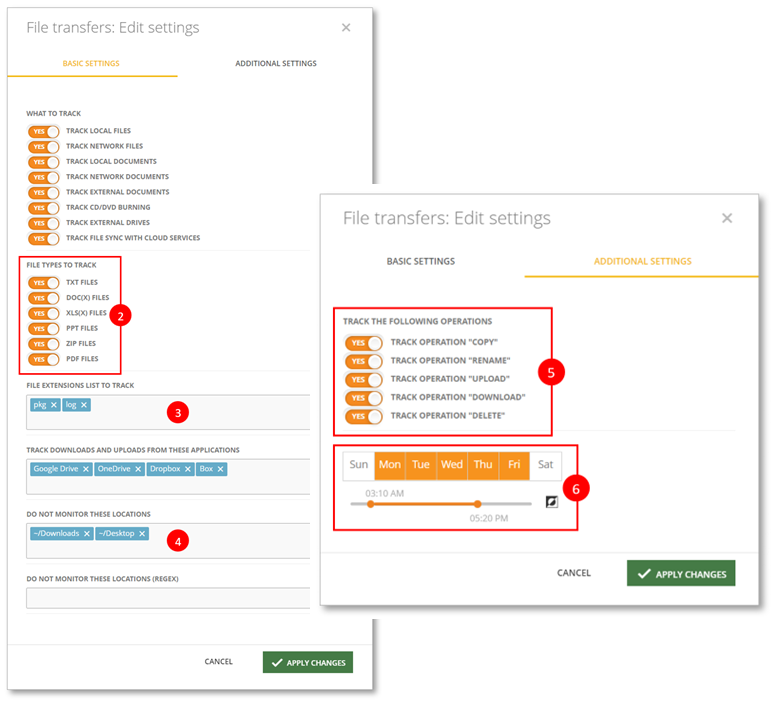
You can now turn File Transfers monitoring on/off by using the YES/NO toggle switch.
You can monitor file types/file extensions, exclude locations from monitoring, etc. You can also decide which file operations to track and specify the date and time of the monitoring schedule.
Detect Employee Productivity with Active, Idle, and Focus Time Criteria
Productivity Tracking with Applications Rules
We have added Time Active (min), and Time Idle (min), Time Focused, Total Time Active (min), Total Time Idle (min), Time Focused (min) criteria for Applications rules.
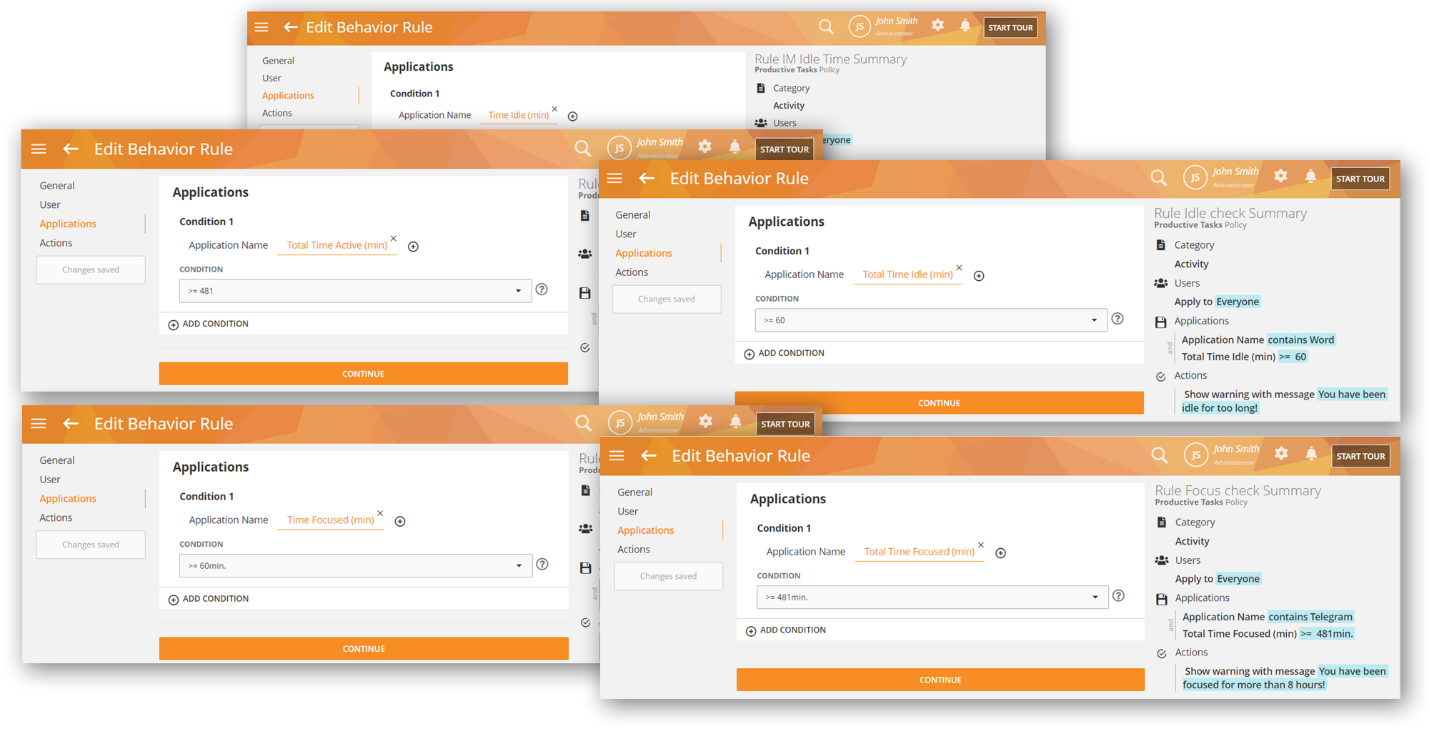
These rule criteria will help you track how the user is performing and respond accordingly. For example, if a user is idling for too long, show them a warning, if a user is active for too long on a social media app, notify the admin, etc.
Productivity Tracking with Webpages Rules
We have added support for the Time Active (min) and Time Idle (min) criteria in Webpages rules:
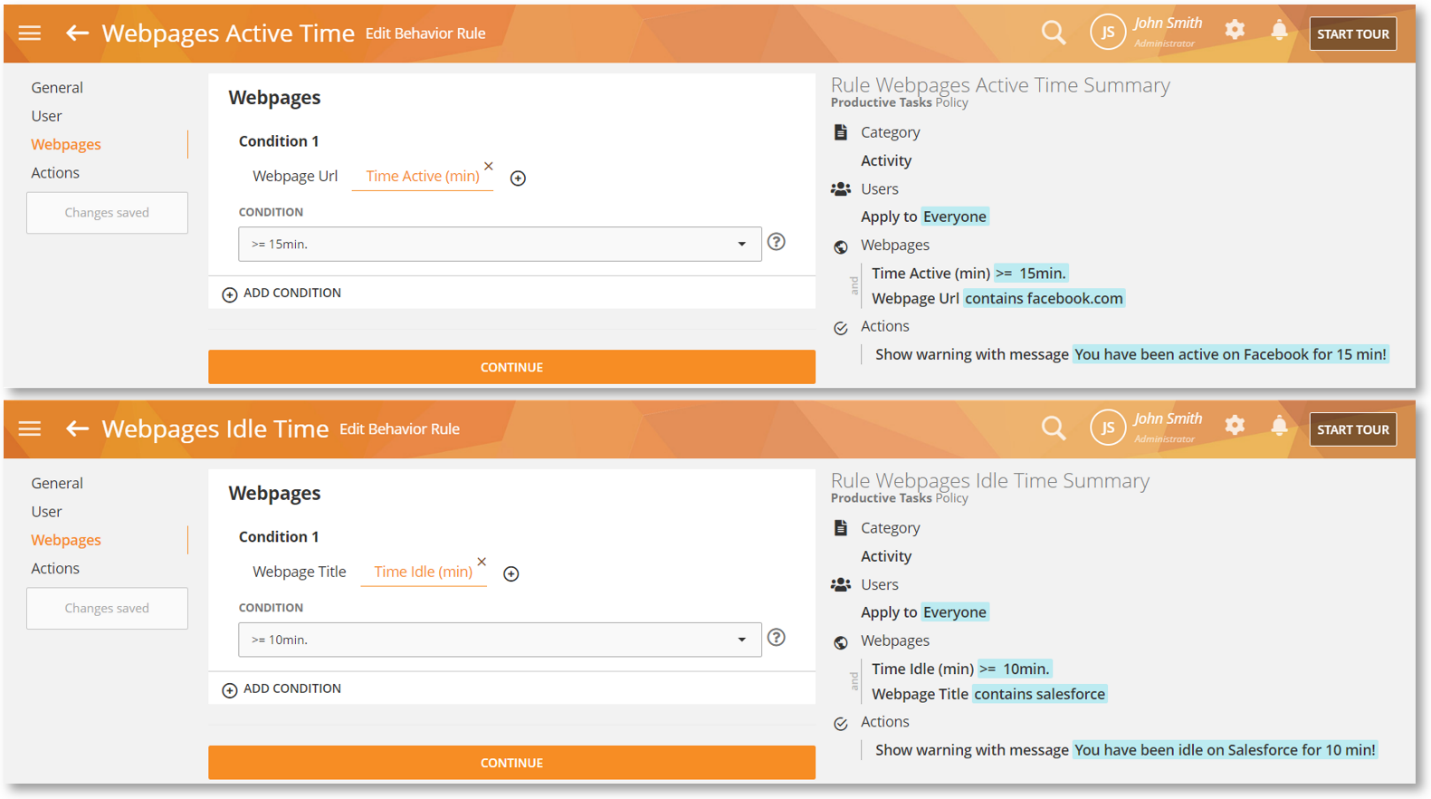
These rule criteria will help you track how a user is spending their time online. For example, if they are active on YouTube or idling while keeping open your CRM site (e.g., Salesforce), etc. potentially exposing sensitive information.
Communicate Securely and Anonymously with HTTP and SOCKS Proxies
Many organizations and individuals use HTTP proxy to detect and block suspicious traffic that can be an intrusion, virus, or malware. It also protects corporate web servers from external cyberattacks.
Similarly, you might use SOCKS proxy to hide your IP, facilitate communication with websites that have a firewall and limit regular client access, or overcome geo-restrictions.
Previously, the Mac Agent was unable to use these proxies.
From this version, we have added support for both the HTTP and SOCKS proxy.
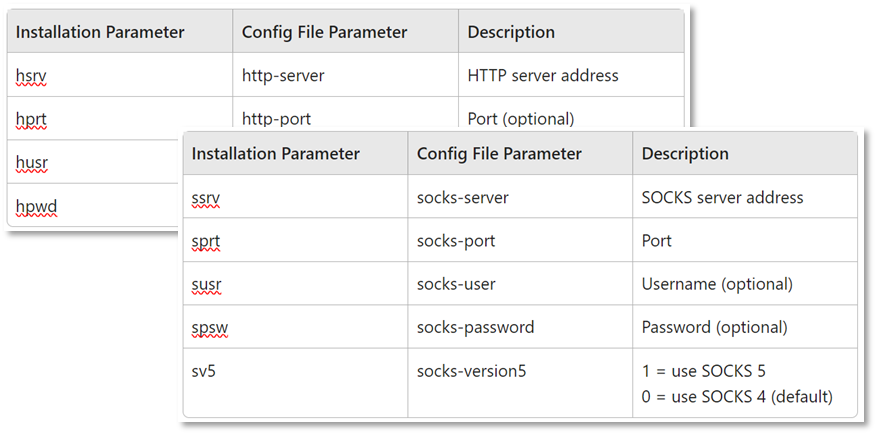
You can configure them from the Agent command line parameters or through the Agent configuration files. Both methods are discussed in the Agent Installation/Configuration Parameters (Mac) section of the Agent installation article.
Other New Features & Improvements
There are a lot more improvements packed into this release with several general enhancements to the UI, security, and performance. Below are just a few of them. Check out the full list here to get the details.
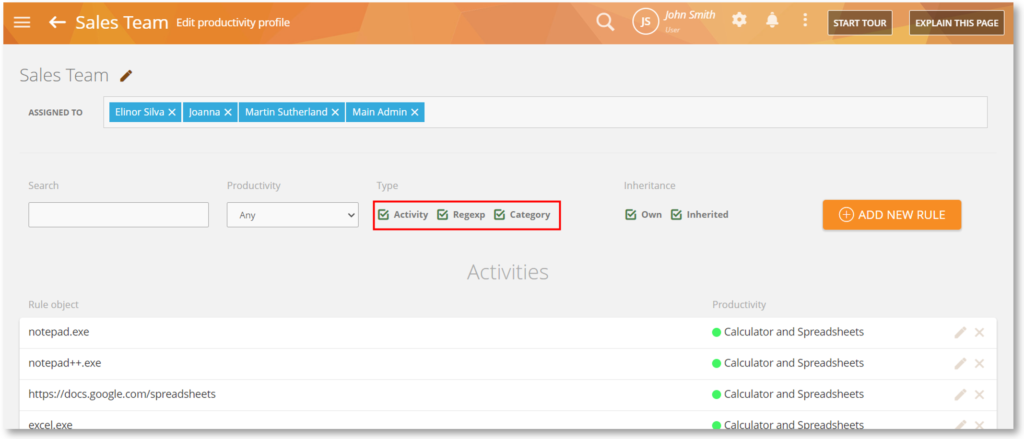
App/Web Classification Priorities
The productivity profiles used to classify apps and websites will now have the following priority: Activity, RegExp, and Category. This will help clarify how app/web activities will be classified and displayed.
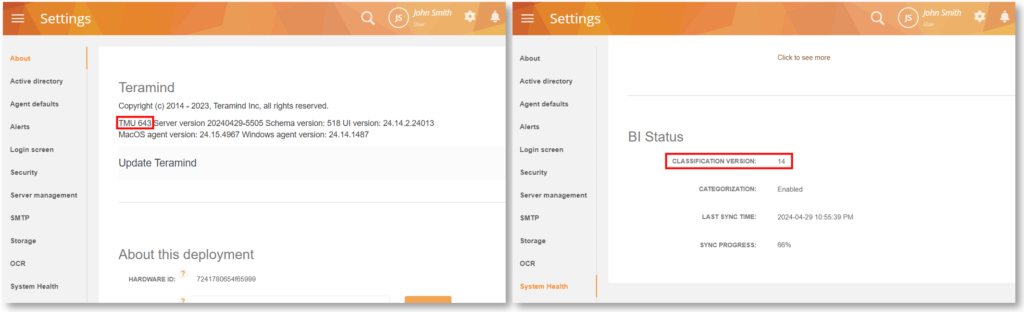
TMU and BI Classification Version
On the On-Premise deployments, the Settings > About screen will now show the TMU (platform release) version, and the Settings > System Health screen will show the BI classification version. This will help admins keep track of what versions of the packages are installed.
Support for Self-Signed Certificate with AWS RDS
Previously, if you tried to use a self-signed certificate with your AWS RDS deployment, you would get an error because Teramind didn’t support it. Now, you will be able to use a self-signed certificate with your AWS RDS deployment.
Support for Multiple History Servers
We have added support for multiple history servers in a cluster. Also implemented was load balancing support for multiple WebSocket connections. This will improve processing a large volume of history data, especially in larger deployments.