CCPA Compliance Software: Monitor, Protect, Comply
Simplify regulatory compliance and protect personal data with Teramind’s employee monitoring solution to ensure employees aren’t breaking CCPA regulations.

Why Choose Teramind for CCPA Compliance
Privacy-First Design
Our CCPA compliance software features built-in privacy controls that help organizations address CCPA regulations and meet regulatory standards while implementing privacy practices that respect the privacy of their employees’ endpoint activity.
Granular Control
Configure exactly what data is monitored, when it’s collected, and who can access it to ensure data collection processes are effectively managed. This granular control helps align data processing activities with CCPA requirements and mitigates compliance risks for your organization.
Risk Prevention
Proactively identify potential data breaches, prevent unauthorized access, and implement reasonable security measures to protect consumer data while managing third party vendors who handle sensitive information.
Key Teramind Features for CCPA Compliance
Teramind offers some of the best CCPA compliance tools to help your organization achieve and maintain CCPA compliance while protecting sensitive data through powerful monitoring capabilities.
Privacy-Friendly Monitoring
Configure monitoring to respect privacy boundaries while maintaining security visibility.
- Limit session recordings to only capture activity surrounding rule violations
- Black out screens when PII, PHI, or other sensitive personal information appears
- Disable recording for personal websites and applications
- Set monitoring schedules to properly handle personal data and protect California residents’ privacy
These monitoring features also help manage consent preferences effectively, ensuring compliance with CCPA regulations and enhancing transparency in consumer interactions.
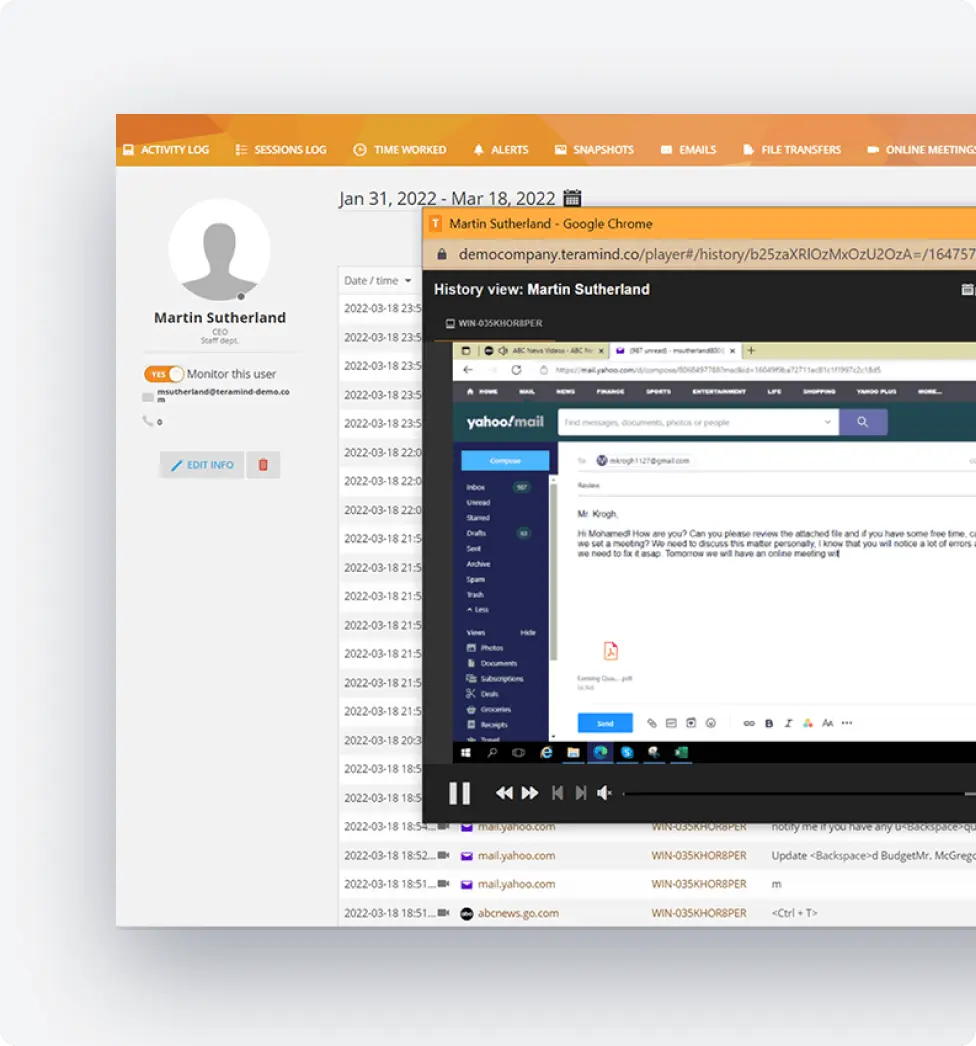
Data Loss Prevention
Ensure data security by preventing unauthorized handling of sensitive data covered under CCPA regulations.
- Block actions that could compromise security like downloading, emailing, or uploading sensitive data
- Create automated alerts when consumer data is accessed inappropriately
- Implement granular rules to prevent data exfiltration across multiple channels
- Monitor file transfers containing regulated consumer information to mitigate risks of data breaches
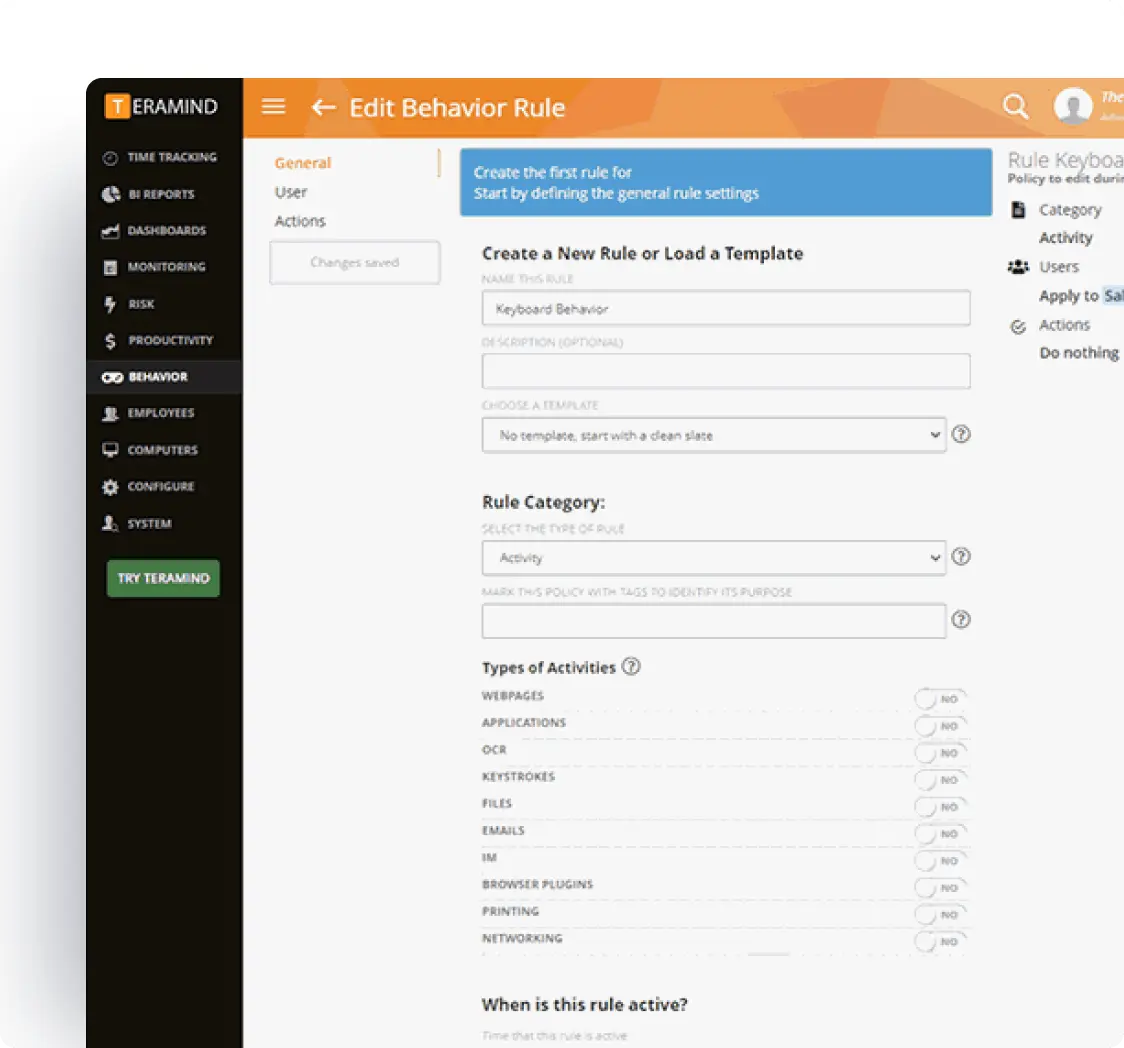
Data Classification & Discovery
Identify where personal data exists across your organization to maintain accurate data inventories.
- Discover and classify personal data across your systems automatically
- Create visual data flows to understand how consumer data moves through your organization
- Track data processing activities for compliance documentation requirements
- Implement data mapping tools that help meet CCPA compliance requirements for data transparency
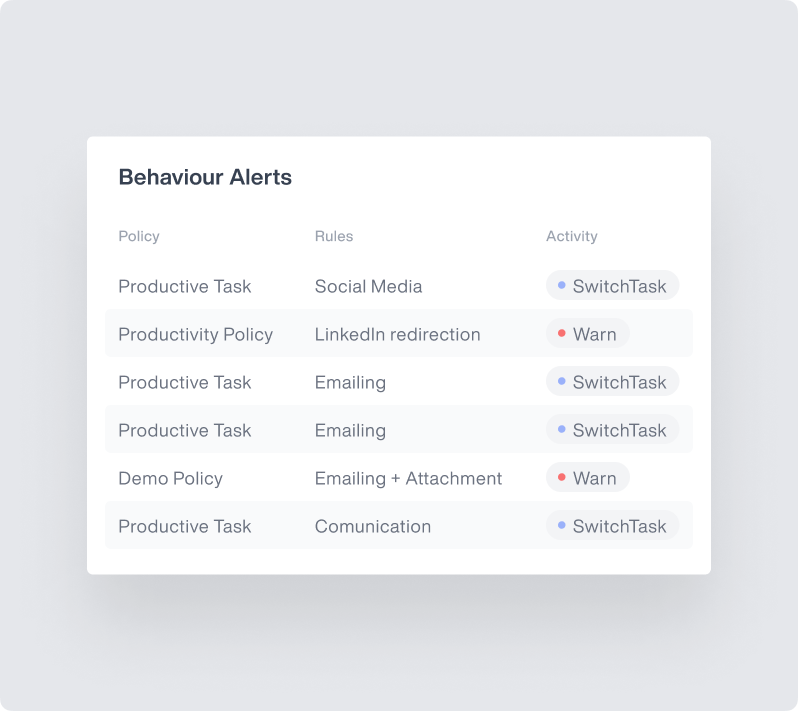
Comprehensive Audit Logs
Maintain detailed records for compliance verification and data processing transparency.
- System logs provide evidence for compliance audits required by privacy laws
- Track all administrator activities through detailed audit trails
- Document data processing activities as required by CCPA regulations
- Generate reports that help demonstrate compliance with regulatory standards
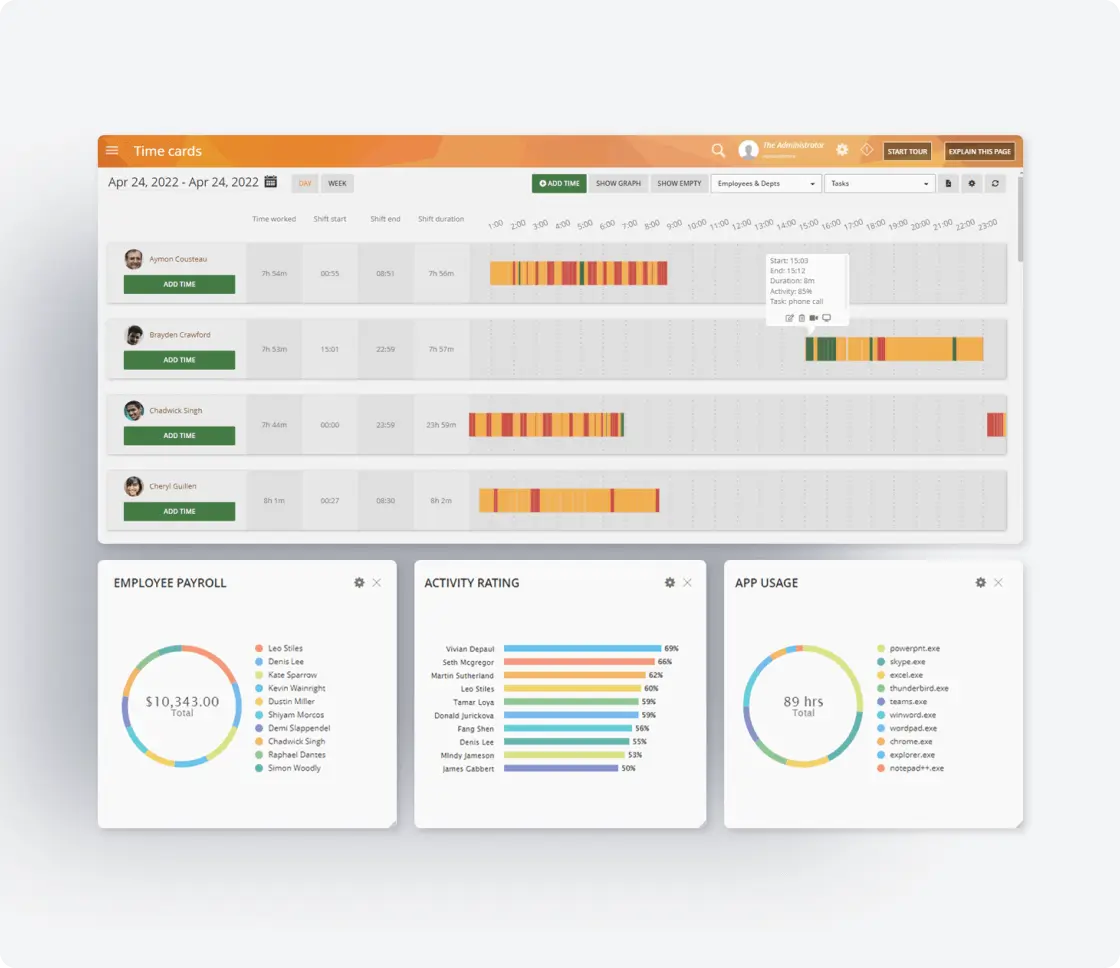
Compliance Reporting
Generating reports is crucial for internal audits and regulatory inquiries to demonstrate CCPA compliance.
- Document your compliance efforts with detailed activity reports
- Track potential compliance risks to demonstrate proactive privacy management
- Monitor trends in data access and usage across your organization
- Generate reports that demonstrate implementation of reasonable security measures as required by CCPA
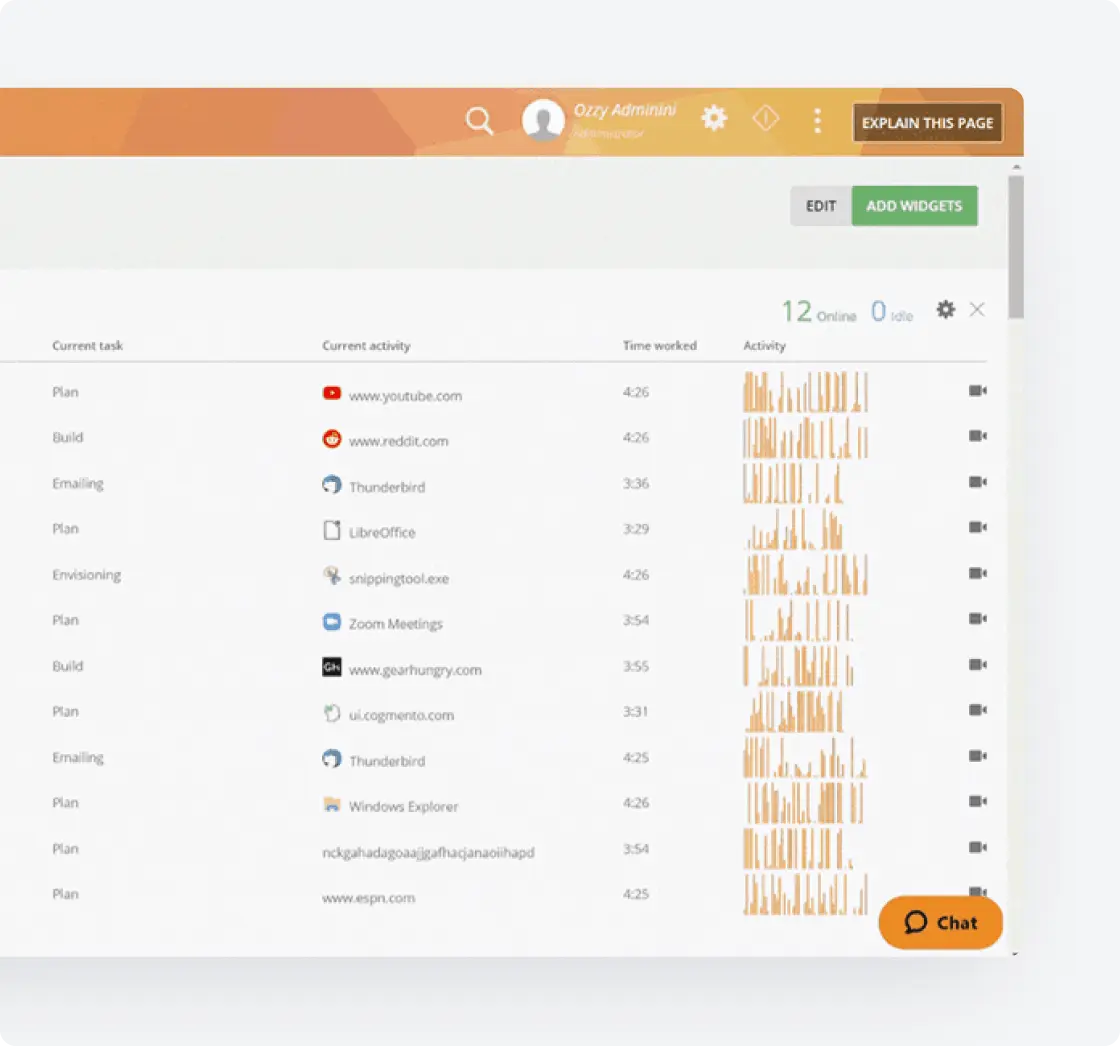
Security Rules and Policies
Create customized security policies tailored to your specific CCPA compliance needs.
- Develop rules to identify and protect various categories of personal data
- Automatically enforce data handling policies across your organization
- Create custom compliance playbooks using automated blocking and alerts
- Establish regulatory standards for handling consumer data throughout your business
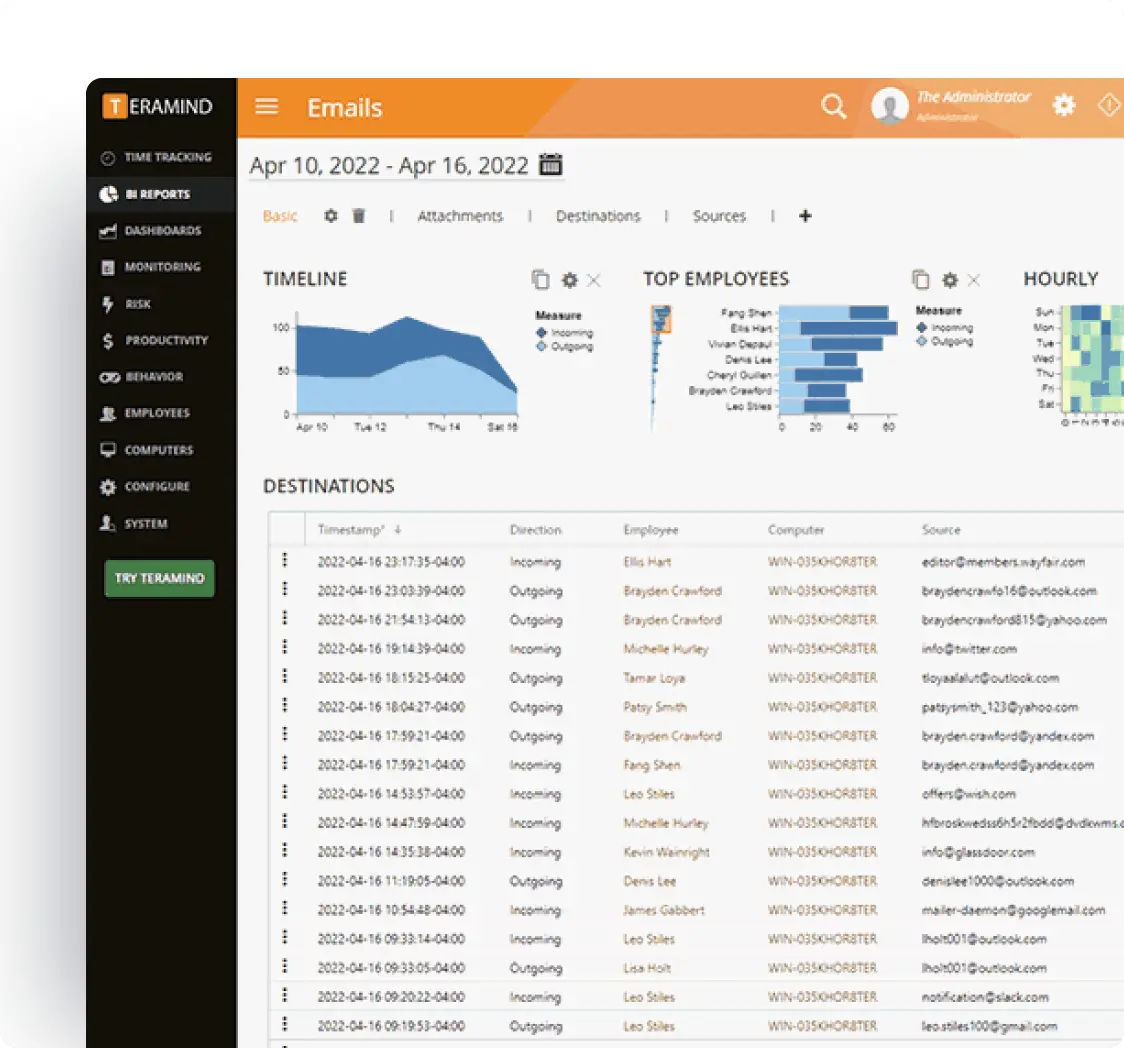
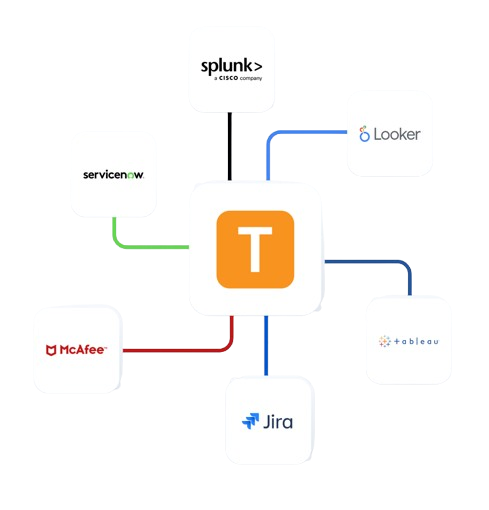
Enterprise Integrations
Integrate Teramind with your existing security infrastructure to enhance CCPA compliance monitoring.
- Integrate with leading SIEM solutions like Splunk, ArcSight, and QRadar to centralize security event monitoring
- Connect with SOAR platforms to automate incident response for potential data privacy violations
- Leverage Common Event Format (CEF) for standardized security event reporting
- Enhance existing security tools with Teramind’s detailed user behavior analytics
Teramind's Core Features
Leverage Teramind’s unparalleled power to solve your workforce challenges.
Live View & Historical Playback
Monitor employee screens in real-time or review past activity with historical playback to gain complete visibility into user activity and computer activity.
Optical Character Recognition
Teramind’s OCR functionality allows you to extract text from images and screenshots, enhancing your monitoring and analysis capabilities.
Website
Monitoring
Track employee time spent on websites, identify unproductive web browsing, and enforce company policies with comprehensive website monitoring.
Application
Monitoring
Monitor application usage, track time spent on specific apps, and identify potential security risks with detailed application monitoring on your endpoints.
Email
Monitoring
Monitor employee emails to prevent data leaks, ensure compliance with company policies, and protect sensitive information.
Instant Message Monitoring
Track instant messages and conversations to gain insights into team communication and collaboration, and ensure compliance.
Social Media Monitoring
Monitor social media activity to protect your brand reputation, prevent data leaks, and ensure employees adhere to company policies.
Network
Monitoring
Gain visibility into network activity, identify potential security threats, and optimize network performance with network monitoring.
Citrix
Monitoring
Monitor employee activity within Citrix environments, track application usage, and ensure data security with specialized Citrix monitoring on your devices.
Remote Desktop Control
Take control of remote employee computers in real-time to provide support, troubleshoot issues, or prevent data breaches and insider threats.
RDP Session Recording
Record RDP sessions to gain a comprehensive understanding of user activity, troubleshoot technical problems, and ensure compliance.
Productivity
Analysis
Analyze employee productivity with detailed metrics, identify areas for improvement, and boost productivity across your team members.
Active Vs. Idle
Time Logs
Track active and idle time to understand how employees spend their work hours and optimize time management and productivity.
Unproductive Work
Time Analysis
Identify unproductive work time, analyze patterns, and implement strategies to improve efficiency and time management.
Try Platform
With a Live Demo
to see how it works.

What our Customers Say
“The interface and reporting capabilities of Teramind remain unmatched compared to other products we have tried. Overall, Teramind is far more advanced than other competitors. They are definitely raising the bar and I’ll back them up any day.”
Ricky H.
Government Administration
“It’s been an amazing experience and a wonderful software that does exactly what you want! Security, control, peace of mind, the ability to know all that is going on in the organization. Very easy to use. It gives you real data! It has given us the protection that we need!”
Rene H.
Head IT Security
“This software has allowed us to save from a potential data breach and being able to catch people leaving who tried to take our IP. Very good software. A bit on the expensive side but worth every penny. Functionality is easy to get around. Has a great GUI.”
Milena L.
IT Manager
FAQs
What is the CCPA compliance program?
The CCPA compliance program refers to the set of policies, procedures, and technical measures an organization implements to meet California Consumer Privacy Act requirements. A streamlined compliance process is crucial in this context, as it simplifies the navigation through complex regulations and ensures that organizations meet legal requirements more efficiently. This includes establishing processes for handling consumer rights requests, implementing reasonable security measures to protect consumer data, maintaining accurate data inventories through data mapping tools, and ensuring proper management of opt-out requests. A comprehensive CCPA compliance program helps organizations mitigate risks of non-compliance while demonstrating commitment to privacy practices.
What is CCPA in software?
CCPA in software refers to specialized CCPA compliance tools and compliance software designed to help organizations protect personal information and meet regulatory standards. These solutions typically include features for data mapping, managing consumer requests, implementing security controls, and monitoring data processing activities. A CCPA compliance tool automates many manual processes associated with privacy compliance, helps identify sensitive personal information across systems, and provides automated evidence collection for demonstrating compliance with privacy regulations.
How much does CCPA compliance cost?
CCPA compliance can be a daunting task, with costs varying based on organization size, existing privacy practices, and current security measures. Investments typically include privacy management software ($10,000-$150,000 annually), staff training, legal consultation, and ongoing compliance efforts. While dedicated CCPA compliance solutions represent an upfront investment, they significantly reduce compliance risks and potential costs associated with non-compliance, including regulatory fines of up to $7,500 per intentional violation. Organizations must balance these costs against the substantial penalties and reputational damage that could result from data breaches or privacy violations.
How to become CCPA compliant?
To become CCPA compliant, organizations should first conduct comprehensive data mapping to understand what consumer data they collect and how it flows through their systems. The California Privacy Rights Act (CPRA) expands and amends the original CCPA, making compliance with these laws crucial for businesses to enhance consumer rights and safeguard against potential noncompliance risks. Next, implement privacy policies that inform California residents about their rights and how to submit consumer data requests. Organizations must then establish processes for verifying and responding to consumer rights requests, including access, deletion, and opt-out requests. Finally, implement reasonable security measures to protect consumer data, train employees on privacy practices, and deploy CCPA compliance software to automate compliance processes, monitor data processing activities, and generate reports for demonstrating ongoing compliance.

