Insider Fraud Detection for Every User Across Your System
Defend company and customer data against misconduct by leveraging behavior analytics to detect and prevent fraudulent activity.
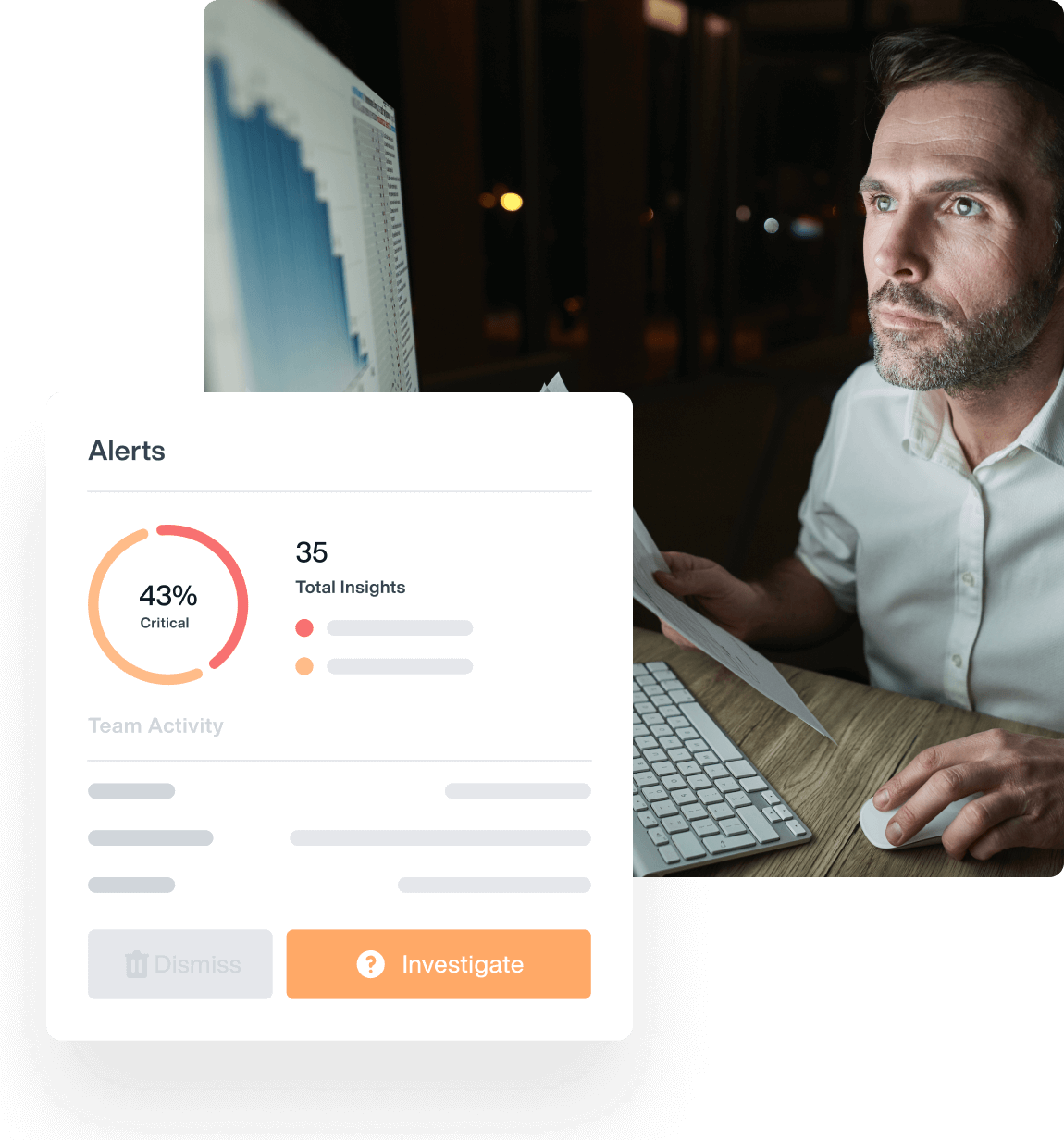
Drive Your Insider Fraud Detection Strategy
with Behavioral Data Analytics
Insider fraud is on the rise, especially
for those operating in financial services.
Teramind’s insider fraud detection solution relies on user activity monitoring, automated responses and comprehensive behavior analytics to detect the subtle signs of insider fraud and then prevent it.
Intelligent behavior analysis solutions give businesses the means to detect, prevent and protect against fraudulent activities.
How Teramind Helps
Fortify Insider Fraud Detection
Fortify insider fraud detection with continuous policy enforcement.
Teramind ensures continuous enforcement of anti-fraud measures and assists security and fraud teams in their insider fraud detection efforts.
- Create rules and policies to monitor users and enforce anti-fraud initiatives.
- Automatically notify admins, block actions or lock out users when anti-fraud policies are violated.
- Apply stricter monitoring controls for added security to data defined as sensitive & critical.
- Enforce role-based access controls (RBAC) that limit data access based on job titles.
- User risk assessments to find out if user actions are trending toward fraudulent.
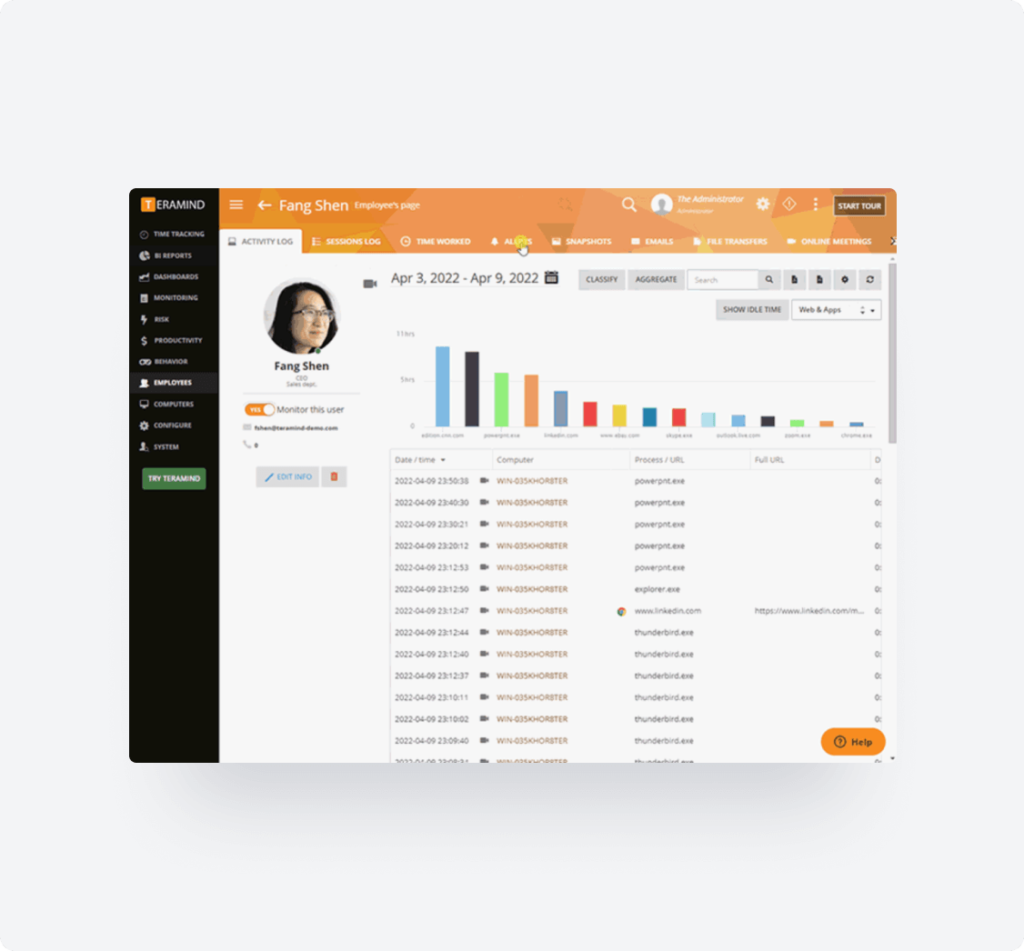
Monitor Privileged Users
Monitor those most likely to commit insider fraud: privileged users.
Protect critical data from insiders most likely to conduct insider fraud and in positions to cause the most damage–supervisors, accountants and other privileged employees.
- Track, record and log whenever customer information and accounts are accessed by users, including admins.
- Block attempts to disable fraud detection alerts or escalate privilege.
- Get automated alerts to irregular system requests like data export attempts or unauthorized data access.
- Assess the validity everyday actions that could be used for fraud like creating new accounts or loans using OCR.
- Be alerted to all actions regarding privileged data like M&A documents, credit card information or IP.
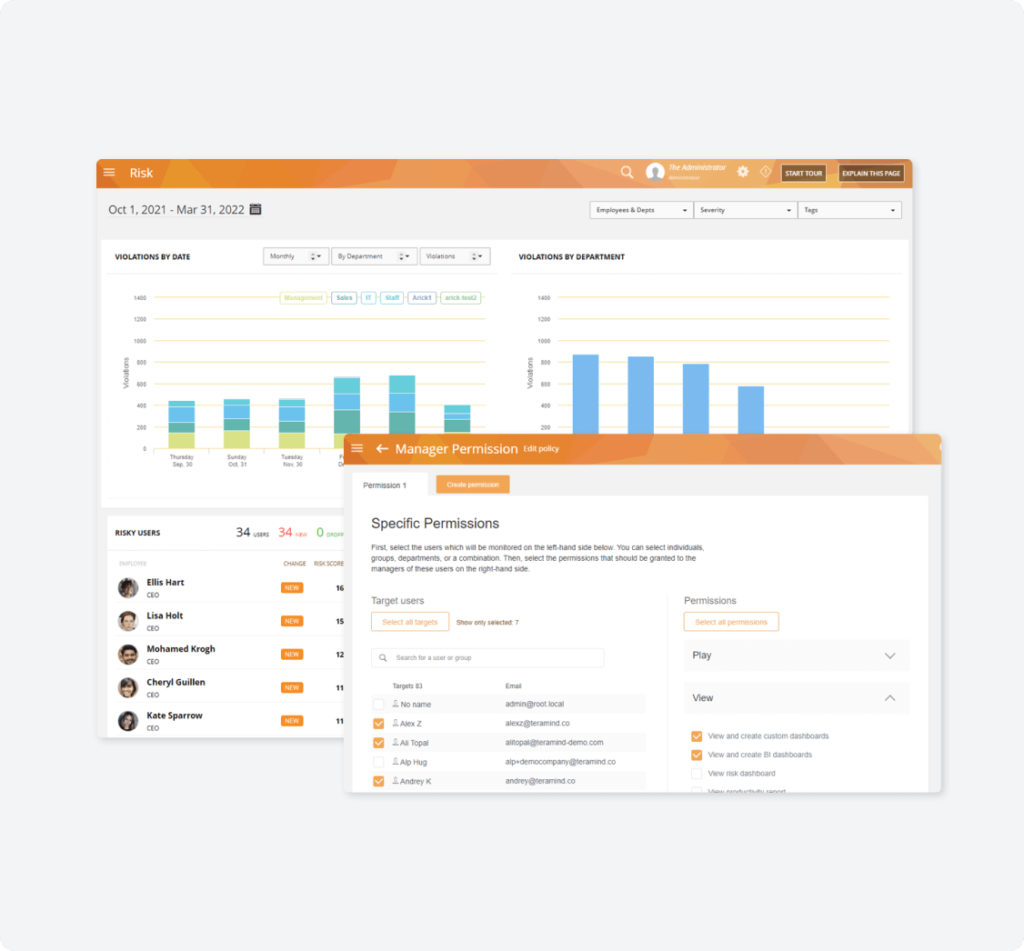
Protect company data
Protect company data that’s most at-risk for being targeted by fraudsters
Use Teramind for focused monitoring and protection of the confidential and sensitive data most at risk of being used to commit insider fraud: PII and PFI.
- Detect & block activity containing PII & PFI like clipboard operations or print screen functions.
- Use OCR search to detect if users are transferring or hiding PII or PFI in unstructured formats.
- Find out whenever users attempt to access data containing PII or PFI.
- View risk reports and assessment on users with access to PII and PFI.
- Get logs detailing user behavior surrounding PII and PFI data.
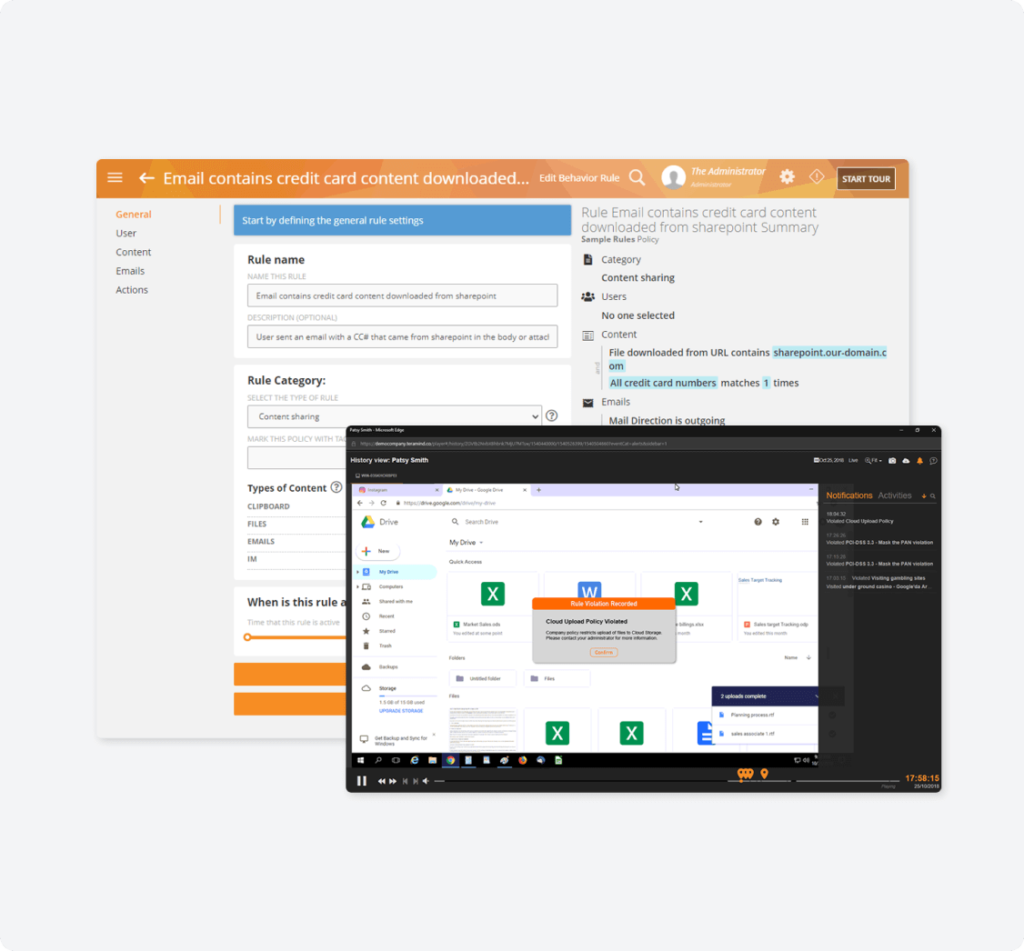
contextualized evidence
Enhance internal audits & investigations with contextualized evidence.
Teramind produces audit trails containing behavior reports, logs and analytical assessments detailing all monitored activity and actions performed by users.
- Investigate each logged activity or behavior alert with historical playback of video recorded sessions.
- Catch and watch fraudulent activity in real-time with instant violation alerts and live session playback.
- Use audit trails created to investigate and uncover trends in suspicious activity.
- View risk analysis and assessment reports built by UEBA that assist in exposing insider fraud.
- Collect irrefutable evidence of insider fraud for internal or external investigators using logs and recordings.
We bring businesses peace of mind through our award-winning insider fraud detection solution
Protect your data, manage compliance and improve productivity with Teramind.
Learn More
About Insider
Fraud Detection
Know what it is and what to look for.
What is insider fraud?
Insider fraud happens when a malicious insider, whether they’re an executive, manager, employee, contractor, vendor or partner uses their access to perform intentional data misconduct for personal gain or to conduct further criminal activity. Fraudulent insider activities include data mishandling, stealing customer and client information to organize an identity crime or stealing an organization’s intellectual property.
Insider fraud affects all industries and is most prevalent in sectors that handle personal information and have high transaction rates like finance and banking, healthcare, e-commerce and charities.
How does insider fraud occur?
It can be as simple as using a company credit card for personal purchases or as complex as stealing customers’ personally identifiable information to supply an identity theft scheme.
What threats does insider fraud pose?
Insider fraud may result in financial loss, reputational damage and loss of customer trust, along with penalties and fines for failing to comply with data protection requirements.
How do you detect insider fraud?
While insider fraud detection has become increasingly difficult in today’s digital environment, anti-fraud departments and IT security can make use of modern technologies to strengthen their insider fraud detection capabilities.
Insider fraud detection entails the continuous logging, monitoring and auditing of employee actions which allow security and anti-fraud professionals to discover and investigate suspicious activities that may result in detection of fraud early on. This process can be automated with the use of AI-machine learning.
Try Platform
With a Live Demo
to see how it works.

Try Platform
With a Live Demo
to see how it works.

What our Customers Say
“The interface and reporting capabilities of Teramind remain unmatched compared to other products we have tried. Overall, Teramind is far more advanced than other competitors. They are definitely raising the bar and I’ll back them up any day.”
Ricky H.
Government Administration
“It’s been an amazing experience and a wonderful software that does exactly what you want! Security, control, peace of mind, the ability to know all that is going on in the organization. Very easy to use. It gives you real data! It has given us the protection that we need!”
Rene H.
Head IT Security
“This software has allowed us to save from a potential data breach and being able to catch people leaving who tried to take our IP. Very good software. A bit on the expensive side but worth every penny. Functionality is easy to get around. Has a great GUI.”
Milena L.
IT Manager





