Insider Threat Prevention & Detection Powered by Behavior Analytics
Protect your company from data loss caused by accidental, negligent or compromised insiders with insider threat prevention fueled by data-driven endpoint monitoring.
Teramind's Insider Threat Capabilities
Prevent Insider Threats
Prevent all types of insider threats and data loss caused by insiders.
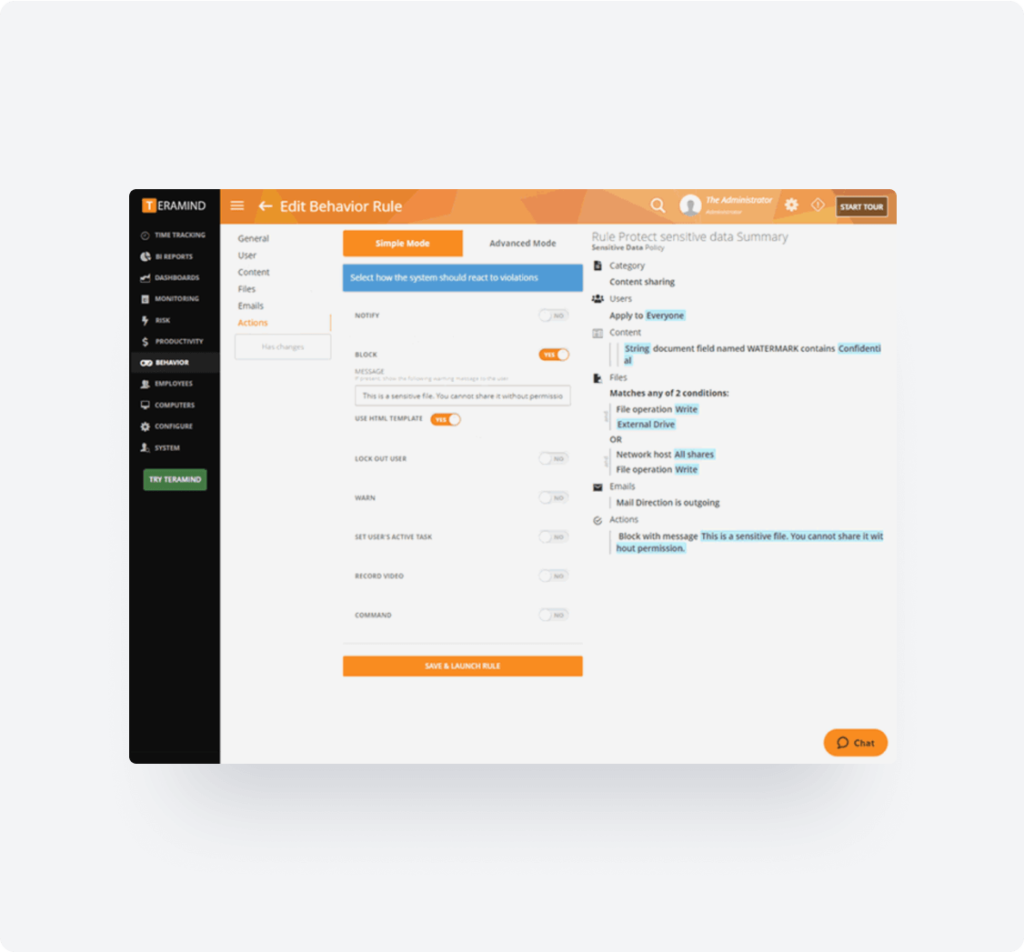
Teramind is capable of detecting insider threats and preventing them before they happen through its Behavior Rules & Alerts engine.
- Get alerted to anomalous and malicious behaviors indicative of an oncoming attack or data breach.
- Limit how company data and files are handled to prevent accidental or intentional data leaks.
- Protect your systems from malware by preventing users from falling vulnerable to phishing campaigns.
- Keep an eye on those who have the most access with access control policies for privileged users.
Detect Attacks in Real-time
Detect and thwart attacks in the moment with real-time threat prevention.
Automated & customizable responses built into Teramind stop insider threats and alert admins before an attack happens.
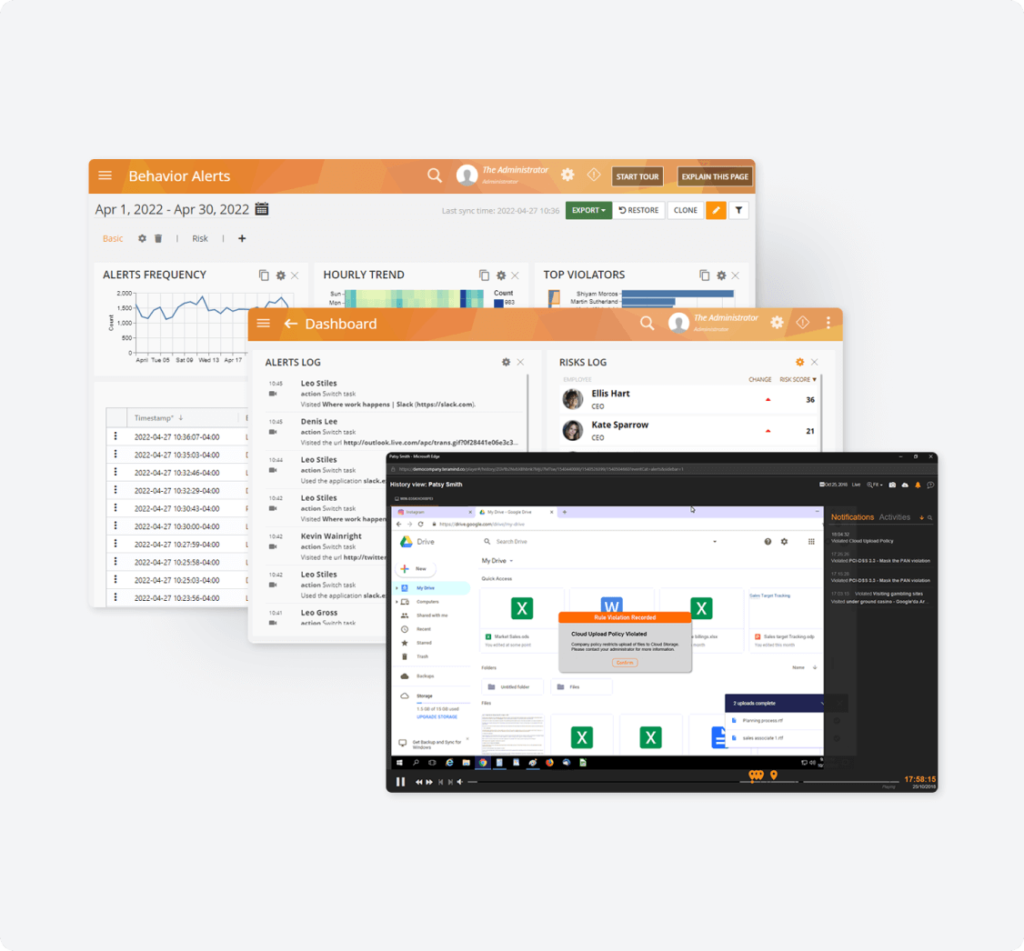
- Monitor and block email transport activities that indicate data exfiltration.
- Prohibit file uploads to anywhere including public cloud and external USB drives.
- Shut users out after-hours or when logging in from unknown sources and IP addresses.
- Intercept suspicious email activity like unprotected data sharing.
Predict Oncoming Threats
Predict oncoming threats with intelligent risk assessment.
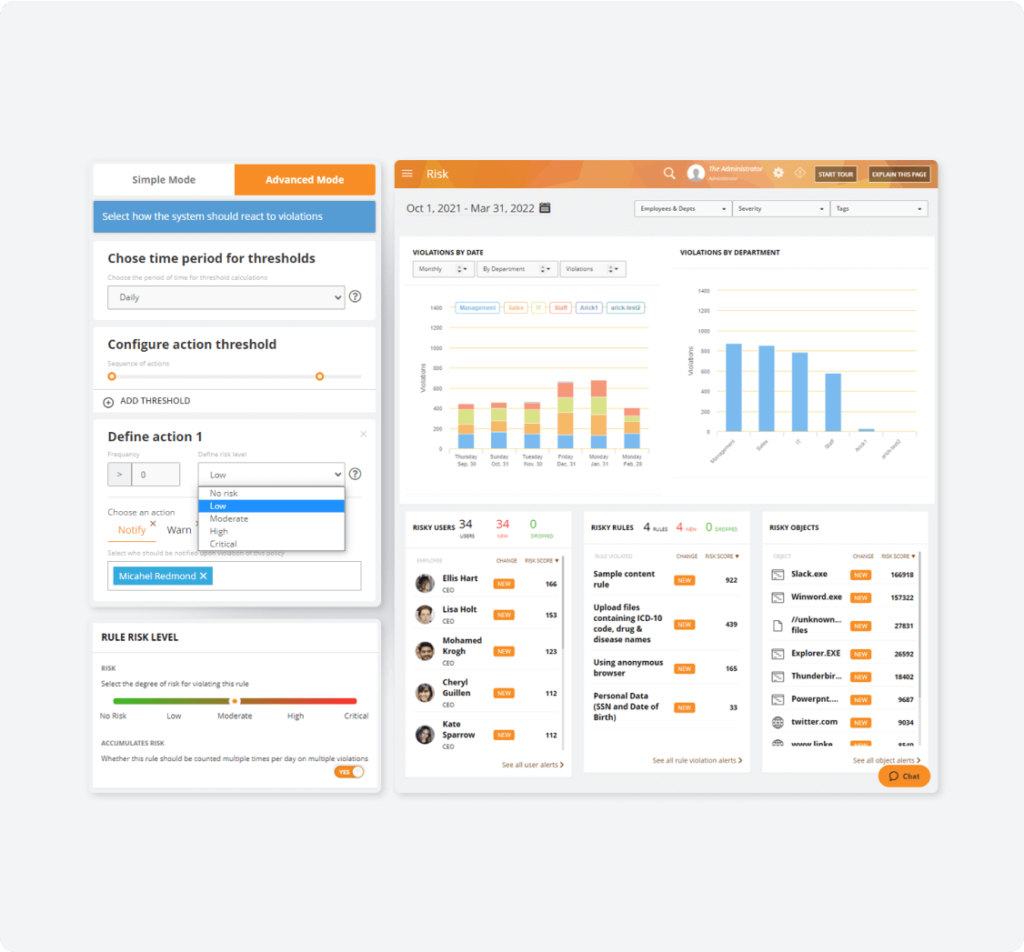
Use dynamic risk scoring to gain insights into user behavior and prevent insider threats and other potential security risks before they become critical issues.
- See all risky activity in a single dashboard and identify the organization’s biggest security risks.
- Find out if users’ risk is persistent or escalating to address growing threats to the system.
- Identify vulnerable or targeted areas based on what, when and where risky user behaviors are happening.
- Uncover anomalous, deviating behaviors indicative of insider threats.
Conduct Detailed Investigations
Conduct detailed investigations and collect irrefutable evidence.
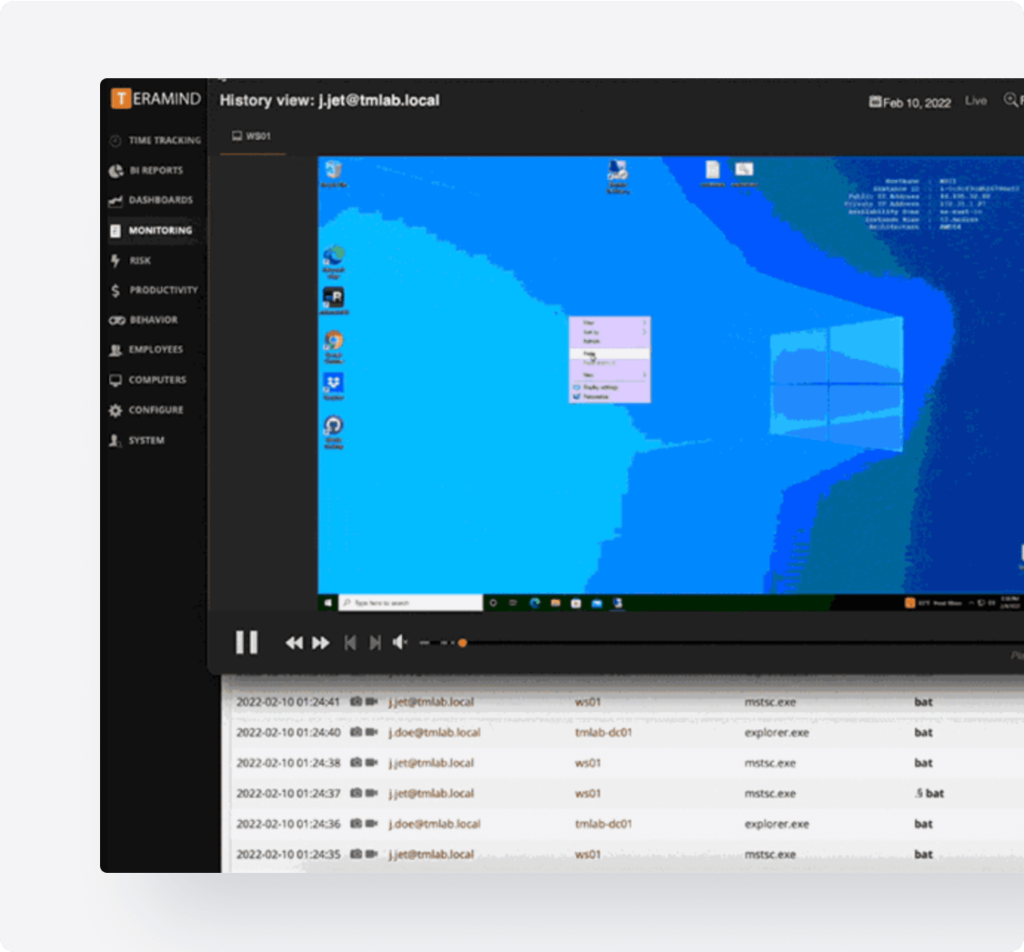
Perform detailed forensic investigations with Teramind’s forensics features like session playback and OCR to find out exactly what happened during a breach.
- See detailed timelines of user and administrative actions in immutable logs that can be used as forensic evidence.
- Watch what happened leading up to and following a rule violation or alert.
- Find stealthy activity hidden inside unstructured data with high-speed OCR search that locates unstructured content.
- Pinpoint the exact moment and location a data breach occurred with comprehensive activity reports.
What our Customers Say
Larissa H.
IT Support Specialist
Yakir D.
CIO
IT Security & Risk Manager
$7B Manufacturing Enterprise
Try Platform
With a Live Demo
to see how it works.

Try Platform
With a Live Demo
to see how it works.

Explore Teramind’s Insider Threat Prevention for 2 Key Industries Prone to Insider Threats.
Activity Monitoring for the
Healthcare Industry
Ensure consistent access to patient data and achieve compliance with user activity monitoring for healthcare.
Comprehensive Fraud and
Insider Threat Detection for Finance
Strengthen cybersecurity and insider threat detection for finance with a robust enterprise DLP endpoint monitoring solution.
Let's Get You Started
Protect your data, manage compliance and improve productivity with Teramind.
Solve for Security & Compliance with Teramind
Compliance Enforcement
Protect sensitive data and monitor the behaviors and activities of all users.
Insider Risk Management
Track and view the behaviors and activities behind your workforce.




