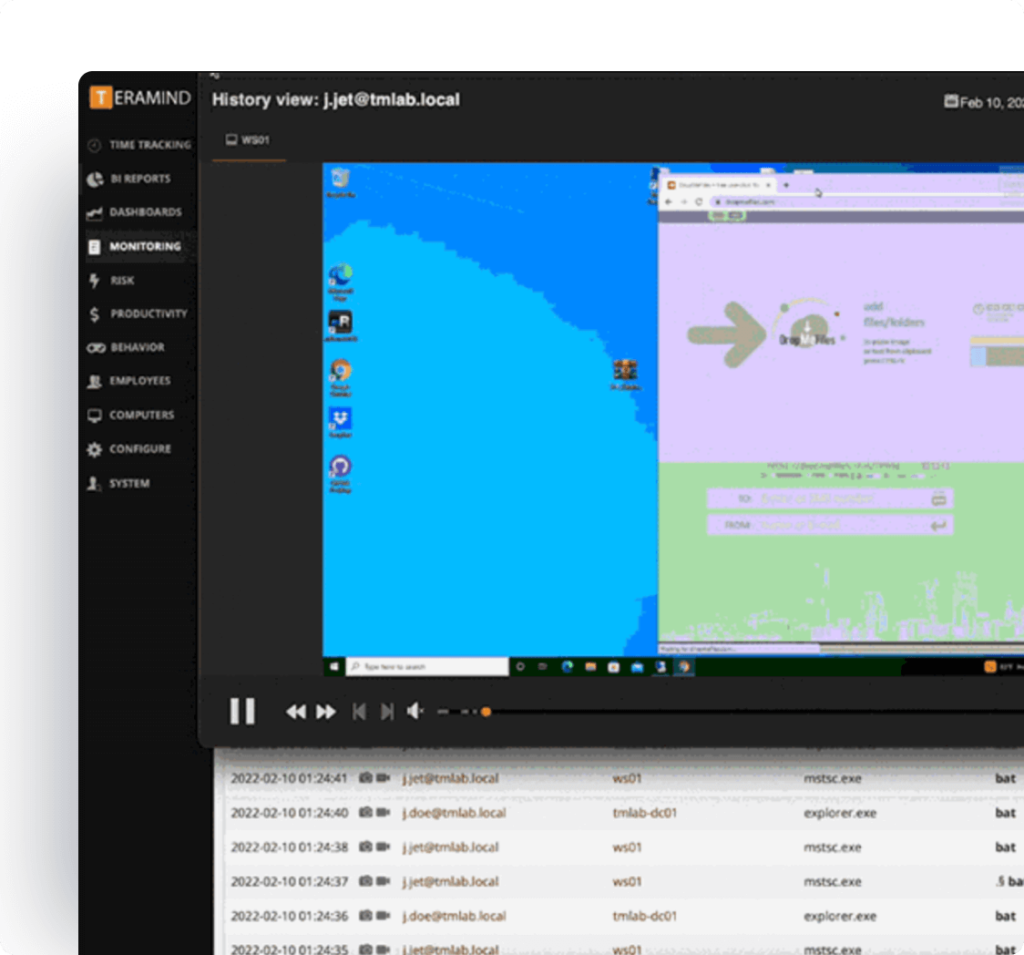
Search user sessions with Optical Character Recognition
Conduct high speed searches of any user session with optical character recognition (OCR) to find content anywhere on screen in any format.
Investigate with OCR
With the ability to search non-parsable and unstructured data, Teramind’s OCR search enriches forensic investigations and compliance audits.
- Use OCR to locate sensitive data use, combining with Live Screen Recording to see all user actions that led up to and followed the event.
- Find any instances where sensitive data is viewed, accessed, or mishandled.
- Export OCR search results and submit findings as forensic evidence for audit and data breach investigations.
High Speed
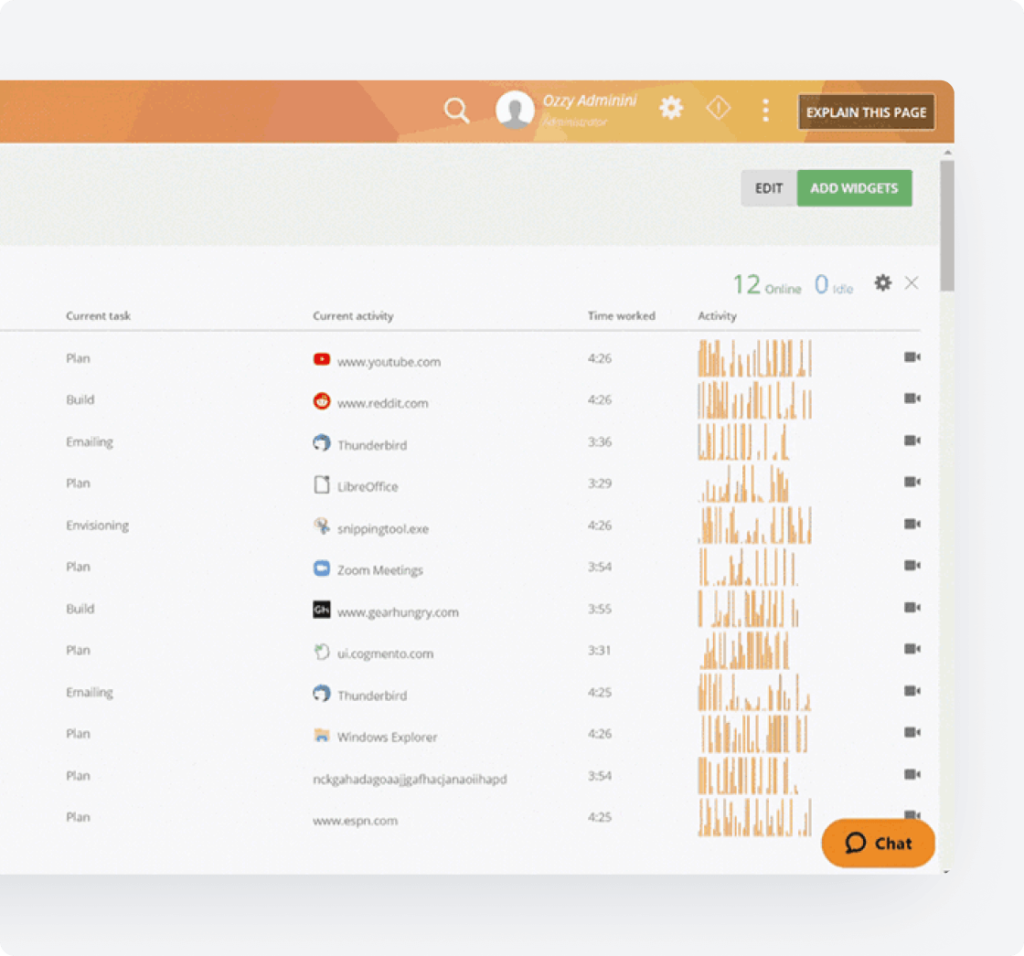
Session Mining
Search every archived and active employee session recording to find any on-screen text fast.
- Search employee and 3 rd -party contractor sessions for any specified on-screen data.
- Quickly search every recording session to identify the data or content you’re looking for.
- Make the best use of your time for collecting evidence during an investigation.
Session Recording with OCR in Action
The uses for optical character recognition are limitless.
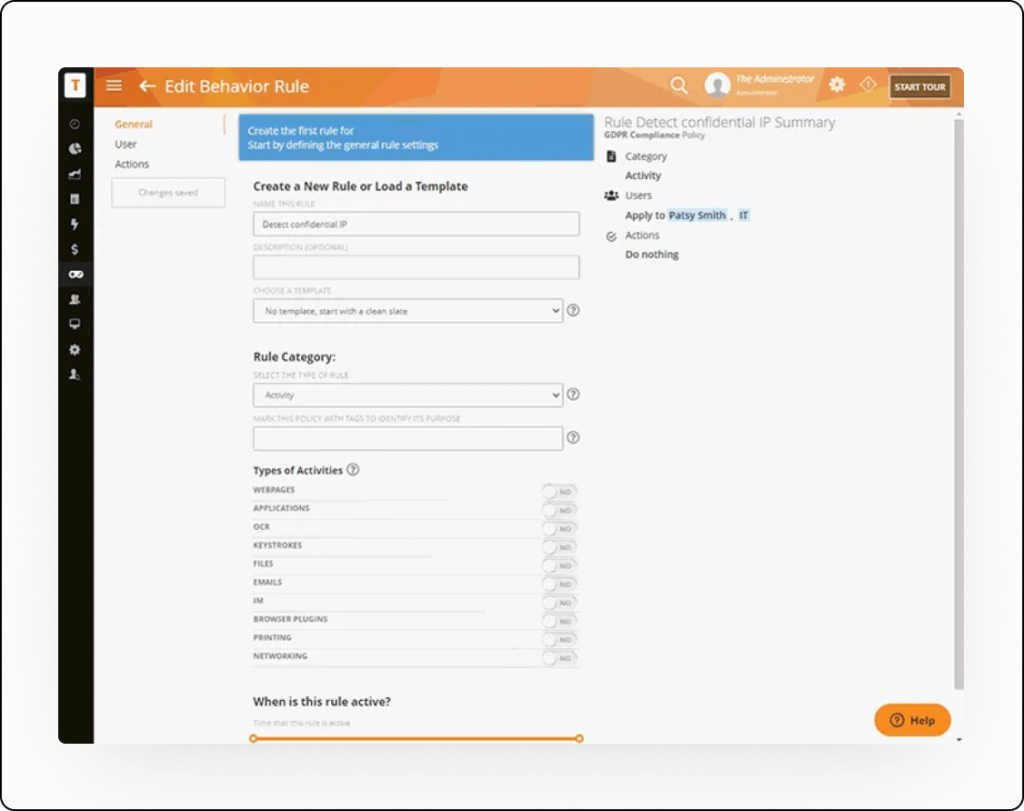
IP & Embargoed Data Protection
It’s also extremely helpful to have searchable logs when conducting internal security investigations, and combining keystroke logs with smart rules and alerting can bring violations to your attention immediately, so you can mitigate risk.
Development & Engineering
Core Teramind Features
Leverage Teramind’s unparalleled power to solve your workforce challenges.
Live View & Historical Playback
Monitor employee screens in real-time or review past activity with historical playback to gain complete visibility into user activity and computer activity.
Optical Character Recognition
Teramind’s OCR functionality allows you to extract text from images and screenshots, enhancing your monitoring and analysis capabilities.
Website
Monitoring
Track employee time spent on websites, identify unproductive web browsing, and enforce company policies with comprehensive website monitoring.
Application
Monitoring
Monitor application usage, track time spent on specific apps, and identify potential security risks with detailed application monitoring on your endpoints.
Email
Monitoring
Monitor employee emails to prevent data leaks, ensure compliance with company policies, and protect sensitive information.
Instant Message Monitoring
Track instant messages and conversations to gain insights into team communication and collaboration, and ensure compliance.
Social Media Monitoring
Monitor social media activity to protect your brand reputation, prevent data leaks, and ensure employees adhere to company policies.
Network
Monitoring
Gain visibility into network activity, identify potential security threats, and optimize network performance with network monitoring.
Citrix
Monitoring
Monitor employee activity within Citrix environments, track application usage, and ensure data security with specialized Citrix monitoring on your devices.
Remote Desktop Control
Take control of remote employee computers in real-time to provide support, troubleshoot issues, or prevent data breaches and insider threats.
RDP Session Recording
Record RDP sessions to gain a comprehensive understanding of user activity, troubleshoot technical problems, and ensure compliance.
Productivity
Analysis
Analyze employee productivity with detailed metrics, identify areas for improvement, and boost productivity across your team members.
Active Vs. Idle
Time Logs
Track active and idle time to understand how employees spend their work hours and optimize time management and productivity.
Unproductive Work
Time Analysis
Identify unproductive work time, analyze patterns, and implement strategies to improve efficiency and time management.
Request Your
Custom Demo Now
What our Customers Say
Larissa H.
IT Support Specialist
Yakir D.
CIO
IT Security & Risk Manager
$7B Manufacturing Enterprise


